In a recent release, Microsoft has provided an extensive analysis of a relatively obscure yet highly dangerous threat actor.
In their report, Microsoft has designated this group as “Octo Tempest.” They describe Octo Tempest as a financially motivated, native English threat actor, possessing extensive expertise and an utter lack of scruples.
Octo Tempest’s genesis dates back to early 2022, primarily focusing on activities like selling SIM swaps and pilfering accounts held by individuals with substantial cryptocurrency holdings. However, over the course of a few months, their scope expanded significantly. They began employing tactics like phishing, social engineering, and resetting a substantial number of passwords for compromised service providers. Their objective in these campaigns was to amass sensitive data.
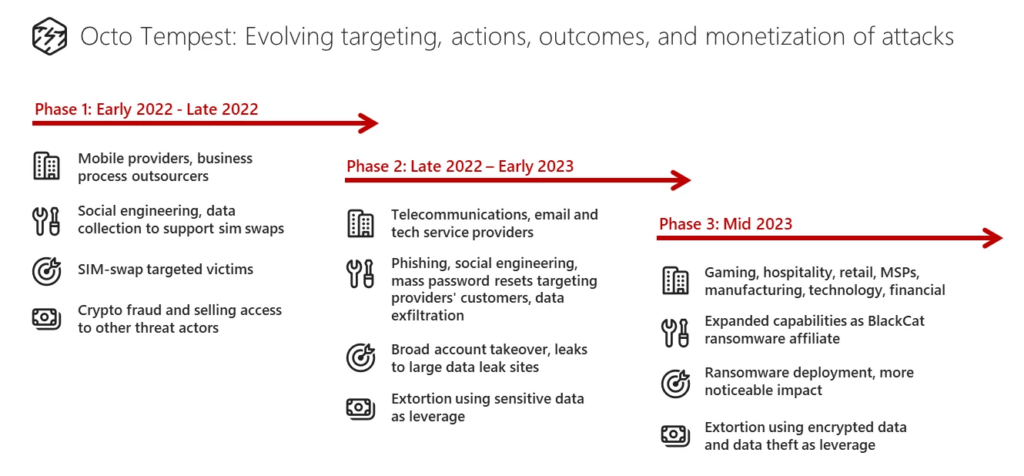
Moreover, Octo Tempest forged an affiliation with BlackCat (also known as ALPHV), a notorious ransomware-as-a-service provider. They even started deploying encryptors on the endpoints of their victims. This alliance was particularly unexpected since BlackCat isn’t known for collaborating with native English-speaking criminals.
Octo Tempest predominantly targets organizations in various sectors, including gaming, hospitality, retail, manufacturing, technology, and finance. Occasionally, they also set their sights on managed service providers (MSPs).
The group employs extreme measures to gain initial access to their target’s network, including threats of physical violence. In some instances, chat logs have revealed the attacker’s threat to send a shooter to the victim’s residence to harm their spouse.
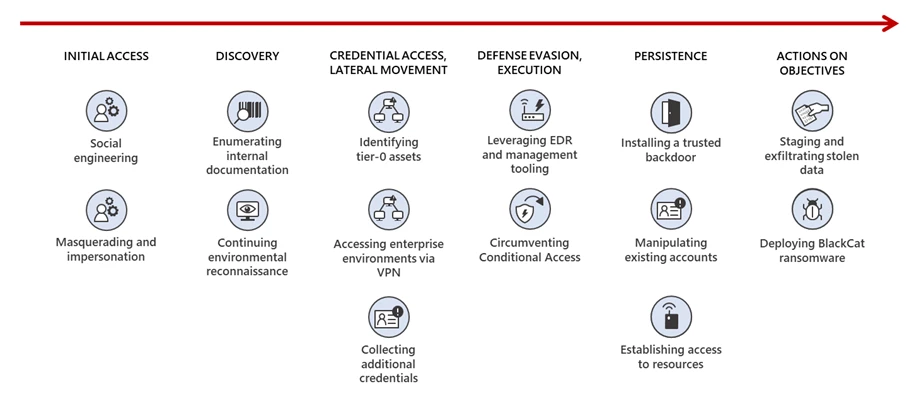
Once initial access is secured, Octo Tempest aims to expand their influence while maintaining a low profile to avoid raising suspicion. They have been observed suppressing alerts related to changes and altering mailbox rules.
The ultimate objective of Octo Tempest is to either steal cryptocurrencies, sensitive data, or extort money from their victims through ransomware. For the comprehensive report, you can refer to the following link.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






