
The BlackCat ransomware operators have proven to be a formidable adversary, consistently adapting and innovating their malicious activities. Their relentless evolution in the realm of ransomware has made it increasingly challenging for cybersecurity experts to mitigate their threats effectively.
Unveiling the Munchkin Update
In a recent development, BlackCat operators introduced an update known as “Munchkin” that enhances their ability to propagate their malicious payload across victim networks. This strategic move highlights the group’s commitment to staying ahead of security measures. The evolution of their ransomware tooling has been an ongoing process spanning the past two years.
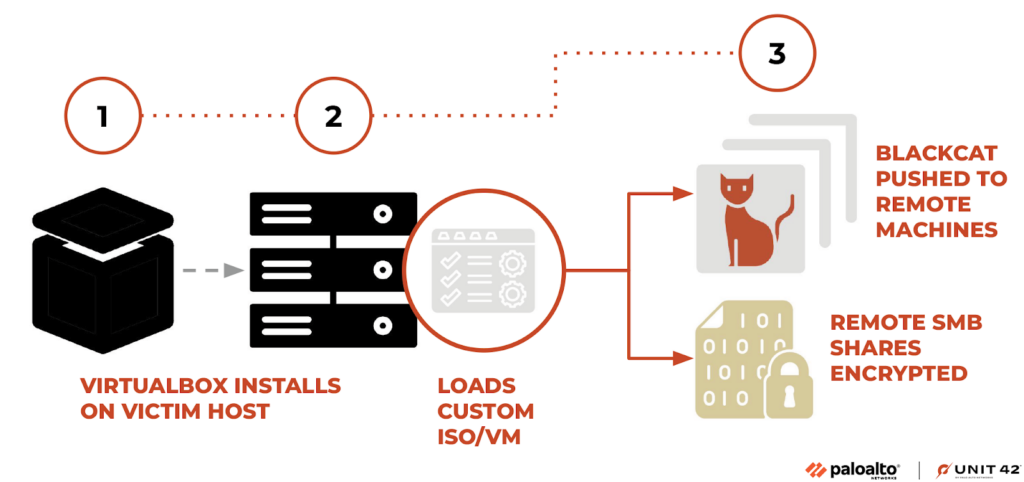
Cybersecurity researchers at Unit 42 of Palo Alto Networks recently made a significant discovery related to BlackCat’s activities. They obtained a unique instance of Munchkin, loaded within a customized Alpine Virtual Machine (VM). This finding underlines a growing trend among ransomware threat actors who are turning to VMs as a means to evade security solutions during malware deployment.
BlackCat’s evolution over time involved several key strategies to enhance its security and resilience. They focused on obfuscating configurations and employing command-line parameters, adding layers of complexity to their operations.
Unveiling the ‘Munchkin’ Tool
The latest addition to BlackCat’s arsenal is the ‘Munchkin’ tool. This tool leverages a Linux-based operating system to execute BlackCat on remote machines and encrypt SMB/CIFS shares effectively. What’s intriguing is the method used to deploy Munchkin. It arrives as an Alpine OS-loaded ISO file, which is executed through VirtualBox due to its compact nature. Once initiated, the malware takes several steps, such as modifying the VM’s root password, initiating a new terminal session with tmux, running the ‘controller’ binary, and ultimately shutting down the VM.
Anatomy of the Controller Malware
The core of the Munchkin tool, also referred to as the controller malware, resides within the /app directory. This directory includes several key files and scripts, each playing a role in the malware’s operation. Notable files within this directory include:
- /app/controller
- /app/config
- /app/payload
- /scripts/smb_common.py
- /scripts/smb_copy_and_exec.py
- /scripts/smb_exec.py
The Extensive Arsenal of Python Scripts
Within the /usr/bin directory, a host of Python scripts are found, adding to the malware’s versatility and capabilities. These scripts serve various functions, including credential manipulation and exploitation. Some notable scripts in this extensive list include:
- DumpNTLMInfo.py
- Get-GPPPassword.py
- GetADUsers.py
- GetNPUsers.py
- GetUserSPNs.py
- … and many more
BlackCat’s Ongoing Adaptation
The emergence of Munchkin reflects the BlackCat ransomware operators’ continuous efforts to refine their strategies and evade security measures effectively. Their utilization of VMs to circumvent security restrictions is part of a broader trend among malware creators who remain committed to outmaneuvering the security community.
In conclusion, the cat-and-mouse game between ransomware operators and cybersecurity experts continues to intensify, underscoring the need for proactive security measures and continued vigilance in the face of evolving threats.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.





