
WHAT IS ANONYMITY
There are several levels of anonymity but the important idea behind anonymity is for a person to be non-identifiable, unreachable, or untrackable.
When anonymity is considered, privacy is often assumed.
And while privacy and anonymity (and even security) are interwoven concepts, privacy is not synonymous with anonymity.
ANONYMITY DOES NOT EQUAL PRIVACY

Privacy primarily involves you controlling who sees what activities you engage in online. Other people may know who you are, but not what information or websites you access or seek out. Privacy relates to the content. If you send an encrypted email to a friend so only the two of you can open it, this is private. But other entities can potentially know who sent the email to whom. Thus privacy does not always mean anonymity.
WHY BE ANONYMOUS
I just heard you saying: “I don’t care to be anonymous, I have nothing to hide”. You don’t have to be involved in anything illegal if you seek anonymity online. The main reasons on why anonymity online is important follow.
Freedom of speech
People must be able to express themselves online on social media, content sharing websites, blogs, or in comment sections without the fear of being criticized or facing consequences like losing their job. In the United States of America, the Supreme Court has ruled repeatedly that the right to anonymous free speech is protected by the First Amendment.
Personal safety
Using online anonymity you can worry less about your personal safety as a result of your online actions. You shouldn’t be afraid that someone can find out your location or where you live, if you dont want to of course, and come after you to inflict physical injury.
Data Protection
Being anonymous online help you protect sensitive data like your personal, and credit card information from malicious actors. Hackers come after such information and then sell them to other malicious actors on the dark web. On several occasions these data are stolen from companies to which you trust your data for specific purposes, like a service offering, so think again when you do so.
TOOLS TO HELP YOU REMAIN ANONYMOUS ONLINE
Use a VPN
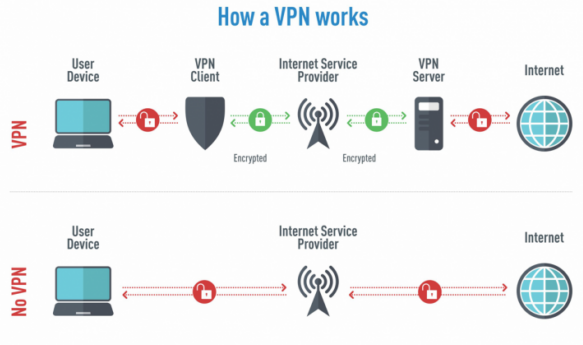
There are numerous VPN providers that you can use and can help improve your online anonymity by hiding your real IP address and encrypting your data transmissions.
Browse with Tor
Tor browser is becoming increasingly popular with the average user. It offers anonymity and a path through Internet censorship and monitoring. Tor is by no means the perfect tool for anonymity online. It has its flaws and it is quite slow but if you want to browse as anonymously as possible you should give Tor a try.
Install and Use Whonix
Another layer to your online anonymity effort is the use of Whonix Gateway and Workstation. Each is a Linux VM you can run on virtualization engines of your choice. You as a user will connect to Whonix Workstation which will use Whonix Gateway as its internet gateway, leveraging the Tor networks capabilities, thus keeping your real IP address as well as your online actions are hidden. Using the Whonix VMs also gives you another layer of protection from websites with malicious code since your actual, the physical machine cannot be compromised, (at least not so easily).
Search The Web With DuckDuckGo
When it comes to online anonymity the search engine of choice is DuckDuckGo. This search engine hopes to get some of your Google searches by promising not to use cookies to follow you online and do not collect any personal information. They claim to even protect your search history even from them!
Dont Use Social Accounts to Login to Other Sites
Avoid logging into other websites with your social media accounts. This way both the website will get more information that you need it to and the social media company will be able to track more of your actions and gather more information about your online presence.
Use alternative email services
Use email services that are designed for anonymity and privacy. Some of the best and with generous free plans out there are:
If you only need to send an anonymous email but don’t need to receive a response, the best choice is to use a one-way anonymous email platform. There are plenty to choose from: some of them will allow you to use the recipient’s public PGP key to encrypt your message while others will send you read and received receipts while keeping your identity completely hidden. Try AnonymouseMail, CyberAtlantis, 5ymail, or W3 Anonymous Remailer.
Use an Ad Blocker
Everything you do online—from browsing to shopping to using social networks—is tracked, typically as behavioral or advertising data. Browser extensions are simple, generally free add-ons that you can use to slow down or break this type of data collection, without completely ruining your experience of using the internet.
Use Signal
Signal is the best encrypted messaging app that let you send text messages and voice memos as well as voice calls and audio calls. Its easy to use and offers more anonymity than any other app.
CONCLUSION

Anonymity online is not easily achievable. You have to be constantly aware of your actions and use different tools and practices which sometimes are not practical for our day to day online lives. Sure, most of us have our Gmail, we Google search and we scroll on our favorite social media, but let us be aware that:
when something online is free, YOU are the product!
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






