Penetration testing is an important part of security for any organization that handles sensitive information. It helps ensure that systems are secure against attacks by hackers and other malicious actors.
NIST Publications on Penetration Testing
Penetration testing is the method by which the security of an application, computer system, or network is tested by simulating attacks from malicious actors.
By performing penetration testing, your organization can identify the attack vectors the malicious actor can utilize to attack you, the vulnerabilities, and security control weaknesses that he/she can exploit to compromise the data, application, or any other environmental resources.
The results of a pentest can provide valuable insights and help your organization to develop plans to address cybersecurity risks.

Many times though, unfortunately, the penetration testing exercise is conducted only to satisfy a regulatory requirement and is considered merely a compliance task by the management.
NIST Standards Referencing Penetration Testing
NIST is a well-known foundation in the IT sector that created many guidelines and standards. These standards even though created for US federal agencies and their contractors, many private organizations choose to adopt them to improve their cybersecurity posture.
Penetration Testing is mentioned in several of NIST’s publications
- NIST Special Publication (SP) 800-115: “TECHNICAL GUIDE TO INFORMATION SECURITY TESTING AND ASSESSMENT” references and describes penetration testing under 5.2 along with four penetration testing phases, planning, discovery, attack and reporting.
- NIST SP 800-95: “Guide to Secure Web Services” states that software security testing should include security-oriented code review and penetration testing.
- NIST SP 800-137: “Information Security Continuous Monitoring for Federal Information Systems and Organizations“, under Penetration Testing from NISTIR 7298, refers to penetration testing as a test methodology in which assessors, using all available documentation (e.g., system design, source code, manuals) and working under specific constraints, attempt to circumvent the security features of an information system.
- NIST SP 800-152: “A Profile for U.S. Federal Cryptographic Key Management Systems” under Security Assessment and 11.1.4 states that penetration testing shall be performed as part of the security assessment of Federal Cryptographic Key Management Systems (FCKMS).
- NIST SP 800-160: “Systems Security Engineering” references penetration testing as the means to test that the required protection is delivered across all defined system modes and states.
- NIST SP 800-53 Rev. 5: “Security and Privacy Controls for Information Systems and Organizations“. This publication aims to help organizations identify the security and privacy controls needed to manage risk and to satisfy the security and privacy requirements.
NIST 800-53 Security Control for Penetration Testing
You see that many NIST publications reference penetration testing but none is as comprehensive as NIST 800-53.
The NIST SP 800-53 has a list of security controls organized in different families, each of which organizes these controls into common, necessary groupings based on their application.
One of these families of controls, the Assessment, Authorization and Monitoring (CA) contains a series of controls that covers the planning, implementation, and continuous monitoring of policies and security systems.
Its focus is on demonstrating an organization’s ability to assess and continually track vulnerabilities as they emerge due to external threats or internal configuration changes. One of the controls, CA-8, speaks directly about penetration testing.
NIST Control Enhancements
NIST makes 3 additional control enhancements to CA-8 to consider when conducting penetration tests.
- Utilizing independent pen testing agents: Independent testers provide, according to NIST, impartial testing, and such avoidance of conflict of interest is paramount to proper compliance.
- Red team exercises: A “red team” exercise is slightly different from a penetration test. Penetration tests typically focus on application, network, or system-level vulnerabilities to determine risk values inherent in the system. A red team, conversely, focuses on highly specific areas of attack and coordination, and will often focus on the connections between physical, administrative and technical systems. If Penetration testing is a wide net cast to catch vulnerabilities, red teams are a scalpel dismantling complex systems to find deep attack vectors. NIST CA-8 suggests using red team techniques to inform risk and control implementation.
- Facility penetration testing: NIST also requires facility-level penetration testing, including the assessment of physical environments where people access data, data centers, and workstations.
Basic Penetration Testing Structure
The general methodology suggested by NIST for the execution of the penetration test follows four stages:
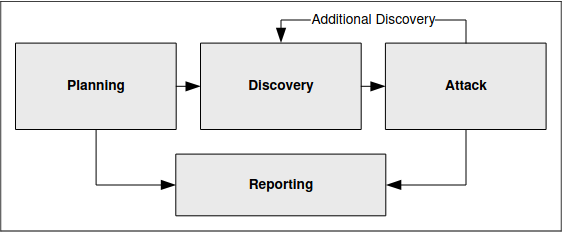
Planning
In the planning phase, rules are identified, the scope is determined, management approval is finalized and documented, and testing goals are set. The planning phase sets the groundwork for a successful penetration test. No actual testing occurs in this phase.
CA-8 suggests using vulnerability analysis so that its results can inform the penetration testing activity and make it more effective. It also outlines a basic penetration testing structure with the following steps which are mainly executed during the planning phase:
- Conducting a pretest analysis of the systems to undergo assessment, utilizing full knowledge of system organization and configurations.
- Cataloging a pretest set of known and potential vulnerabilities based on the previous analysis.
- Designing tests specifically to exploit known and potential vulnerabilities to determine the scope of their exploitability.
- Crafting agreements regarding the conduct, scope, and scale of the penetration test from both testing and tested parties.
- Coordinate testing procedures and techniques in ways that correlate with real-world threats and technologies.
- Mapping of privacy and security laws that could impact the unauthorized disclosure of data during the test and taking steps to mitigate any unintentional data breach.
Discovery
The discovery phase of penetration testing includes two parts. The first part is the start of actual testing and covers information gathering and scanning. Network port and service identification is conducted to identify potential targets.
Techniques like hostname, IP address, application, and services information gathering as well as employee names and contact information gathering are part of the discovery phase.
Attack (which feeds more discovery actions)
Executing an attack is at the heart of any penetration test and represents the individual steps of the attack phase—the process of verifying previously identified potential vulnerabilities by attempting to exploit them.
Reporting
The reporting phase occurs simultaneously with the other three phases of the penetration test. In the planning phase, the assessment plan, commonly called the “Rules of Engagement” is developed. In the discovery and attack phases, written logs are usually kept and periodic reports are made to system administrators and/or management.
Conclusion
Whether you follow NIST’s methodology to conduct a penetration test for your organization or wish to choose another framework, what is most important is that you inherit a structured approach. Proper planning is crucial and you may need more time allocation to the planning phase than you may think.
What will you gain from regular penetration tests?
Identify and prioritize risks. You will understand what security controls are necessary to enhance your organization’s security needed to protect your people and assets.
Prevent malicious actors from infiltrating your systems. Performing regular penetration tests allows you to be proactive in your real-world approach to evaluating your IT infrastructure security. The process uncovers holes in your security, giving you a chance to properly remediate any shortcomings before an actual attack occurs.
Avoid security incidents, which will harm your business operations and cause financial and reputation harm.
Be compliant. With regular penetration testing exercises, you will be able to demonstrate due diligence and dedication toward information security. This will help address the compliance and security obligations that are mandated by standards and regulations like PCI and ISO27001.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.





