Cybersecurity has become increasingly popular in the last decade. It has seen great interest from technical and non-technical people wanting to take their opportunity in the field.

Security breaches bring more attention to the importance of Information Security and Cybersecurity to the public, increasing demand for training and certification.
But what are the steps one can take to become an expert in Cybersecurity?
Expert – An expert is someone who has broad and deep competence in terms of knowledge, skill, and experience through practice and education in a particular field. (Wikipedia)
Getting into my practical advice on how to acquire the skill, knowledge, and experience..
- Programming
- Networks
- Operating Systems
- Web Applications
- Containers
- Cloud
- Tools
- Penetration Testing Methodologies
- Information Security Standards and Frameworks
LEARN PROGRAMMING
It is recommended that cybersecurity professionals learn at least one object-oriented programming language. Mastering more than one language is better, but a solid understanding of one language can aid in understanding many other languages.

In order to understand how an attacker breached a system, or how an exploit works you will need to understand the language the exploit was written on. Sometimes when being the attacker or the Penetration Tester, you will have to understand it in order to modify it to fit the needs of the system or the environment under testing.
Don’t be intimidated. You don’t actually need to learn how to create applications or exploits yourself. Don’t get me wrong, it would be very useful if you would. But this can take a lot of time and you need to learn more skills than just programming.
Learn to read code. I don’t know how much sense this makes to you, but if you know what variables, methods, or functions are then you most probably will understand what they do if you read them in a script or program. You don’t need to be a programmer to know how to read code.
Common languages used
The most common and useful languages out there to use as a basis for Cybersecurity activities are C or C++, Python, Bash, Powershell, and SQL.
LEARN HOW NETWORKS WORK
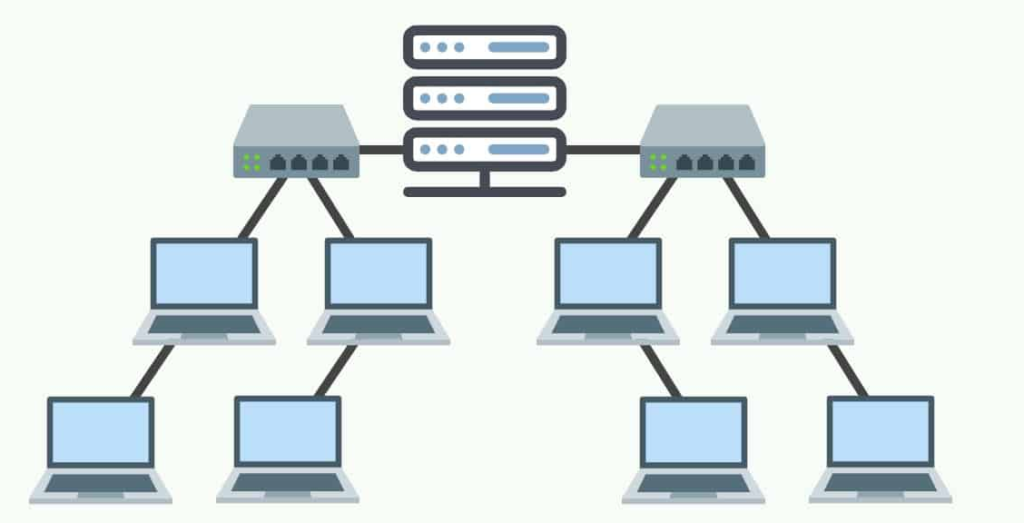
Take some training on CCNA level concepts online. Learn the basic functionality of networks, what ports and protocols, services are. If you learn the OSI Layers and what is the use and functionality of each layer you will probably know more than most “experts” out there.
Have a solid understanding of the components of a network. What a switch is, what a router does, how a firewall protects your network, how an IDS or IPS can enhance your network protection.
LEARN HOW OPERATING SYSTEMS WORK

I don’t mean clicking around to find out what the OS can do for you. Learn how an OS works, what are its components etc. You will need to get better than the average user if you want to be a better cybersecurity professional.
Don’t stick to one OS, the world is operating with at least more than 2 OSes. Windows and Linux knowledge is essential.
I recommend using the OS you are most comfortable with as your primary OS and then installing the additional OS as virtual machines on VirtualBox.
LEARN HOW WEB APPLICATIONS WORK

Web applications are very common nowadays. They are popular because provide an interface between the end user and the web servers
Web application hacking refers to the exploitation of applications which can be done by manipulating the application via its graphical web interface, tampering the Uniform Resource Identifier (URI), or tampering HTTP elements not contained in the URI.
Methods that can be used to hack web applications are SQL Injection attacks, Cross-Site Scripting (XSS), Cross-Site Request Forgeries (CSRF), Insecure Communications, etc.
The best place to start is the OWASP Top 10
LEARN CONTAINER SECURITY AND MICROSERVICE-BASED ARCHITECTURE
WHAT A CONTAINER IS
A container consists of an entire runtime environment: an application, plus all its dependencies, libraries, other binaries, and configuration files needed to run it, bundled into one package. By containerizing the application platform and its dependencies, differences in OS distributions and underlying infrastructure are abstracted away.
Container security is the protection of the integrity of containers. This includes everything from the applications they hold to the infrastructure they rely on.
A very practical way to learn container technology is deploying a small lab with a very small cost on a raspberry pi. You can set up portainer on a Pi and start creating containers on it easily. Practicing the creation, modification, and deletion of containers, images, and networks will make you understand container technology faster and easier.
You can learn more about container and docker security from this article and how to secure Kubernetes using some of the top security tools in this article.
EDUCATE YOURSELF IN CLOUD TECHNOLOGIES
Google, AWS, Azure are the dominant ones. Learn what solutions they are using to provide application, architecture, network security, and so on. There are tons of free resources to learn about their components and how they work.
You will see a lot of terminology like “NSG” and “S3 buckets” and you don’t have to just know the meaning of them, you will have to know how they function. Either to leverage their functionality to defend them, to attack them as part of a penetration test or to use them in a large design or as part of an architecture.
Click on each image for some excellent free resources you can start with:
READ ALL THE MAJOR PENETRATION TESTING METHODOLOGIES. LEARN AT LEAST TWO OF THEM.
You don’t have to be or decide to take the penetration testing path to learn about the most well-known penetration testing methodologies in the world. From System Admin, IT Security, IT Auditor, Analyst, to IT Manager, and CISO you will benefit greatly if you read and learn at least two of the best Penetration Testing Methodologies out there. You will learn proper approaches for securing systems, networks, and applications
GET SOME HANDS-ON EXPERIENCE WITH ESSENTIAL TOOLS
Download and play with these free tools to learn more about Vulnerability assessments, Web Application Penetration testing, traffic analysis, port scanning.
Nessus and OpenVAS for VA Scanning
Burp Suite and OWASP Zap for Web Application Security Testing
Wireshark for protocol and traffic analysis
Nmap for port scanning (and more)
I recommend that you download and install Kali Linux on VirtualBox. Burp Suite, OWASP ZAP, Wireshark, and Nmap are preinstalled on Kali and you can easily install Nessus and OpenVAS.
Get Familiar With Information Security Standards and Frameworks
Information security standards and frameworks help organizations manage risk.
As an expert providing services to an organization, you are expected to assess the security of an organization and then design and guide the implementation of the appropriate security controls, especially if you are pursuing positions like: Information Security Manager, Chief Information Security Officer (CISO), and similar positions.
Information security standards and frameworks will act as a blueprint helping you define and prioritize the tasks required to minimize the risk deriving from threats to your information assets. They are also essential when your organization wants to achieve compliance and pass any IT audits required.
Having knowledge and expertise in using these standards and frameworks will certainly give you the edge as a professional against people who are only technically oriented in certain areas and don’t have the capacity to provide an organization with a holistic approach to defining and managing information security programs.
Top Information Security Standards & Frameworks
ISO/IEC 27001/27002/27005 series for Information Security Management Systems (ISMS)

ISO 27001/27002 is probably the most known standard for implementing an Information Security Management System (ISMS). Getting the ISO 27001 certification means that you follow best practices and provide the assurance that information assets are protected.
ISO 27001 focuses on the requirements for the information security program and ISO 27002 is a supplementary standard that focuses on the information security controls that organizations might choose to implement. These controls are listed in Annex A of ISO 27001.
ISO 27005 describes how to conduct an information security risk assessment in accordance with the requirements of ISO 27001.
NIST Cybersecurity Control Framework (CSF)
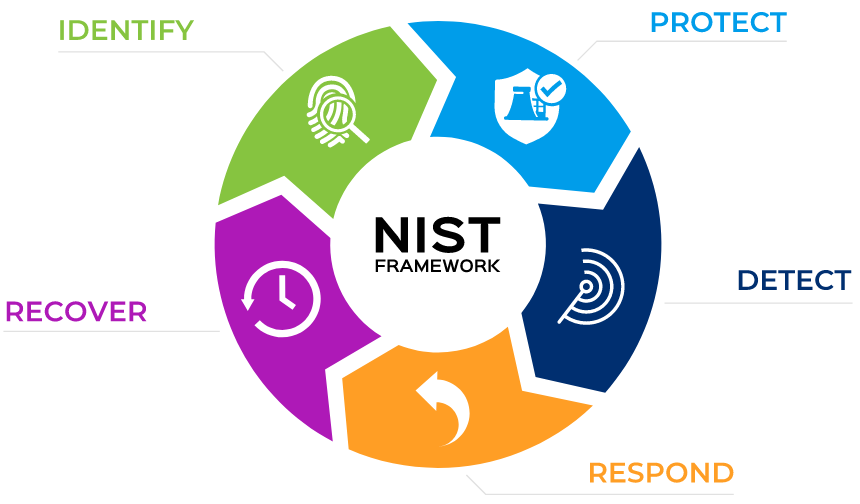
NIST CSF is a well-known framework built with the purpose to provide the private sector with enough information so that their critical IT infrastructure is secure.
CSF focuses on risk management and it is divided into three parts:
- Core functions: Identify, Protect, Detect, Respond, Recover
- Implementation: Risk management processes and practices
- Profiles specific to a business or industry with goals and desired outcomes
NIST SP 800-53 and 800-171

Initially, the SP 800-53 was designed for government agencies to protect their critical data and infrastructure. However, with SP 800-171, the Department of Defense (DoD) made it mandatory for all cybersecurity vendors and contractors to implement this standard to bid on new opportunities.
These are two different standardization documents but are very much interlinked, as most of the controls in SP 800-171 are related to SP 800-53.
PCI DSS
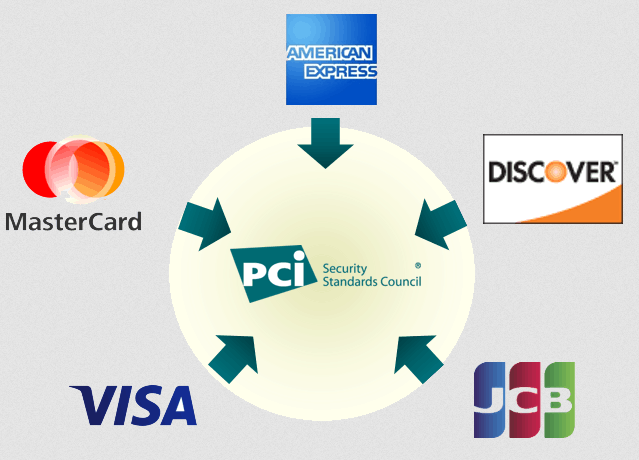
The Payment Card Industry’s Data Security Standard framework covers companies that handle credit card information in one of four ways:
- accepting credit cards
- processing the transactions
- storing this data or transmitting credit card data.
By putting this security framework in place and passing the certification process, a company proves that it has improved the security of the complete payment process.
Control Objectives for Information and Related Technology (COBIT)
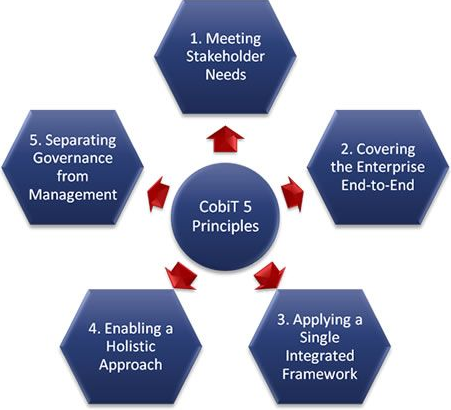
COBIT is the name of a security framework developed by an organization known as Information Systems Audit and Control Association (ISACA).
This framework defines governance and management principles, processes, and organizational structures for enterprise information technology.
COBIT provides the requirements for implementing an Information Security Management System (ISMS) and is compatible with the ISO/IEC 27000 series of standards
CONCLUSION
To become a Cybersecurity Expert you must have a passion for knowledge. This is a complex and demanding field where the combination of diverse skills is essential.
You have to be willing to fail and try again quite a few times. Persistence is key.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.








