Privilege escalation is one of the core concepts of information security. It refers to the type of attack where a user gains higher levels of access over computer systems or networks than the ones originally intended for the user.
What is privilege escalation?
Privilege escalation occurs when an attacker (or a legitimate user) exploits vulnerabilities, weak security controls, or system design, to obtain higher privileges than the one they should have. A simple user with basic rights on a system can exploit these weaknesses to elevate their privileges to administrator or root-level access, depending on the type of system.
This unauthorized access can lead to a multitude of security risks and data breaches.
Types of Privilege Escalation
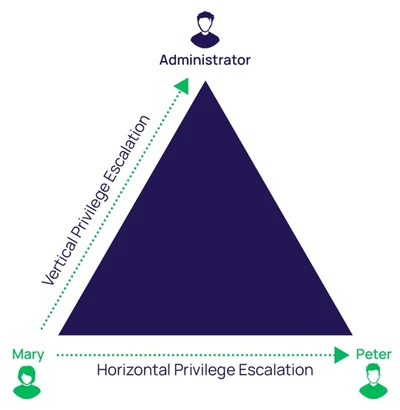
Privilege escalation can be categorized into two main types: Horizontal and Vertical privilege escalation.
In the horizontal privilege escalation, a user gains the privileges of another user at the same level. For example, one regular user gaining access to another regular user’s account.
In a vertical privilege escalation, the user escalates his privilege to a higher level, often from a user account to an administrative or superuser account.
Consequences of Privilege Escalation
- Expanded Control: Attackers can access sensitive data, execute arbitrary commands, and make system-level changes, potentially taking over the entire system.
- Persistence: Privilege escalation allows attackers to establish persistence on a compromised system, ensuring they can maintain control even after a system reboot or other disruptions.
- Lateral Movement: With elevated privileges, attackers can move laterally within a network, compromising additional systems and expanding the scope of the attack.
- Data Theft and Manipulation: Attackers can steal, alter, or delete data, which can have significant consequences, especially in cases involving sensitive information.
Common Attack Vectors Attackers Use To Perform Privilege Escalation
For attackers, privilege escalation is not the end goal. It is a means to an end.
Privilege escalation, as an attack type, only makes sense once the attacker already has access to a system. After their initial access, they will want to deepen their access and perform more severe actions utilizing their higher levels of access to the system.
To gain initial access to the system and perform privilege escalation, the attackers usually perform the following actions.
1. Vulnerability Identification and Exploitation
Attackers search for known vulnerabilities or zero-day vulnerabilities in software applications. These vulnerabilities can be found in software, operating systems, or configurations that allow for the exploitation of security weaknesses.
By exploiting these vulnerabilities, they can run malicious code that enables privilege escalation.
3. Misconfigured Access Controls
Even if vulnerabilities are not present in a system, an attacker can exploit misconfigured access controls on the system to gain access to sensitive files or execute commands with elevated privileges, gaining further access to the system.
4. Social Engineering
Social engineering is highly effective because it circumvents security controls by exploiting human emotions. Attackers have realized that it is much easier to trick or manipulate a user than guessing their password.
5. Credential Exploitation
Attackers can exploit valid user credentials to gain access to a system and they can get their hands on such credentials with various methods:
Password exposure: there are many cases where employees share passwords with others, reuse them, or store them in plaintext on computers.
Credential stuffing: attackers use a list of usernames or email addresses and passwords they obtained from previous breaches or the dark web, and try it against accounts in a target system. Because individuals commonly reuse passwords, this technique has high success rates.
Password guessing: attackers can use information like exposed credentials in the dark web to create custom wordlists by which they can make educated guesses about the new password the user has selected (brute force attack).
Shoulder surfing: attackers can observe the actions of privileged individuals, either in person, or through keyloggers on their devices, and thus gain access to passwords.
6. Malware
One of the many uses of malware used by attackers is to gain a hold on a system and then try to perform privilege escalation. This is because malware typically runs as an operating system process and has the permissions of the user account from which it was executed.
How To Prevent Privilege Escalation
To protect systems from attackers seeking to utilize privilege escalation, organizations can employ various strategies.
- Regular Patching: Keeping software and systems up-to-date helps patch known vulnerabilities.
- Access Control: Implementing robust access controls and monitoring permissions can prevent unauthorized access.
- Strong Authentication: Enforcing strong password policies and using multi-factor authentication can deter attackers.
- Monitoring and Incident Response: Continuously monitoring system logs and having a well-defined incident response plan in place can aid in the early detection and mitigation of attacks.
Conclusion
Understanding how attackers utilize privilege escalation is essential for devising effective security strategies. By recognizing the methods employed by malicious actors, organizations can better defend their systems and data against this pervasive threat. Vigilance, strong security practices, and a proactive stance are key to mitigating the risk of privilege escalation attacks.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.