Italian organizations are facing a significant threat from a phishing campaign unleashed by threat actors deploying a potent new malware called WikiLoader.
This insidious piece of malware serves as a delivery mechanism for various malicious payloads, including a banking trojan and the Ursnif malware. Designed with advanced evasion techniques, WikiLoader poses a significant challenge for detection and analysis, making it a formidable tool in the hands of cybercriminals.
Unveiling WikiLoader
A Malware-as-a-Service WikiLoader is a sophisticated downloader that operates as a malware-as-a-service, catering to multiple cybercriminal groups.
It first came into the spotlight in December 2022, attributed to the threat actor TA544, known for employing Ursnif malware to target Italian organizations. Since its initial identification, Proofpoint researchers have detected several subsequent campaigns, with a substantial focus on Italian entities. The malware earned its name due to a unique evasion technique – making a request to Wikipedia and verifying the presence of the string “The Free” in the response contents.
WikiLoader is designed to retrieve and execute a shellcode hosted on Discord, subsequently using it to execute Ursnif, further amplifying its impact on the victim’s system.
Evasive Campaign Tactics
The attack chain commences with malicious emails containing weaponized Microsoft Office attachments or PDFs. Although macro-enabled documents have fallen out of favor for malware delivery among most threat actors, TA544 persists in using them, notably to deliver WikiLoader. The malware distribution has also been linked to another threat actor, TA551, further exacerbating the risks for Italian organizations.
Phishing Examples and Delivery Mechanisms
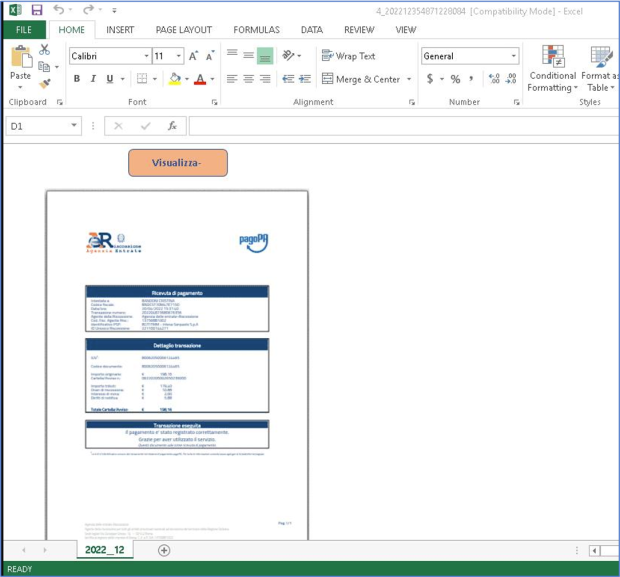
December Campaign: Impersonating the Italian Revenue Agency In a campaign observed in December, attackers used a phishing email spoofing the Italian Revenue Agency, featuring a Microsoft Excel attachment laden with VBA macros. Upon activation, the macros initiated the installation process of WikiLoader.
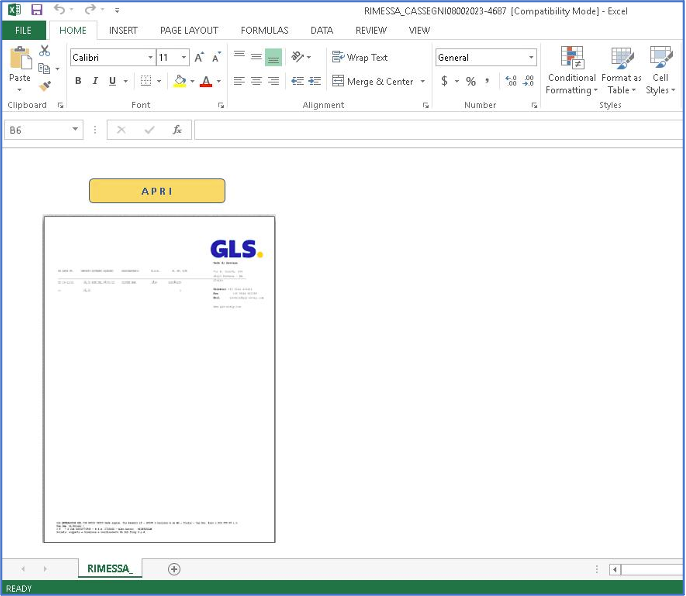
February Campaign: Impersonating an Italian Courier Service In February 2023, the attackers posed as an Italian courier service in their phishing email. The attached Excel file contained VBA macros that facilitated the installation of WikiLoader.
July Campaign: Exploiting Accounting Themes During a campaign in July, TA544 utilized accounting themes in their phishing emails, which included PDF attachments with URLs leading to the download of a zipped JavaScript file that executed WikiLoader.
Continuous Development and Mitigation Measures
The researchers have observed ongoing rapid development of WikiLoader, indicating the threat actors’ efforts to enhance its capabilities and effectiveness. To defend against this formidable threat, organizations are advised to disable macros by default for all employees, block the execution of embedded external files within OneNote documents, and ensure JavaScript files are opened by default in notepad or similar applications, achieved through group policy object (GPO) adjustments.
Conclusion
WikiLoader poses a severe and persistent danger to Italian organizations, with its dynamic nature and ability to deliver multiple malicious payloads. As cybercriminal tactics evolve, staying vigilant and adopting robust security measures becomes imperative in safeguarding sensitive data and thwarting potential attacks. Organizations must remain proactive in their cybersecurity strategies to mitigate the risks posed by WikiLoader and other sophisticated malware-as-a-service threats.





