A sophisticated Chinese nation-state group has been identified employing HTML smuggling techniques to target Foreign Affairs ministries and embassies in Europe. The campaign, named SmugX, showcases the group’s strategic shift towards European targets. Cybersecurity firm Check Point has been monitoring this activity since December 2022 and highlights the use of new delivery methods, particularly HTML Smuggling, to distribute the PlugX remote access trojan on compromised systems.
HTML Smuggling: A Stealthy Attack Vector
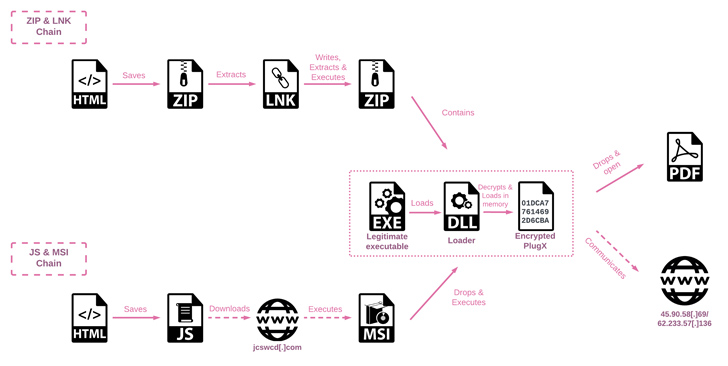
In the SmugX campaign, the threat actors utilize HTML Smuggling, a stealthy technique that exploits legitimate HTML5 and JavaScript features to assemble and launch malware. By leveraging this method, the attackers embed the malware within decoy documents attached to spear-phishing emails. HTML smuggling leverages HTML5 attributes that can function offline by storing binary data within JavaScript code. This data blob, or embedded payload, is decoded into a file object when opened via a web browser, enabling the execution of the malware.
SmugX Targets Diplomats and Government Entities
Analysis of the decoy documents, which were uploaded to the VirusTotal malware database, reveals that the SmugX campaign specifically targets diplomats and government entities in various European countries.
The primary targets include Czechia, Hungary, Slovakia, the U.K., Ukraine, and potentially France and Sweden. The threat actor employs various lures to entice victims, including an Uyghur-themed lure titled “China Tries to Block Prominent Uyghur Speaker at UN.docx.” Once opened, this document establishes a connection with an external server through an embedded invisible tracking pixel to extract reconnaissance data.
The PlugX Remote Access Trojan: A Persistent Threat
The SmugX campaign utilizes the PlugX remote access trojan, also known as Korplug, as its final payload. Dating back to 2008, PlugX is a modular trojan that accommodates diverse plugins, allowing the threat actors to execute a range of malicious activities. These include file theft, screen captures, keystroke logging, and command execution.
The infection process involves DLL side-loading techniques to decrypt and launch the PlugX trojan. To cover their tracks, the threat actors even dispatched a batch script named del_RoboTask Update.bat, which erases evidence of their activities by deleting the legitimate executable, the PlugX loader DLL, and the registry key used for persistence.
The Adversarial Collective: Unveiling the Culprits
While the exact identity of the threat actor behind the SmugX campaign remains unclear, preliminary evidence points to the involvement of Mustang Panda, which shares similarities with other clusters such as Earth Preta, RedDelta, and Camaro Dragon. However, conclusive attribution to the adversarial collective is currently lacking.
Conclusion
The SmugX campaign orchestrated by a Chinese nation-state group demonstrates the evolving threat landscape faced by European Foreign Affairs ministries and embassies. The use of HTML Smuggling as an attack vector highlights the adversaries’ adaptability and ability to evade detection. Organizations should remain vigilant, enhance their cybersecurity measures, and stay updated on emerging attack techniques to effectively defend against such sophisticated threats.