Avast, the renowned cybersecurity firm, has released a free decryptor for the Akira ransomware. This decryptor enables victims to recover their encrypted data without having to pay the ransom demanded by the attackers.
The Akira ransomware has been active since March 2023 and has targeted various organizations across different industries, including education, finance, and real estate. In this article, we will explore the details of the Akira ransomware, the release of the decryptor by Avast, and how victims can utilize it to regain access to their data.
The Akira Ransomware: A Brief Overview
The Akira ransomware is a malicious software that specifically targets Windows systems.
It is a 64-bit Windows binary written in C++ and utilizes the Boost library to implement its encryption code. The authors of the ransomware have employed the Microsoft Linker version 14.35 for its development. In June 2023, a malware analyst named rivitna published a sample of the Akira ransomware that is compiled for Linux. This Linux variant is also 64-bit and employs the Boost library, although it uses the Crypto++ library instead of the Windows CryptoAPI.
During its operation, the Akira ransomware generates a symmetric encryption key using CryptGenRandom(), which is a random number generator implemented by Windows CryptoAPI. It employs the Chacha 2008 encryption algorithm, which is based on D. J. Bernstein’s implementation. The symmetric key is then encrypted using the RSA-4096 cipher and appended to the end of the encrypted file. It’s important to note that the public key used for encryption is hardcoded in the ransomware binary and varies between different samples. The encrypted files are identified by the .akira extension, and a ransom note named “akira_readme.txt” is dropped in each affected folder.
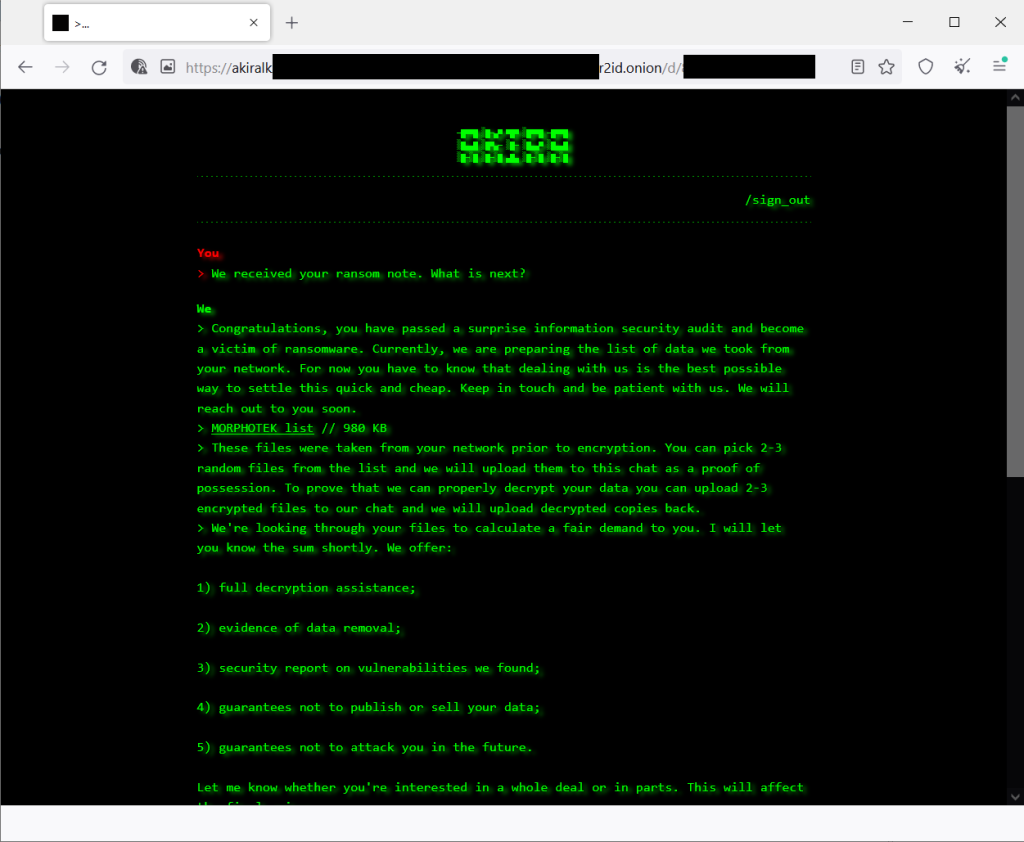
Avast’s Decryptor for Akira Ransomware
To assist the victims of the Akira ransomware, Avast has developed a decryptor that can restore the encrypted files without requiring the payment of the ransom. Avast has released both 64-bit and 32-bit decryptors, ensuring compatibility with different Windows systems.
However, it’s worth noting that the 64-bit decryptor is recommended, as the ransomware itself is designed for 64-bit systems.
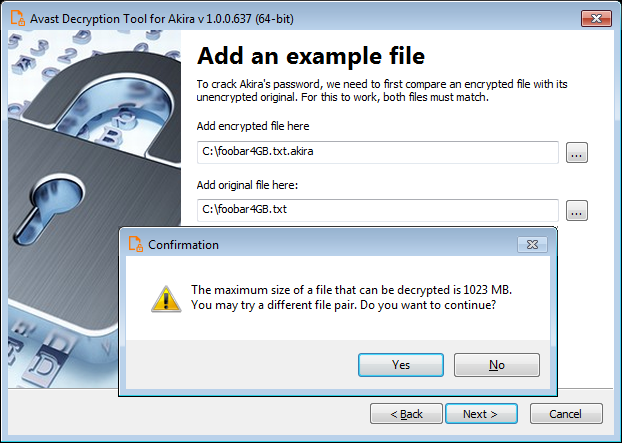
To utilize the decryptor, victims need to provide a pair of files: one encrypted by the Akira ransomware and its original, unencrypted version. Avast has provided a user-friendly wizard that allows users to supply the file pair. It is crucial to select files that are as large as possible, as the block size calculation of Akira can result in varying size limits, even for files that differ in size by just a single byte. The decryptor also offers the option to back up the encrypted files, which is highly recommended by Avast for added security.
Decryptor for Linux Variant and IOCs
While Avast has released a decryptor for the Windows version of the Akira ransomware, it is important to note that a decryptor for the Linux variant has not been released yet. The Linux version of the ransomware operates in a similar manner to its Windows counterpart but utilizes different libraries for encryption. Security researchers are actively analyzing the Linux variant to develop a decryptor, and it is advisable for Linux users affected by the Akira ransomware to regularly check for updates from cybersecurity companies.
In addition to the decryptor, Avast has also shared Indicators of Compromise (IOCs) associated with the Akira ransomware. These IOCs can help organizations and individuals detect and prevent potential infections. The IOCs typically include file hashes, file extensions, ransom note names, and other artifacts that can indicate the presence of the Akira ransomware. By monitoring and blocking these IOCs, users can enhance their defenses against this particular ransomware strain.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.