Recent findings by Microsoft security researchers have unveiled a concerning cyberattack campaign that involves lateral movement to a cloud environment through a Microsoft SQL Server instance. While this approach has been observed in other cloud services like VMs and Kubernetes clusters, its emergence within SQL Server instances raises fresh concerns in the realm of cybersecurity.
Attack Genesis
The attackers initiated their assault by exploiting a SQL injection vulnerability within an application in the target’s environment. This initial breach provided them with access and elevated permissions on a Microsoft SQL Server instance deployed in Azure Virtual Machine (VM), a move that marked the beginning of their intricate lateral movement strategy.
Abusing Cloud Identities
With acquired elevated permissions on the SQL Server, the attackers then leveraged the server’s cloud identity. Cloud identities are commonplace in cloud services, including SQL Server, and often possess elevated permissions. This tactic aimed to facilitate the lateral movement of the attackers to additional cloud resources, thereby expanding the scope of their unauthorized access.
Microsoft Defender for SQL Alerts
The attack was flagged by multiple Microsoft Defender for SQL alerts, enabling the identification and analysis of this novel cloud lateral movement technique. Despite a lack of visibility into the targeted application that initially fell victim to the SQL injection vulnerability, these alerts empowered swift response and enhanced protection measures.
Attack Tactics Unveiled
The attackers’ modus operandi involved a series of familiar SQL Server attack activities. These encompassed SQL injection exploitation, data gathering, and elevating permissions. The information gathered included details on databases, table schemas, database versions, network configurations, and permissions.
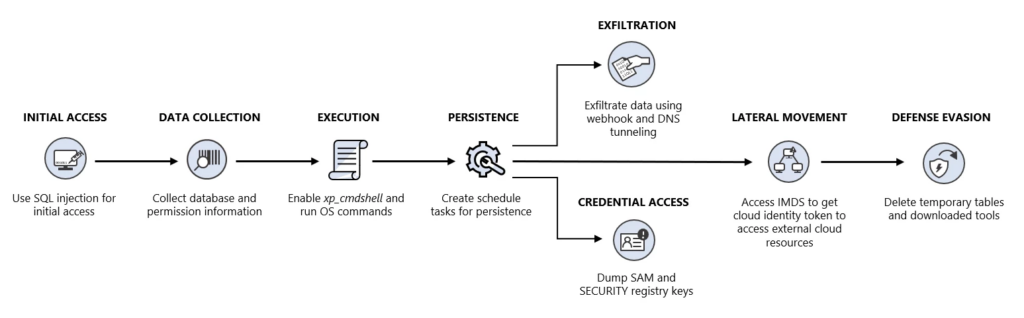
The attackers also enabled the xp_cmdshell command, a method for executing OS commands through SQL queries, to gain shell-like access to the host. They proceeded to collect data, download encoded executables and PowerShell scripts, and establish persistence through a scheduled task. Additionally, attempts to extract credentials by dumping SAM and SECURITY registry keys were made.
Unique Data Exfiltration
A unique aspect of this attack was the data exfiltration method employed by the attackers. They utilized a publicly accessible service called “webhook.site” to discreetly transmit outgoing traffic. This service served as a covert platform for their malicious actions.
Cloud Identity Leveraging
The attackers also made a distinctive move by attempting to leverage the cloud identity of the SQL Server instance. They accessed the Identity Metadata Service (IMDS) to obtain the cloud identity access key. Although their efforts in this regard encountered an error, this technique introduces a potential avenue for lateral movement.
Conclusion
This attack has illuminated the novel phenomenon of lateral movement from a SQL Server instance to the cloud. While this technique is not new in other cloud environments, its appearance in SQL Server instances warrants increased vigilance. As organizations increasingly migrate to the cloud, attackers are adapting known tactics to new environments, emphasizing the need for robust defenses and asset protection.
The importance of adopting least privilege practices in cloud and on-premises solutions cannot be overstated. Over-privileged processes, accounts, managed identities, and database connections often serve as entry points for malicious activities. By adhering to security best practices and limiting permissions to what is strictly necessary, organizations can reduce the attack surface and mitigate risks.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.





