You can build a penetration testing lab on a raspberry pi with DVWA to test your skills and also learn new tricks on how to attack and/or secure web applications in a safe environment.
The “Damn Vulnerable Web Application” also known as DVWA, is a vulnerable PHP/MySQL web application.

How to Install DVWA
The simplest and easiest way to install DVWA is with docker.
Assuming you have docker installed on your machine simply run:
docker pull cambarts/arm-dvwaIf you dont have the DVWA image already downloaded, the command above will do that for you.
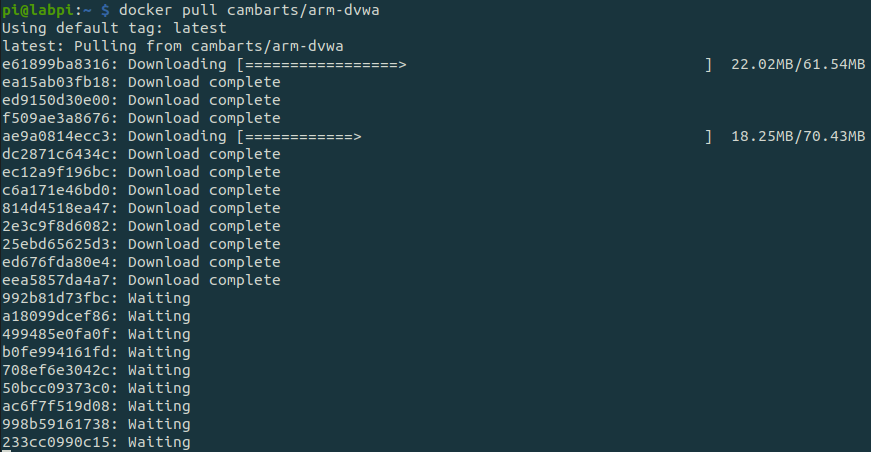
To start the container with a random mysql password run:
docker run -d -p 80:80 cambarts/arm-dvwaIf you want to set your own password use the following command, replacing the “mypass” value with your own desired password:
docker run -d -p 80:80 -p 3306:3306 -e MYSQL_PASS="mypass" cambarts/dvwaYou should then have a container running the DVWA.
Run the following to list your docker containers and see your container running exposing ports 80 and 3306:
docker ps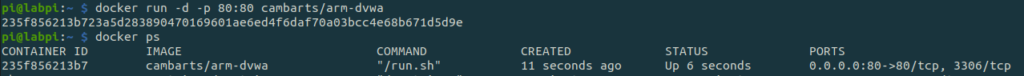
Setup Database
You may now navigate to the IP address of your raspberry pi on port 80, in my case http://192.168.10.27 and you will see the DVWA prompting you to setup the database.
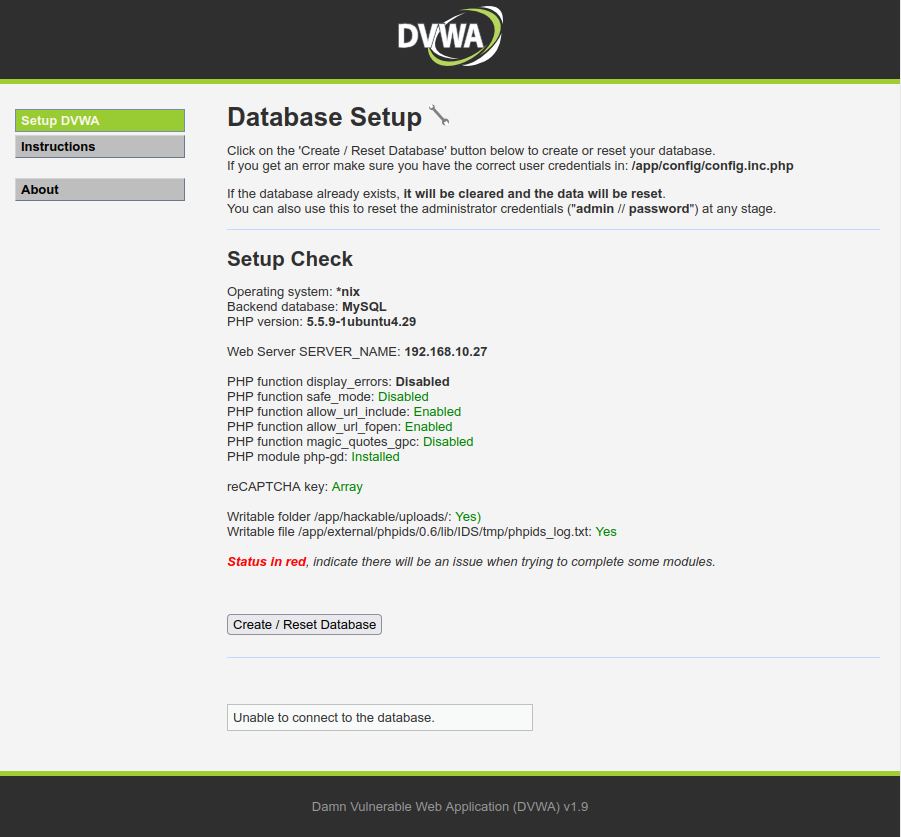
Click on “Create / Reset Database” and you will be redirected to the application’s login page.
Use “admin” and “password” and you are in!
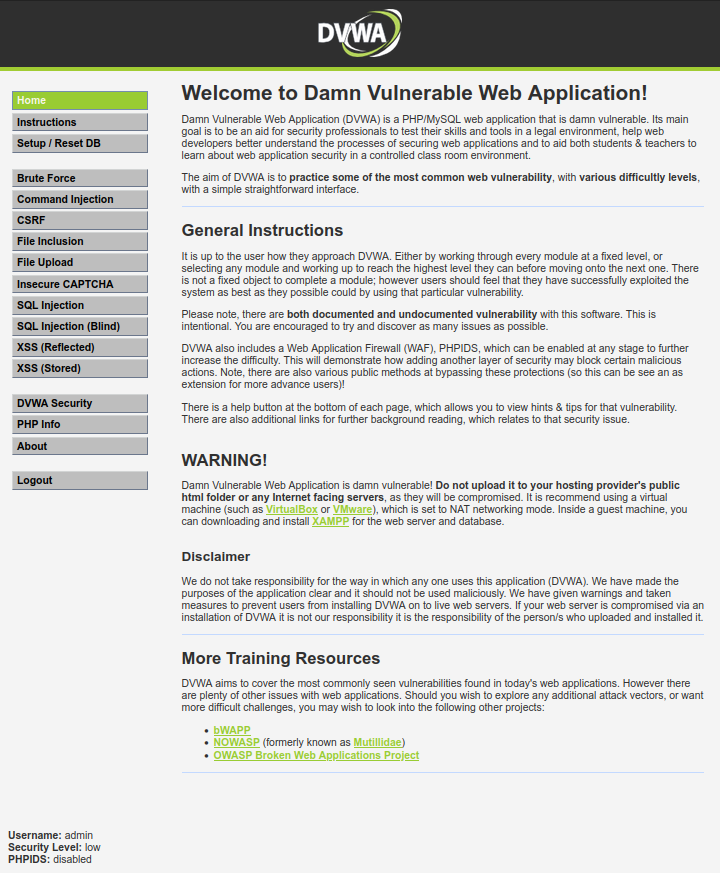
Set the Security Level
In DVWA there are 4 different security levels, low, medium, high and impossible. You may navigate to the “DVWA security” on the right menu to choose the level of your preference..
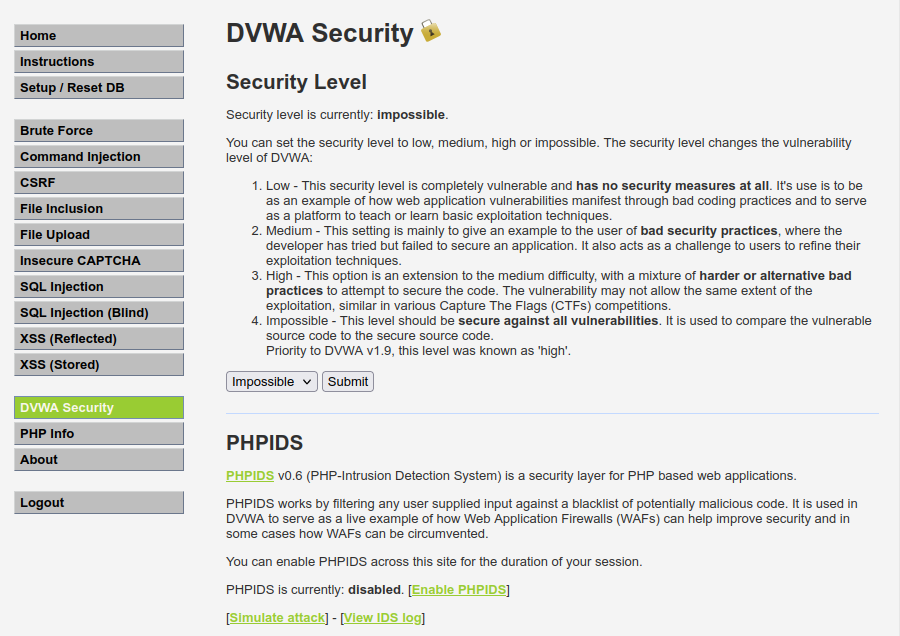
You may also want to choose to enable PHPIDS which is used as alive example of how Web Application Firewalls help you improve security and in some cases how WAFs can be circumvented.
Attack Types
With DVWA you can practice several types of attacks. Start with “Low” security level and play with all the types of attacks, with several tools and techniques. Once you feel more comfortable, increase the security level to make the tests more challenging.
- Brute Force
- Command Injection
- CSRF
- File Inclusion
- File Upload
- Insecure Captcha
- SQL injection
- SQL injection (Blind)
- XSS reflected and stored
Learning while breaking stuff 🙂
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






