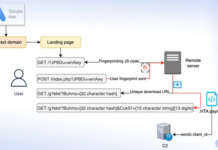
Tens of thousands of physical and virtual devices running Cisco networking software have been compromised as the result of a yet-unpatched vulnerability, according to multiple independent researchers.
The Vulnerability
Cisco recently issued a security advisory, highlighting the presence of an unpatched vulnerability in its IOS XE software. This vulnerability, designated CVE-2023-20198, has become the epicenter of a major security concern due to the potential risks it poses.
The successful exploitation of this vulnerability could provide attackers with “full control of the compromised device” and allow for “possible subsequent unauthorized activity.” Cisco’s Talos threat intelligence group has been vigilant in warning about the gravity of this situation.
The Scale of Compromise
As security experts raced to gauge the extent of the compromised devices, shocking revelations emerged. Jacob Baines, CTO of VulnCheck, pointed out that Cisco’s initial disclosure downplayed the issue, failing to mention the thousands of internet-facing IOS XE web interfaces that have been infiltrated.
The scope of the compromise is not limited to a specific region, it has reached a global scale. Researchers at Censys identified a staggering 34,140 devices with backdoor implants, the majority of which are in the United States.
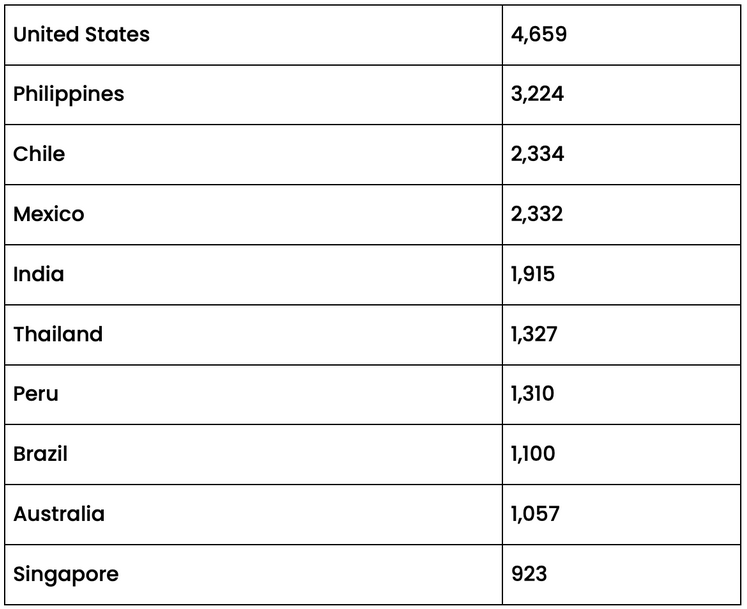
An analysis of the autonomous systems connected to the compromised device IP addresses reveals that telecommunications companies providing internet services to households and businesses are the primary targets.
Cisco’s Response
In response to this alarming breach, Cisco has been working relentlessly to develop a software fix. They urge customers to take immediate action in line with the guidelines outlined in their security advisory.
While it remains unclear who is responsible for these compromises, it is believed that they were carried out by the same actor. The attackers exploited a previous vulnerability, CVE-2021-1435, to implant malicious code on devices.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.