In the ever-evolving landscape of cyber threats, threat actors have an arsenal of methods to infiltrate an organization’s infrastructure. While the tactics may vary, one tool stands out as a favorite among financially motivated cybercriminals: vulnerability exploits.
This article delves into the intersection of vulnerabilities and ransomware attacks, shedding light on the alarming prevalence of exploitation in the digital realm.
The Vulnerability-Ransomware Nexus
The Cybersecurity and Infrastructure Security Agency (CISA) recently shared startling insights into the world of cyber threats. According to their data, nearly one in five common vulnerabilities and exposures (CVE) exploited in the digital arena also finds itself entwined with ransomware attacks. This revelation stems from CISA’s Known Exploited Vulnerabilities Catalog, a repository of 1,019 CVEs, some dating as far back as 2002.
Ransomware’s Favorite Entry Points
The latest update to CISA’s catalog includes a rather grim addition: CVEs with known ransomware exploits.
This update reveals that a staggering 184 CVEs have been associated with ransomware attacks.
Among these, more than 40% are linked to Microsoft products, which are ubiquitous in enterprise environments. In a disconcerting lead, Microsoft outstrips other vendors with a whopping 78 exploited CVEs utilized in ransomware attacks.

The Microsoft Dominance
Delving deeper into this unsettling revelation, we find that over half of the exploited Microsoft vulnerabilities are connected to two of the tech giant’s most popular products: Windows and Exchange Server.
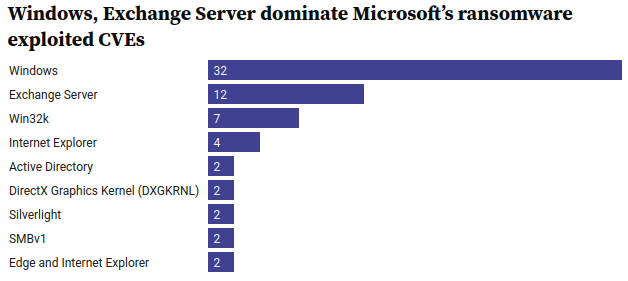
Despite these vulnerabilities being glaring points of entry for ransomware attacks, Microsoft has not responded to inquiries about the situation.
The Ransomware Menace
Ransomware has wreaked havoc on critical services, businesses, and communities globally. Often, these disruptive incidents are orchestrated by threat actors who exploit known CVEs. As Sandra Radesky, Associate Director of Vulnerability Management, and Gabriel Davis, Lead Operations Risk Advisor at CISA, pointed out in a recent blog post, many organizations may be unaware that these vulnerabilities lurk within their networks.
Conclusion
The battle against ransomware is a pressing concern. CISA is taking action to address this issue with the Ransomware Vulnerability Warning Pilot, mandated by the Cyber Incident Reporting for Critical Infrastructure Act of 2022. With these initiatives, we aim to dispel the shadows and bring the vulnerabilities used by ransomware threat actors into the light.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






