Grafana, a widely used open-source platform for analytics and visualization, has recently been discovered to have a security vulnerability. This system caters to a broad range of users, from those involved in small-scale projects to enterprises implementing large-scale installations. Grafana provides users with user-friendly tools for data analysis and visualization, delivering simplicity and aesthetic appeal.
The security flaw, identified as CVE-2023-3128, has been assigned a severity score of 9.4 out of 10 on the CVSS scale. This vulnerability has the potential to allow unauthorized individuals to bypass authentication protocols and gain control over users’ accounts.
At its core, the CVE-2023-3128 vulnerability in Grafana enables the circumvention of authentication or the unauthorized takeover of another user’s account. The vulnerability originates from the validation method employed by Grafana, specifically when it checks Azure Active Directory (Azure AD) accounts based on their email claim in combination with Azure AD OAuth. The challenge lies in the fact that the email address entered in the profile box may not be unique across all Azure AD tenants, allowing one Azure AD tenant to impersonate another using a similar email address.
The consequences of this vulnerability are extensive and alarming. Exploiting this security flaw can grant attackers complete control over a user’s account, potentially exposing sensitive customer data and other crucial information.
Grafana installations that utilize Azure AD OAuth and are configured with a multi-tenant Azure AD OAuth application, but lack an “allowed_groups” option, are particularly susceptible to this vulnerability. If you are currently using Grafana version 6.7.0 or later, it is vital to take immediate action.
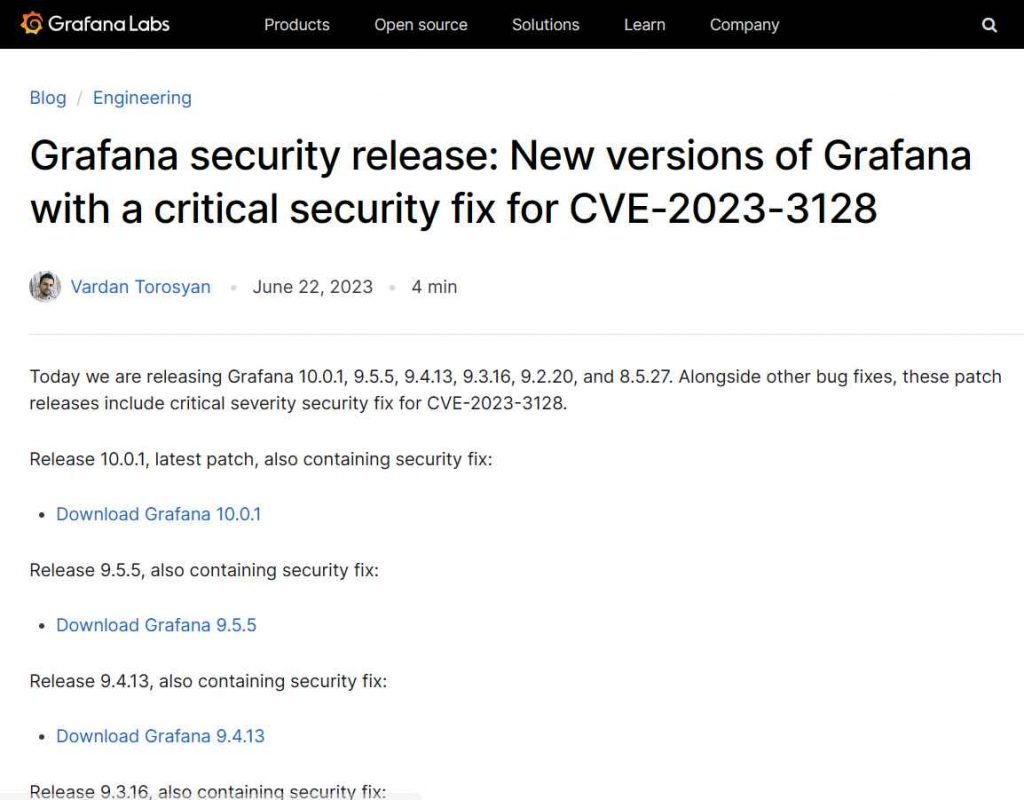
Responding promptly to this critical issue, the Grafana development team has released patches for the vulnerability in versions 10.0.1, 9.5.5, 9.4.13, 9.3.16, 9.2.20, and 8.5.27, respectively. To ensure your security, ensure that you are using one of these versions or a later one.
However, what should you do if an update is not immediately feasible? The good news is that there are mitigation strategies that can be implemented. First and foremost, you can enhance security by ensuring that a user who signs in also belongs to a group in Azure AD. This can be achieved by adding an “allowed_groups” parameter to your Azure AD configuration. By implementing this step, the likelihood of an attacker using an arbitrary email address is significantly reduced.
Another effective approach is to register a single tenant application in Azure Active Directory. This eliminates the possibility of cross-tenant impersonation, which is one of the attack vectors associated with this vulnerability.
In conclusion, Grafana, a widely adopted open-source system for analytics and visualization, has recently encountered a security flaw, identified as CVE-2023-3128. This vulnerability allows attackers to bypass authentication protocols and take control of user accounts. The potential consequences are far-reaching, potentially compromising sensitive customer data and other critical information. To address this issue, the Grafana development team promptly released patches for the vulnerability in several versions. It is crucial for users to update their installations to the patched versions or apply mitigation strategies, such as configuring Azure AD with “allowed_groups” or opting for a single tenant application in Azure Active Directory.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.





