Millenium-RAT, a sophisticated Remote Access Tool (RAT) for Windows systems is now available for purchase on GitHub. This sophisticated Remote Access Tool, or RAT, has made its home exclusively on Windows systems, posing a significant danger to individuals and organizations alike.
Millenium-RAT 2.4: A Stealthy Operative
Millenium-RAT, particularly version 2.4, is a Win32 executable firmly rooted in the .NET framework. Its primary purpose is to retrieve data from compromised systems covertly. Its evolution from version 2.4 to the latest iteration, 2.5, underlines the dynamic nature of its threat landscape.
CYFIRMA aptly describes this malware as a prime example of a complex and malicious toolkit meticulously crafted to achieve multiple objectives.
Millenium-RAT is designed to steal sensitive user data, persist on a compromised device even when faced with cutting-edge anti-analysis techniques, and grant hackers remote control over the infected system.
Versatile and Dangerous
The Millenium-RAT-2.4 boasts a wide range of capabilities, making it a versatile and dangerous tool in the hands of cybercriminals.
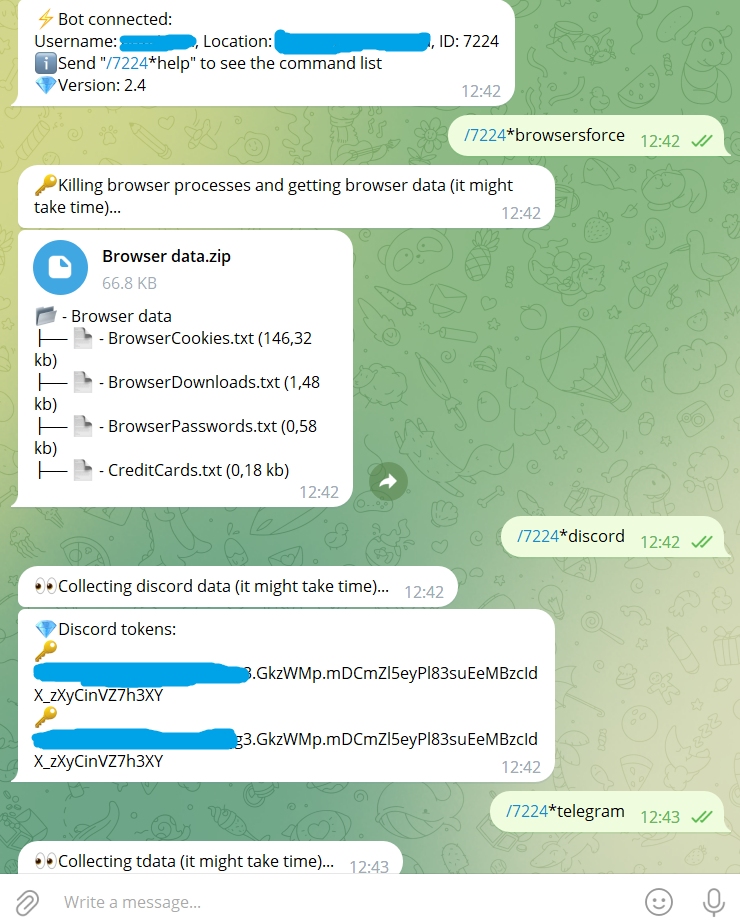
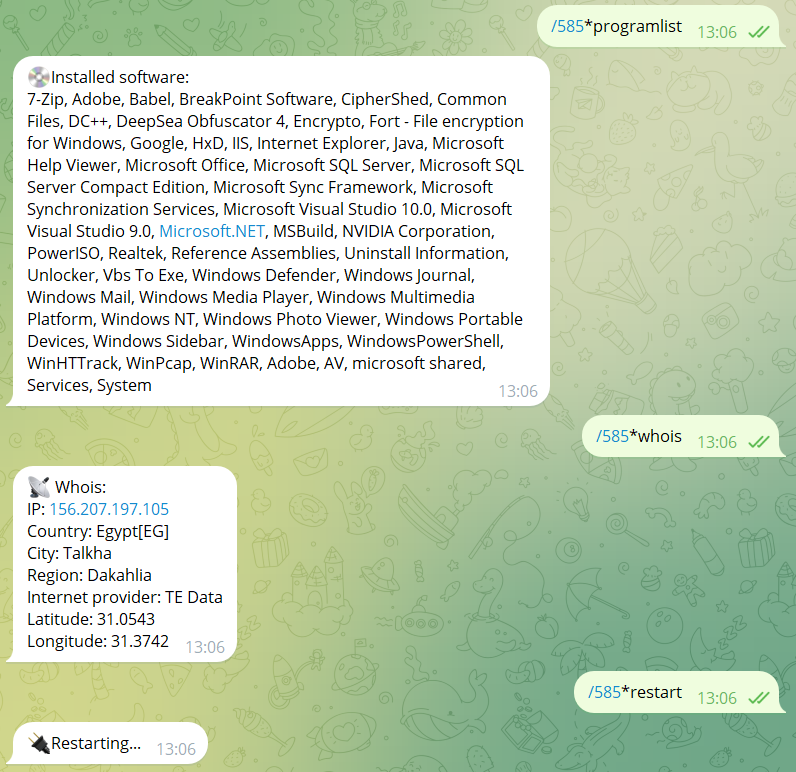
Its functionalities encompass data exfiltration, system information gathering, process disruption, self-destruct mechanisms, evasion strategies tailored for sandbox environments, anti-debugging measures, and remote command execution through the Telegram platform.
Cloaked in False Pretenses
What makes this threat particularly insidious is its presence on GitHub, where it’s advertised under the guise of an educational resource. Behind this facade lies a covert offer of lifetime access in exchange for a modest sum.
While the project remains a closed source, rendering its code inaccessible to the public, interested parties are directed to contact the project via Telegram to obtain access.
The examined sample from version 2.4, revealed by the malware creator on their GitHub account, is available for lifetime access for a mere $30.
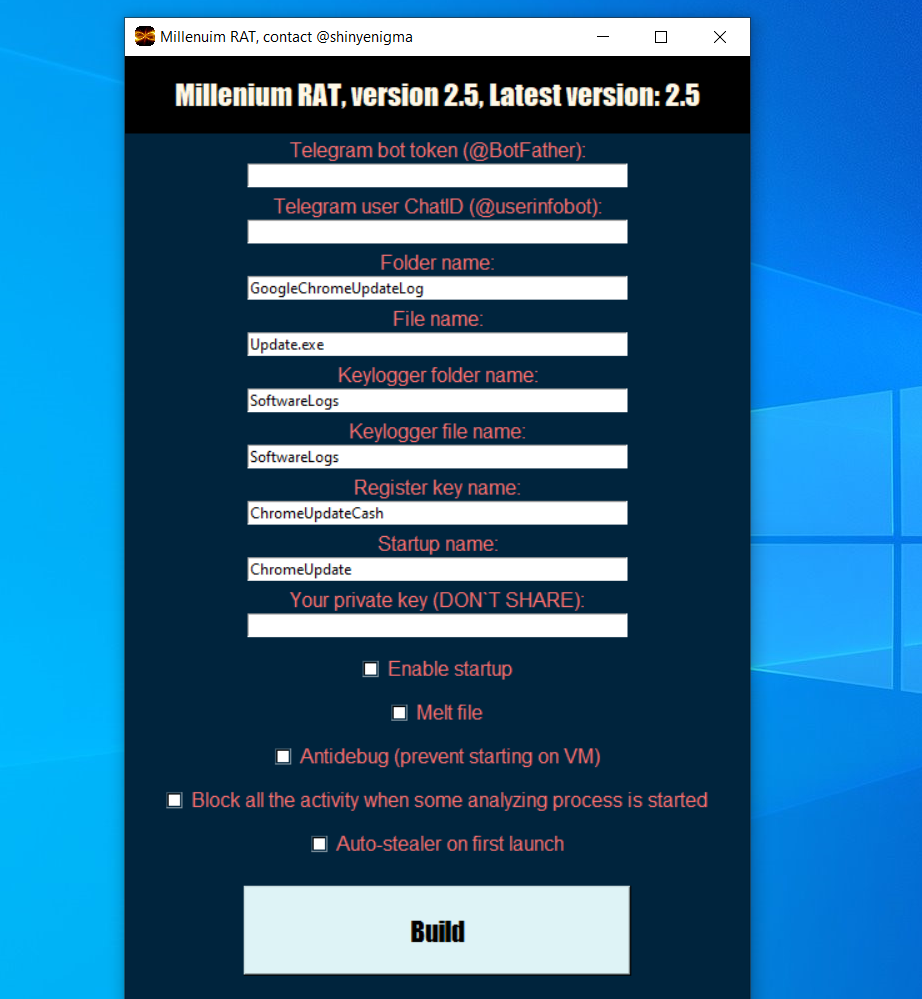
Moreover, the RAT builder further enhances its adaptability, allowing users to customize the RAT to meet specific requirements. This customization includes features like specifying the Telegram chat ID, Telegram Bot token, and even choosing specific filenames, such as the keylogger file.
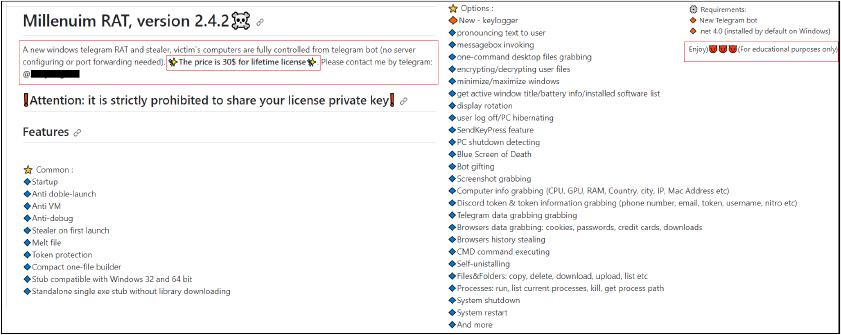
Millenium RAT Advertised Features
The features of Millenium RAT as advertised on Github are:
⭐️ Common :
🔹Startup
🔹Anti doble-launch
🔹Anti VM
🔹Anti-debug
🔹Stealer on first launch
🔹Melt file
🔹Token protection
🔹Compact one-file builder
🔹Stub compatible with Windows 32 and 64 bit
🔹Standalone single exe stub without library downloading
⭐️ Options :
🔶New – keylogger
🔹pronouncing text to user
🔹messagebox invoking
🔹one-command desktop files grabbing
🔹encrypting/decrypting user files
🔹minimize/maximize windows
🔹get active window title/battery info/installed software list
🔹display rotation
🔹user log off/PC hibernating
🔹SendKeyPress feature
🔹Blue Screen of Death
🔹Bot gifting
🔹Screenshot grabbing
🔹Computer info grabbing (CPU, GPU, RAM, Country, city, IP, Mac Address etc)
🔹Discord token & token information grabbing (phone number, email, token, username, nitro etc)
🔹Telegram data grabbing grabbing
🔹Browsers data grabbing: cookies, passwords, credit cards, downloads
🔹Browsers history stealing
🔹CMD command executing
🔹Self-unistalling
🔹Files&Folders: copy, delete, download, upload, list etc
🔹Processes: run, list current processes, kill, get process path
🔹System shutdown
🔹System restart
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






