Now Microsoft has confirmed the risk that “an attacker with physical access to a system can use Thunderspy to read and copy data even from systems that have encryption with password protection enabled.” The vulnerability is in hardware, and so cannot be patched. According to Microsoft, someone with physical access to the device “could sign in and exfiltrate data or install malicious software.”
WHAT YOU CAN DO?
Microsoft’s advice to “stay ahead of advanced data theft” is to buy a new PC. (!!!)
Not just any PC, of course, but one of their newly minted “secured-core PCs.”

These have been around since late last year and come with all the security bells and whistles enabled in hardware and firmware, “mitigating Thunderspy and any similar attacks that rely on malicious DMA.” Intel told me that a Thunderspy attack “could not be successfully demonstrated on systems with Kernel DMA protection,” a feature enabled by default on Microsoft’s Secured-core PCs.
As Microsoft explains, “even if an attacker was able to copy malicious Thunderbolt firmware to a device, the Kernel DMA protection on a Secured-core PC would prevent any accesses over the Thunderbolt port unless the attacker gains the user’s password… significantly raising the degree of difficulty.”
There is now a range of Secured-core PCs available, aimed at business users, likely those with a heightened sense of security awareness, who travel regularly (albeit not just at the moment), and who have valuable data on their machines. This isn’t just spooks—business leaders, VIPs, negotiators, politicians, anyone with sensitive data who travels and leaves their PC out of sight for periods of time.



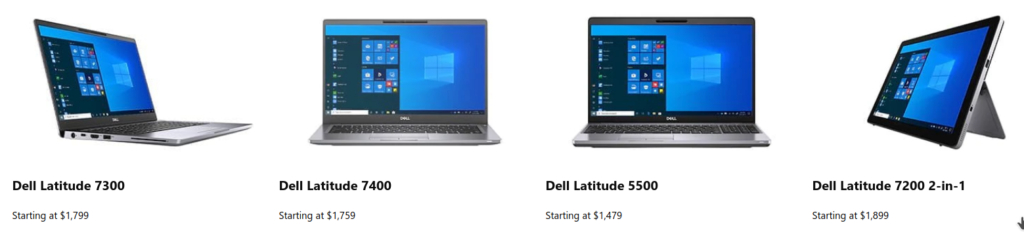
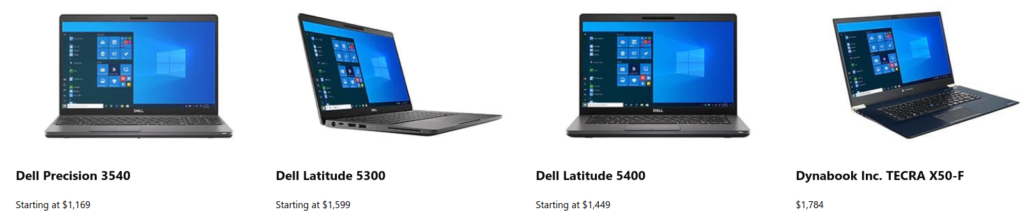
Pricy choices right?
Well these are the prices to pay to stay ahead from these types of threats.
The alternative according to former British intel officer Philip Ingram is to:
“Take a burner device with only the data you need for those meetings on a separate USB. Never connect it to any network when you return home and only use it for travel to that country. If you ever leave it unattended assume the hardware has been compromised. If you have been subject to extended searches at an airport and have lost sight of your IT, assume it has been compromised.”




