A significant threat has emerged from an activity group known as Forest Blizzard (STRONTIUM), originating from Russia. This group has been actively exploiting a critical vulnerability, CVE-2023-23397, in Microsoft Exchange servers to gain unauthorized access to email accounts. The collaboration between the Polish Cyber Command (DKWOC) and Microsoft has been pivotal in combating this threat, as detailed in their report on detecting malicious activity against Microsoft Exchange servers.
Understanding Forest Blizzard: The Russian State-Sponsored Cyber Threat
Forest Blizzard, tracked by Microsoft, is a formidable Russian state-sponsored cyber group primarily targeting sectors such as government, energy, transportation, and NGOs in the US, Europe, and the Middle East. Their linkage to the Russian Federation’s military intelligence agency, GRU, particularly to Unit 26165, has been confirmed by both the United States and the United Kingdom. Their tactics involve using publicly available exploits, including a series of CVEs alongside CVE-2023-23397, indicating their advanced capabilities and resources.
The Exploitation of CVE-2023-23397: A Critical Outlook Vulnerability
The exploitation of CVE-2023-23397, a severe elevation of privilege vulnerability in Microsoft Outlook, demonstrates the sophistication of Forest Blizzard’s operations. The vulnerability is triggered when a user receives a specially crafted message, leading to a Net-NTLMv2 hash leak. This can result in significant unauthorized access, making it imperative for organizations to understand this vulnerability and its implications fully.
Post-Exploitation Techniques and Threat Hunting
The exploitation of CVE-2023-23397 leaves minimal forensic artifacts, making it challenging to detect. Microsoft Incident Response has observed specific post-exploitation activities targeting Microsoft Exchange Server, including Net-NTLMv2 Relay attacks and the abuse of Exchange Web Services (EWS) API. These activities highlight the need for organizations to adopt a comprehensive threat hunting strategy to identify credential compromises.
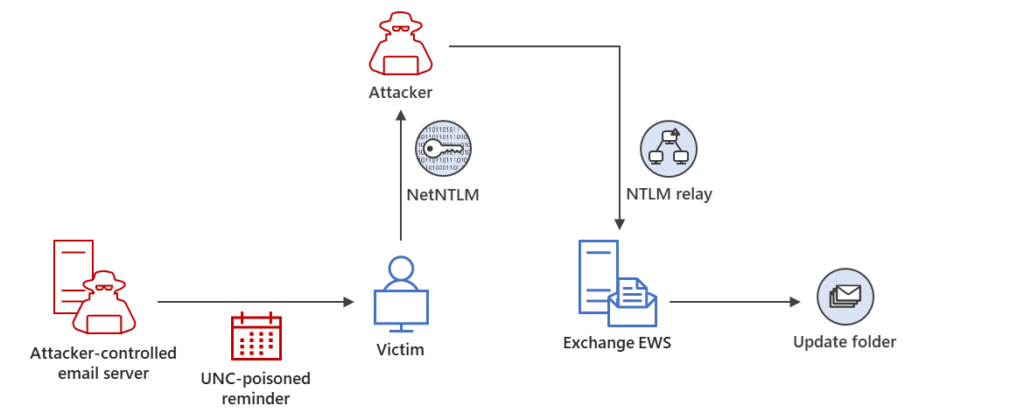
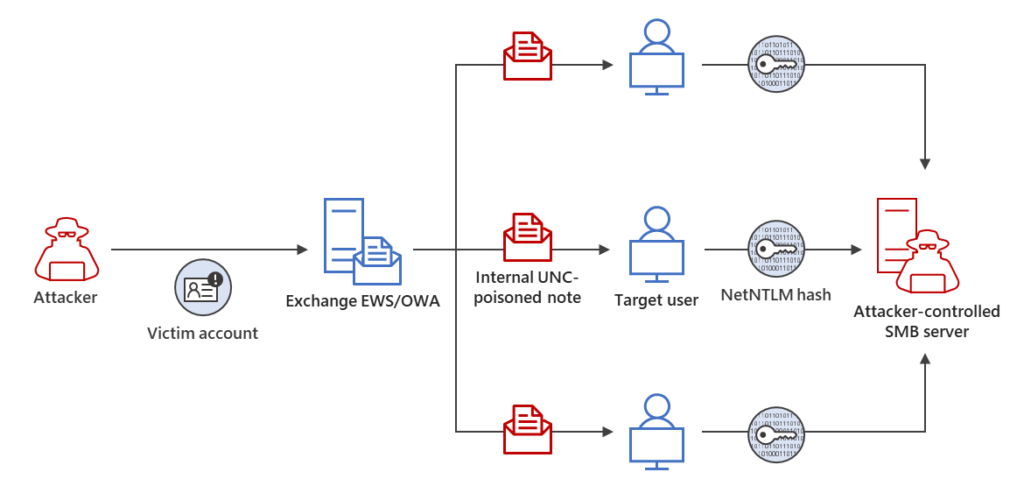
Mitigating the Threat: Steps and Strategies
To mitigate this threat, it is crucial for users to ensure that Microsoft Outlook is updated regularly. Microsoft Defender XDR provides detection capabilities for this exploitation. Furthermore, organizations should employ strategies such as network and endpoint logging analysis, reviewing suspicious messages, and utilizing Microsoft’s Exchange scanning script to identify potential compromises.
Conclusion: A Call to Vigilance and Proactive Defense
The stealthy nature of CVE-2023-23397’s exploitation by Forest Blizzard poses a unique challenge. Organizations must adopt vigilant and proactive defense mechanisms, utilizing Microsoft’s resources and intelligence reports to stay ahead of this evolving threat. The collaboration between entities like Microsoft and national cyber commands remains a critical component in mitigating such sophisticated cyber threats.
For more detailed information and guidance on tackling this threat, visit the official Microsoft page on the topic and leverage their tools and intelligence reports to strengthen your cybersecurity posture.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






