TA453, a sophisticated nation-state actor, has been identified as an entity closely associated with various other notorious groups such as Charming Kitten, PHOSPHORUS, and APT42.
In May 2023, TA453 deviated from its usual approach of employing Microsoft Word documents with macros, and instead, began utilizing LNK infection chains.
Luring the Target: Spear-Phishing with a Benign Conversation
To deceive its victims, TA453 crafted spear-phishing messages that posed as benign conversations. One such example involved impersonating a senior fellow from the Royal United Services Institute (RUSI) and targeting a public media contact of a US-based think tank specializing in foreign affairs and nuclear security.
The spear-phishing emails sought feedback on a project titled “Iran in the Global Security Context” and requested permission to send a draft for review. To add credibility, TA453 mentioned the involvement of renowned nuclear security experts it had previously impersonated, along with offering an honorarium. The threat actors deployed a novel infection chain called GorjolEcho, utilizing various cloud hosting providers.
Expanding the Arsenal: Introducing NokNok and GorjolEcho
TA453’s tactics involved employing a diverse range of cloud hosting providers to deliver a new infection chain. This campaign introduced a newly identified PowerShell backdoor, GorjolEcho.
Upon engaging in an email exchange, the target recipient was sent a malicious link leading to a Google Script macro. Execution of this macro directed the recipient to a Dropbox URL hosting a password-encrypted .rar file named “Abraham Accords & MENA.rar.” The .rar archive contained a dropper named “Abraham Accords & MENA.pdf.lnk.” Notably, this deviation from TA453’s typical infection chain involved the use of a .rar archive and an LNK file for malware distribution, instead of VBA macros or remote template injection. Opening the enclosed LNK file triggered the download of additional stages from a cloud hosting provider, eventually leading to the deployment of the GorjolEcho backdoor.
MAC Attack: Exploiting macOS Systems with NokNok
For macOS systems, TA453 employed a second email containing a ZIP archive that concealed a Mach-O binary disguised as a VPN application. This file, an AppleScript, connected to the command and control (C2) server and downloaded a Bash script-based backdoor named NokNok.
The NokNok backdoor, acting as the second stage, established a persistent presence on the system. It generated a unique system identifier by combining the operating system name, hostname, and a random number. This identifier was then encrypted and base64 encoded before being used as the payload of an HTTP POST request to library-store.camdvr[.]org. The script continued to loop indefinitely, posting every two seconds, and responded to specific triggers, terminating upon receiving “KillKill” or executing the content of the response as a command when receiving “ModuleName.”
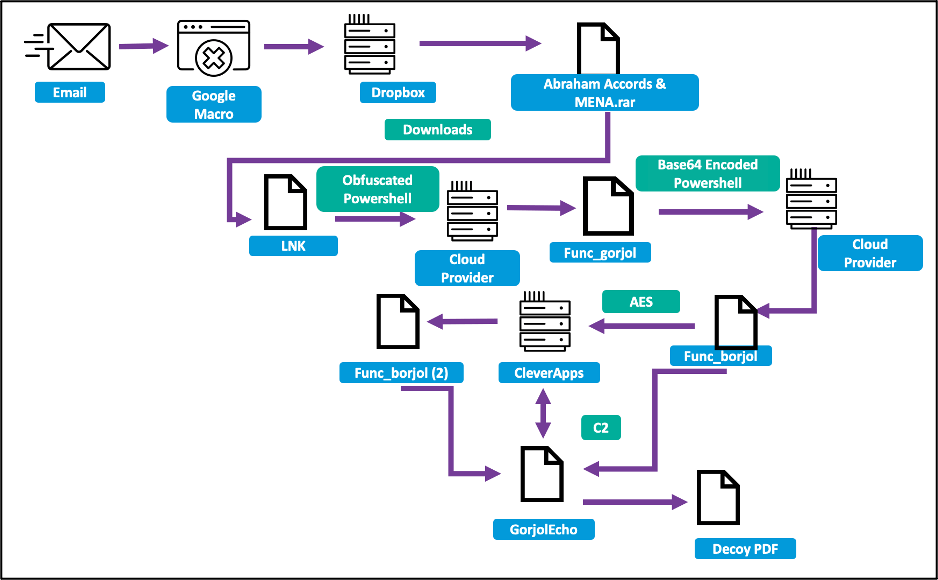
Unraveling the Connections: GorjolEcho and NokNok
Security researchers at Proofpoint identified NokNok as a highly probable port or evolution of the GorjolEcho backdoor, serving as TA453’s initial foothold in intrusion attempts.
NokNok exhibited a modular structure, consisting of four modules designed to gather information on running processes, installed applications, and system metadata. The backdoor achieved persistence through the use of LaunchAgents.
The Puzzle Comes Together: Code Similarities and Clustering
Evidence suggests that TA453 likely operates additional espionage-focused modules for both GorjolEcho and NokNok. The observed modules within NokNok closely resemble the functionalities of the GhostEcho (CharmPower) modules identified by Check Point.
The presence of shared code elements, such as the reuse of the “Stack=Overflow” variable and similar logging syntax, further supports the connection. Notably, Google’s Threat Analysis group attributed some of the code overlaps to Charming Kitten, and certain aspects of NokNok’s functionality bear resemblance to Charming Kitten Mac malware discovered in early 2017.
Conclusion
In conclusion, TA453, a nation-state actor with ties to various groups, has unleashed a formidable malware campaign targeting both Windows and macOS systems. Their adaptive tactics, shift to LNK infection chains, and the introduction of GorjolEcho and NokNok backdoors highlight their ability to evolve and penetrate secure environments.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






