During the discovery phase of a vulnerability assessment or penetration testing it is almost certain that you will utilize the infamous tool nmap.
You may want to pair it with WebMap. WebMap is a web dashboard for your nmap scans. This tool, which is free, can provide you with more management capabilities of your scan results.
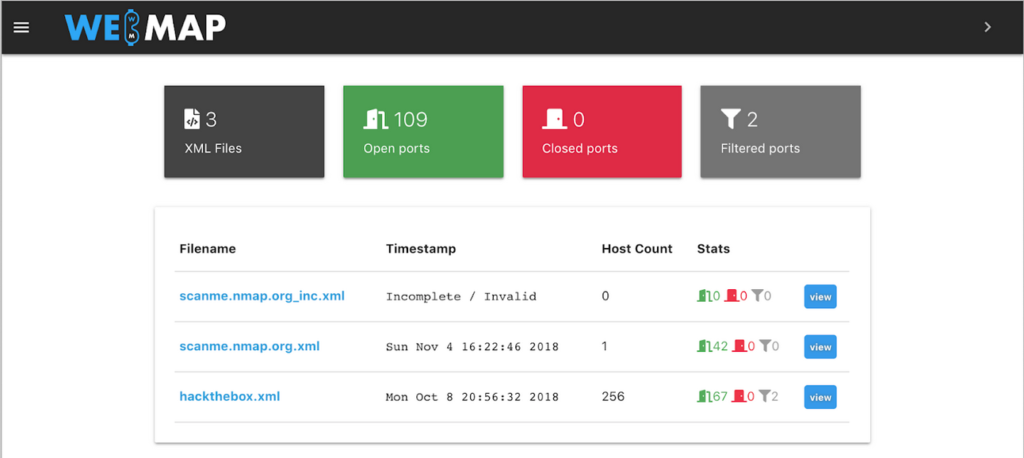
How to Use WebMap
First, create a folder under /tmp:
mkdir /tmp/webmapThen you may run WebMap on docker using the following command:
docker run -d \
--name webmap \
-h webmap \
-p 8000:8000 \
-v /tmp/webmap:/opt/xml \
rev3rse/webmap /run.shThe container will be built along with its dependencies. You may then access the web interface by navigating to http://localhost:8000
You will need to generate a token to access the web interface by running:
docker exec -ti webmap /root/token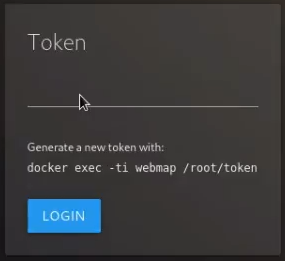
Load your existing nmap XML output files
If you already have some XML files from previous scans you may copy them under /tmp/webmap and those will appear in the dashboard. If you plan to run a new scan and want the XML output file to be available to WebMap directly, you may run:
nmap -sT -A -T4 -oX /tmp/webmap/outfile.xml 192.168.0.0/24WebMap Interface
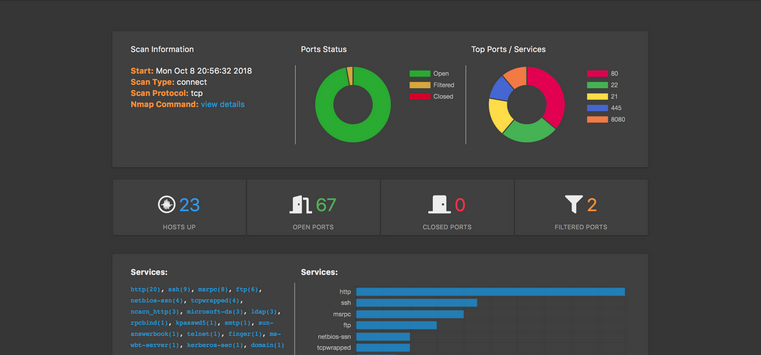
The main dashboard of WebMap will show information like:
- Start date and time of the nmap scan
- scan type
- Port Status (Open, Filtered, Closed)
- Top Ports and Services
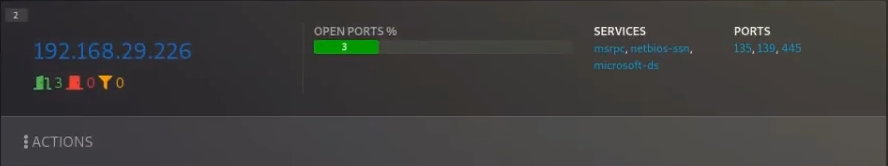
For each host discovered you may add labels like “Vulnerable”, “Critical”, “Warning”, “Checked” and insert any notes for later when you would want to revisit this host.
WebMap gives you the ability to easily generate PDF reports. Simply click the “PDF REPORT” and the PDF will be generated and shown on your browser.
You may also check for CVE and Exploits again, directly through the web interface:

“Network View” gives you a graphical representation of the topology discovered during the nmap scan. Something similar to zenmap’s feature.
Enjoy!
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.





