
Researchers from Cisco Talos Intelligence found that hackers are using public cloud providers like Azure and AWS to spread RATs.
These cloud services allow them to setup their infrastructure with minimal time and makes it more difficult to track them down.
October 2021 Malicious Campaign
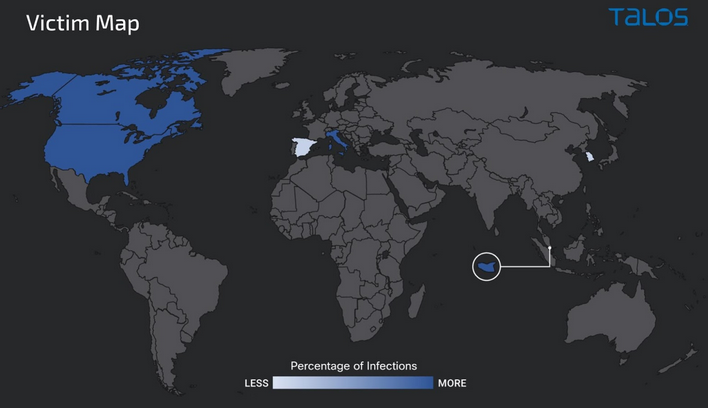
Cisco Talos discovered a malicious campaign in October 2021 delivering variants of Nanocore, Netwire and AsyncRATs targeting user’s information. The victims of this campaign are primarily distributed across the United States, Italy and Singapore.
The actor used complex obfuscation techniques in the downloader script. Each stage of the deobfuscation process results with the decryption methods for the subsequent stages to finally arrive at the actual malicious downloader method.
The actor is using the DuckDNS dynamic DNS service to change domain names of the C2 hosts.
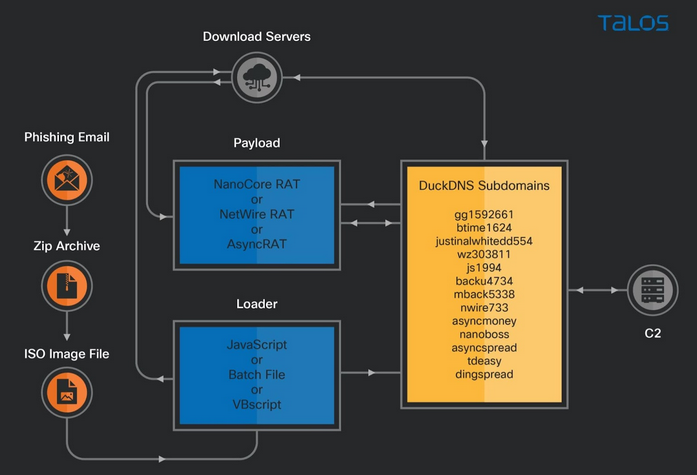
The actor in this campaign maintains a distributed infrastructure consisting of download servers, command and control servers, and malicious subdomains. The downloading servers are hosted on Microsoft Azure and AWS cloud services.
Some of the download servers are running the Apache web server application. The HTTP servers are configured to allow the listing of open directories that contain variants of NanocoreRATs, Netwire RAT and AsyncRATs malware.
The Initial Infection Vector
The initial infection vector is a phishing email with a malicious ZIP attachment.
These ZIP archive files contain an ISO image with a malicious loader in the form of JavaScript, a Windows batch file or Visual Basic script. When the initial script is executed on the victim’s machine, it connects to a download server to download the next stage, which can be hosted on an Azure Cloud-based Windows server or an AWS EC2 instance.
Delivering the Malware Payload
To deliver the malware payload, the actor registered several malicious subdomains using DuckDNS, a free dynamic DNS service. The malware families associated with this campaign are variants of the Netwire, Nanocore and AsyncRAT remote access trojans.
Malicious Domains Used in the Attack
DuckDNS is a free dynamic DNS service providing a public DNS server service allowing the user to create subdomains and maintain the records using the DuckDNS scripts. The actor has created malicious DuckDNS subdomains to deliver malware in this campaign. Some of the actor-controlled malicious subdomains resolve to the download server on Azure Cloud while others resolve to the servers operated as C2 for the remote access trojan payloads.
- gg1592661[.]duckdns[.]org
- btime1624[.]duckdns[.]org
- justinalwhitedd554[.]duckdns[.]org
- wz303811[.]duckdns[.]org
- js1994[.]duckdns[.]org
- backu4734[.]duckdns[.]org
- www[.]backu4734[.]duckdns[.]org
- mback5338[.]duckdns[.]org
- nwire733[.]duckdns[.]org
- asyncmoney[.]duckdns[.]org
- nanoboss[.]duckdns[.]org
- asyncspread[.]duckdns[.]org
- tdeasy[.]duckdns[.]org
- dingspread[.]duckdns[.]org
- asyncpcc[.]duckdns[.]org
- jw9428875.duckdns[.]org
- meunknown.duckdns[.]org
- yuri101.duckdns[.]org
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






