Phishing campaigns that use COVID-19 as a hook are still on the rise. Hackers are increasingly using vaccine-related emails in their targeted spear-phishing attacks.
Lately, threat actors are impersonating Pfizer to steal business and financial information from victims. This campaign took place around August 15 to December 13 2021 in a run for request for quotation (RFQ) scams.
Originating Domains Looked Legitimate
The phishing emails themselves originated from a set of domains which looked like they are controlled by Pfizer:
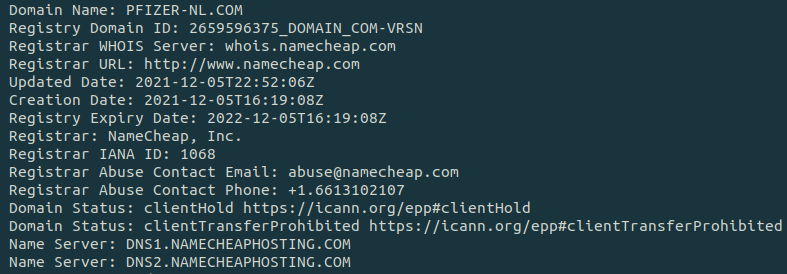
- pfizer-nl[.]com
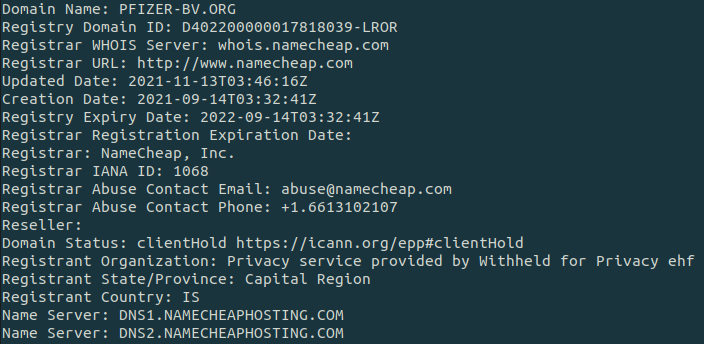
- pfizer-bv[.]org
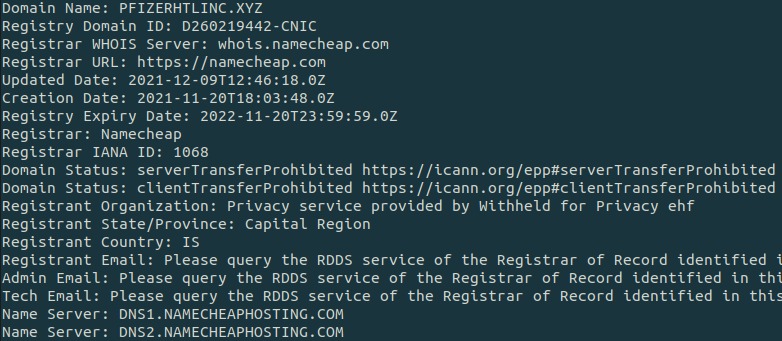
- pfizerhtlinc[.]xyz
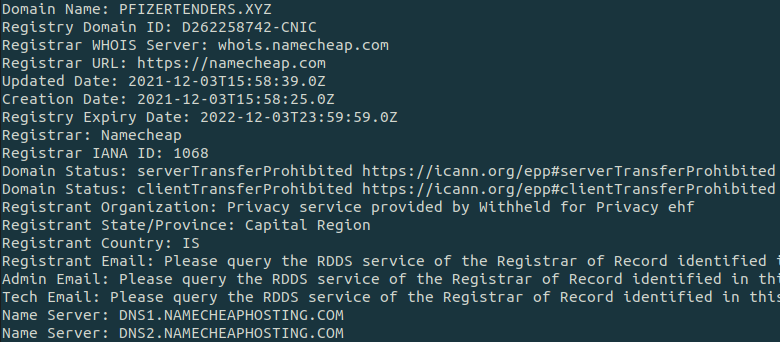
- pfizertenders[.]xyz
The domains were recently created, as little as few days prior to being used in the phishing campaigns.
The domains were registered through namecheap.com, which accepts cryptocurrencies as a payment method, allowing the actors to remain anonymous.
Attackers sent some of the Pfizer-impersonating emails from email accounts set up at Gmail, Outlook, and Ziggo.
Sample Phishing Emails
INKY reported that the subject lines included in the phishing emails included:
- Request For Quotation
- Pfizer Request For Quotation
- RFQ
- RFQ URGENT
- RFQ URGENT CARE
- Request for Supply Invitation
- Invitation to Bid
Here are two sample emails requesting the recipient to bid.
In both cases, the equipment involved had a substantial monetary value.
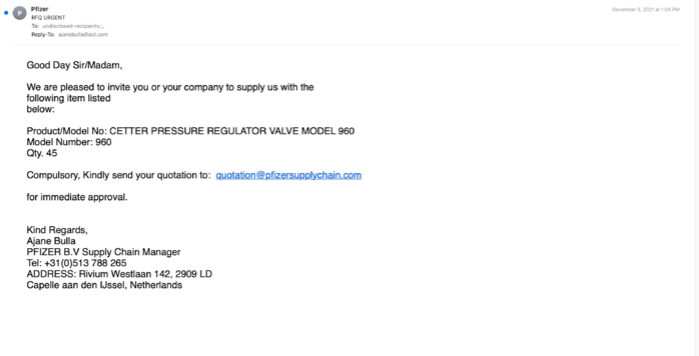
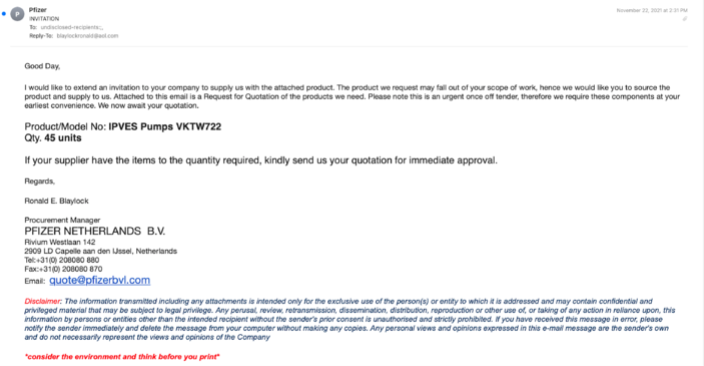
They both claimed that Pzifer was requesting quotes for various industrial engineering supplies, and both had PDF attachments that impersonated Pfizer.
The PDF was three pages long and had a few inconsistencies (e.g., different due dates on different pages), but, in general, looked pretty good. The discussion of payment methods and terms set the recipient up for the idea that they would have to share banking details at some point.
The PDF does not contain links that drop malware or phishing URLs that could generate flags in email security tools and does not contain any typographical errors that make the fraud obvious.

While the exact objective of the campaign is unclear, the fact that the payment terms are included in the PDF is an indication that threat actors will ask the recipient to share their banking details at some point.
If payment information is provided, attackers could use it in future BEC campaigns against the company’s target customers.