While performing penetration testing against your target one of the things you will look for is if you can perform a DNS Zone transfer.

What is DNS Zone Transfer
DNS zone transfers use the AXFR protocol to replicate DNS records across DNS servers. If you do not protect your name servers, attackers can get information about all your hosts with AXFR.
AXFR offers no authentication, so any client can ask a DNS server for a copy of the entire zone. This means that unless some kind of protection is introduced, an attacker can get a list of all hosts for a domain, which gives them a lot of potential attack vectors.
Lab Time

Installation
I recommend you download the Vulhub repository which you can use for more tests on more attacks to different vulnerabilities on your local environment in the future.
git clone https://github.com/vulhub/vulhubBy navigating inside the folder vulhub you will see the entire collection of vulnerable docker environments. In this article we will focus on dns-zone-transfer.
Get into the directory:
cd dns-zone-transferBuild the image and start the container:
docker-compose up -dIf you dont have the docker-compose installed, run:
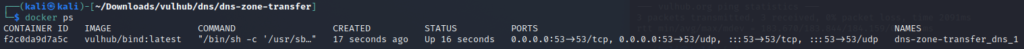
sudo apt install docker-composeCheck your running containers and you will see that the container exposing port 53 (DNS) is running “docker ps“:
Exploit the Vulnerability
Open up your terminal and run the dig command against this DNS server we just installed on a docker container.
*dig is a network administration command-line tool for querying the Domain Name System (DNS).
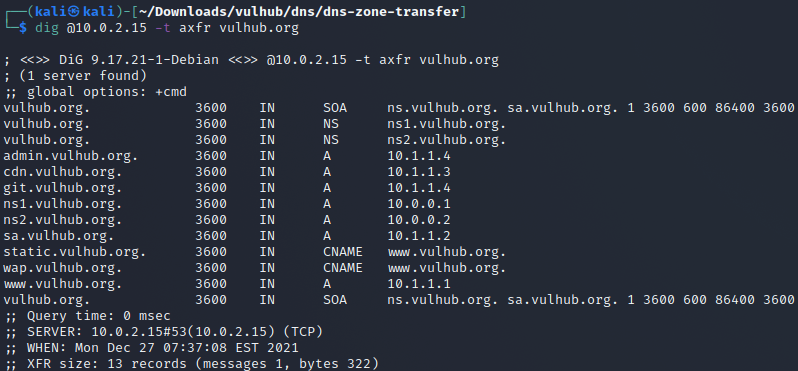
dig @yourIPHere -t axfr vulhub.orgRun this command by adding the IP of the machine to which you installed the docker image. Mine was 10.0.2.15.
By querying the “vulhub.org” zone on the DNS server running on the container, we can see that we can retrieve ALL DNS records.
This means that this DNS server is vulnerable to DNS Zone Transfer.
Other Commands to Test DNS Zone Transfer
Except the dig command, there are other commands and tools you can use to test if a DNS zone trasnfer is possible.
Fierce
A recon tool preinstalled on Kali Linux.
fierce -dns <domain>Host
A command to perform DNS lookups.
host -t axfr <test-url> <name-server>NSLOOKUP
Used very often by network administrators.
>nslookup
>server <name-server>
>set type=any
>ls -d <test-url>DNSRecon
A script that comes preinstalled on Kali Linux.
dnsrecon -d <domain> -t axfrProtect Your DNS Servers
In order to prevent this vulnerability from occurring on your systems, the DNS server should be configured to only allow zone transfers from trusted IP addresses.
You can also use transaction signatures (TSIG) for zone transfers. This helps in preventing IP spoofing efforts.
It is quite rare that you will find DNS servers which are vulnerable to zone transfers. But since you should conduct your tests thoroughly, check every time.
You never know, maybe an admin forgot to secure his DNS server properly.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.





