The “Lazarous Group”, a North Korean APT conducted a spear phishing attack, weaponized with malicious documents that try to lure targets into clicking by using the same “job-opportunities” baloney that the group has done before.
How the Attack Works
The attack starts by executing malicious macros embedded in the Word documents. The word documents seem to be luring the victims about new job opportunities at Lockheed Martin. The documents were named:
- Lockheed_Martin_JobOpportunities.docx
- Salary_Lockheed_Martin_job_opportunities_confidential.doc
After a series of injections, the malware achieves startup persistence in the victim’s system.
After a target opens the malicious attachments and enables execution of macros, an embedded macro drops a WindowsUpdateConf.lnk file in the startup folder and a DLL file (wuaueng.dll) in a hidden Windows/System32 folder. LNK files are Windows shortcut files, as in, pointers to original files in Windows.
Next, the .LNK file is used to launch the WSUS / Windows Update client – wuauclt.exe, a legitimate process file popularly known as Windows automatic updates that’s located in C:\Windows\System32 by default. The Update client is used to run a malicious DLL that bypasses security detection.
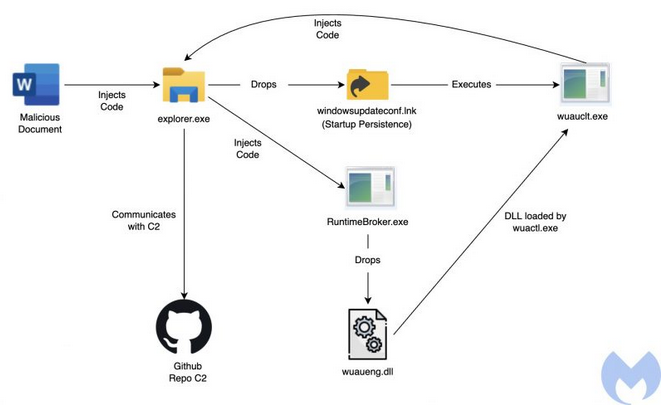
“With this method, the threat actor can execute its malicious code through the Microsoft Windows Update client by passing the following arguments: /UpdateDeploymentProvider, Path to malicious DLL and /RunHandlerComServer argument after the DLL,” the researchers explained.
The Attackers Used Github as C2
It is rare for attackers to utilize github as C2.
Using Github as a C2 has its own drawbacks but it is a clever choice for targeted and short term attacks as it makes it harder for security products to differentiate between legitimate and malicious connections.
Operation: Dream Job
Read more details on the Operation: “Dream Job” which was also used in the recent past by North Korean threat actors here.
The “dream job” is supposedly sent on behalf of some of the most prominent defense and aerospace companies in the US, including Boeing, Lockheed Martin, and BAE.
The infection and infiltration of target systems had been carried out through a widespread and sophisticated social engineering campaign, which included: reconnaissance, creation of fictitious LinkedIn profiles, sending emails to the targets’ personal addresses, and conducting a continuous dialogue with the target – directly on the phone, and over WhatsApp.
Upon infection, the attackers collected intelligence regarding the company’s activity, and also its financial affairs, probably in order to try and steal some money from it.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.