On Sunday night, the email account of Namecheap, a domain registrar, was breached, resulting in a flood of phishing emails that targeted MetaMask and DHL recipients.
Phishing Campaigns and SendGrid
The phishing campaigns began at around 4:30 PM ET and were sent from SendGrid, an email platform historically used by Namecheap for renewal notices and marketing emails. As a result, Namecheap CEO Richard Kirkendall confirmed that the account was compromised, and they disabled email through SendGrid while investigating the issue.
Kirkendall also said that they believe the breach may be related to a December CloudSek report on the API keys of Mailgun, MailChimp, and SendGrid being exposed in mobile apps.
Flood of Impersonating Emails
The phishing emails sent in this campaign impersonated either DHL or MetaMask.
The DHL phishing email pretends to be a bill for a delivery fee required to complete the delivery of a package with embedded links that lead to a phishing page attempting to steal the target’s information.
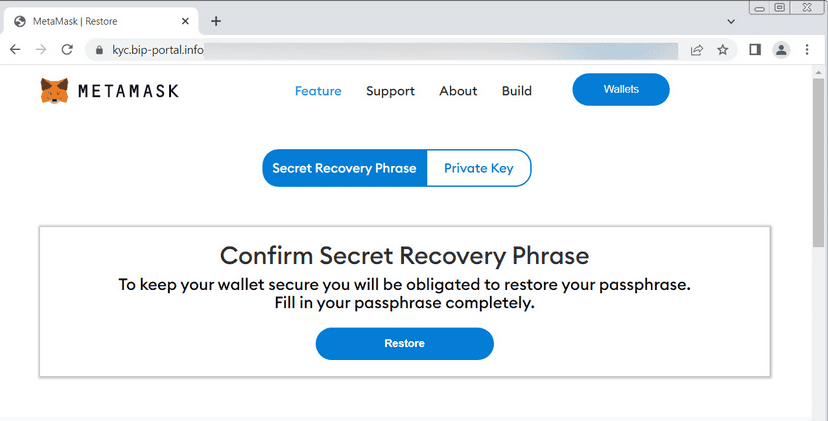
MetaMask Phishing Email
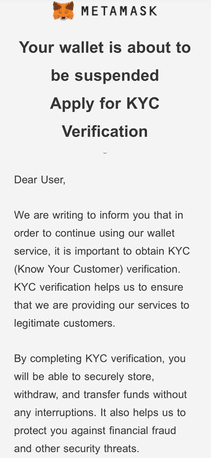
“We are writing to inform you that in order to continue using our wallet service, it is important to obtain KYC (Know Your Customer) verification. KYC verification helps us to ensure that we are providing our services to legitimate customers,” reads the MetaMask phishing email.
“By completing KYC verification, you will be able to securely store, withdraw, and transfer funds without any interruptions. It also helps us to protect you against financial fraud and other security threats.“
“We urge you to complete KYC verification as soon as possible to avoid suspension of your wallet.“
The email contains a marketing link from Namecheap (https://links.namecheap.com/) that redirects the user to a phishing page pretending to be MetaMask.
Once a user provides either the recovery phrase or private key, the threat actors can use them to import the wallet to their own devices and steal all the funds and assets.
Namecheap Blames “Upstream System”
Namecheap published a statement Sunday night stating that their systems were not breached but rather it was an issue at an upstream system that they use for email.
“We have evidence that the upstream system we use for sending emails (third-party) is involved in the mailing of unsolicited emails to our clients. As a result, some unauthorized emails might have been received by you,” reads a statement issued by Namecheap.
“We would like to assure you that Namecheap’s own systems were not breached, and your products, accounts, and personal information remain secure.“
While Namecheap did not state the name of this upstream system, the CEO of Namecheap previously tweeted that they were using SendGrid, which is also confirmed in the phishing emails’ mail headers.
Impact on Namecheap’s Clients
The breach and subsequent phishing campaigns caused alarm and frustration among Namecheap’s clients. Many took to Twitter to report the issue and express their concerns about the security of their personal information and cryptocurrency wallets.
Namecheap has since apologized for the incident and assured clients that they take the security of their products, accounts, and personal information very seriously. However, the incident underscores the ongoing threat that phishing attacks pose to both individuals and organizations.
Recommendations for Recipients
If you received either a DHL or MetaMask phishing email tonight from Namecheap, immediately delete it and do not click on any links.

Investigations Ongoing
After the phishing incident, Namecheap says they stopped all emails, including two-factor authentication code delivery, trusted devices’ verification, and password reset emails, and began investigating the attack with their upstream provider. Services were restored later that night at 7:08 PM EST.
Conclusion
The breach of Namecheap’s email account and subsequent phishing campaigns highlight the importance of robust security measures for both individuals and organizations.
As the threat of phishing attacks continues to evolve, it is essential to remain vigilant and take steps to protect personal and sensitive information. As investigations into this incident continue, it remains to be seen what additional measures Namecheap and other organizations will take to safeguard against phishing attacks and other forms of cyber threats.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






