
Indian hackers infected themselves with their own RAT. The APT group called “Patchwork” scored an embarrassing own goal during their recent campaign to drop a variant of the “BADNEWS” remote administration trojan (RAT) called “Ragnatela“.
Who Is Patchwork
Patchwork is a cyberespionage group that was first observed in December 2015. While the group has not been definitively attributed, circumstantial evidence suggests the group may be a pro-Indian or Indian entity. Patchwork has been seen targeting industries related to diplomatic and government agencies.
Much of the code used by this group was copied and pasted from online forums. Patchwork was also seen operating spearphishing campaigns targeting U.S. think tank groups in March and April of 2018.
Patchwork, like some other East Asian APTs is not as sophisticated as their Russian and North Korean counterparts.
What Is Ragnatela Malware
Ragnatela is a new variant of the “BADNEWS” RAT and was built sometime in late November 2021. The capabilities of this malware variant are:
- Executing commands via cmd
- Capturing screenshots
- Logging Keystrokes
- Collecting list of all the files in victim’s machine
- Collecting list of the running applications in the victim’s machine at a specific time periods
- Downing addition payloads
- Uploading files
The Attack
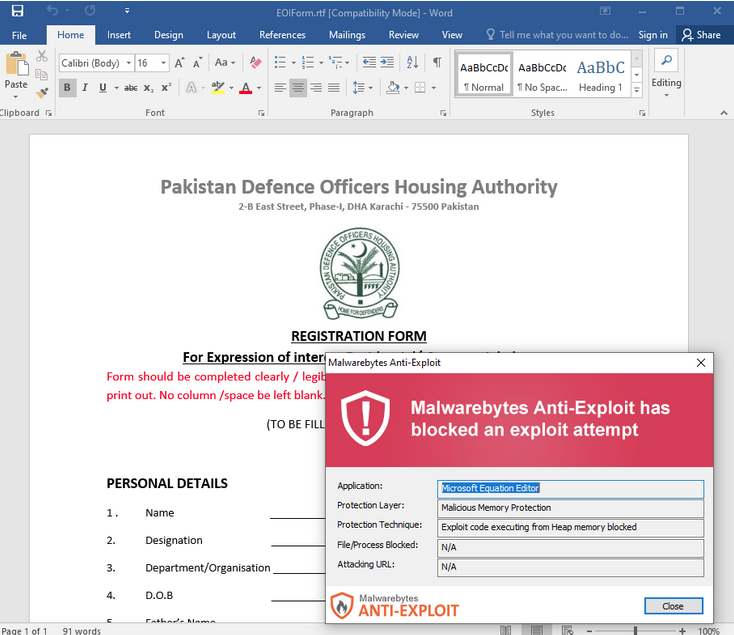
In order to distribute the RAT onto victims, Patchwork lures them with documents impersonating Pakistani authorities. For example, a document called EOIForm.rtf was uploaded by the threat actor onto their own server.
That file contains an exploit (Microsoft Equation Editor) which is meant to compromise the victim’s computer and execute the final payload (RAT). That payload is stored within the RTF document as an OLE object.
The Discovery
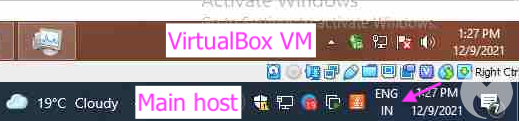
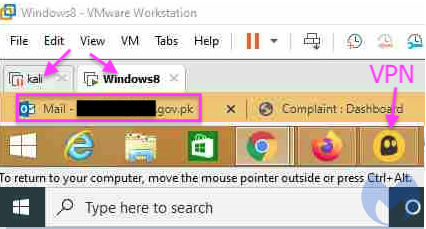
Malwarebytes Labs gathered the information which proved that the Patchwork’s Indian hackers indeed scored an embarrassing own goal. They managed to get captured keystrokes and screenshots of the group’s computers and virtual machines.
“Ironically, all the information we gathered was possible thanks to the threat actor infecting themselves with their own [remote access trojan], resulting in captured keystrokes and screenshots of their own computer and virtual machines,” Malwarebytes Threat Intelligence Team said in their report.
Malwarebytes got a better understanding about the attackers, such as their use of virtual machines and VPNs to develop and push updates and check on their victims.

Patchwork’s Victims
Malwarebytes managed to gain visibility on victims that were successfully compromised:
- Ministry of Defense- Government of Pakistan
- National Defense University of Islam Abad
- Faculty of Bio-Science, UVAS University, Lahore, Pakistan
- International center for chemical and biological sciences
- HEJ Research institute of chemistry, International center for chemical and biological sciences, univeristy of Karachi
- SHU University, Molecular medicine
- Themselves




