
Google has released an update for its Chrome browser that includes eleven security fixes, one of which has been reportedly exploited in the wild. The vulnerability that is reported as being exploited in the wild has been assigned CVE-2022-0609.
The Vulnerability
The researchers who found and reported the flaw are Adam Weidemann and Clément Lecigne of Google’s Threat Analysis Group (TAG).
The vulnerability is described as a Use-after-free (UAF) vulnerability in the Animation component.
UAF is a type of vulnerability that is the result of the incorrect use of dynamic memory during a program’s operation.
If, after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to manipulate the program.
Referencing memory after it has been freed can cause a program to crash, use unexpected values, or execute code.
In this case, when the vulnerability is exploited, this can lead to corruption of valid data and the execution of arbitrary code on affected systems.
As a result, a remote attacker can create a specially crafted web page, trick the victim into visiting it, trigger the UAF vulnerability and execute arbitrary code on the target system.
How to Protect Yourself
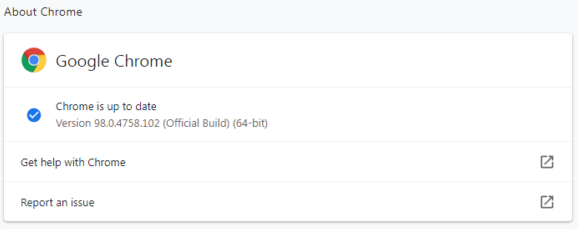
Update your chrome browser to version 98.0.4758.102as soon as possible
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.





