Abdelhamid Naceri, a security researcher has published a public exploit on Github that allows a low privileged user on all client and server windows operating systems, to gain administrative rights.

According to the researcher, even with the latest November 2021 patches elevation of privileges using this exploit is possible.
Naceri during his analysis of CVE-2021-41379 found that the initial issue was not patched correctly by Microsoft.
Naceri stated that:
I have also made sure that the proof of concept is extremely reliable and doesn’t require anything, so it works in every attempt. The proof of concept overwrite Microsoft Edge elevation service DACL and copy itself to the service location and execute it to gain elevated privileges.
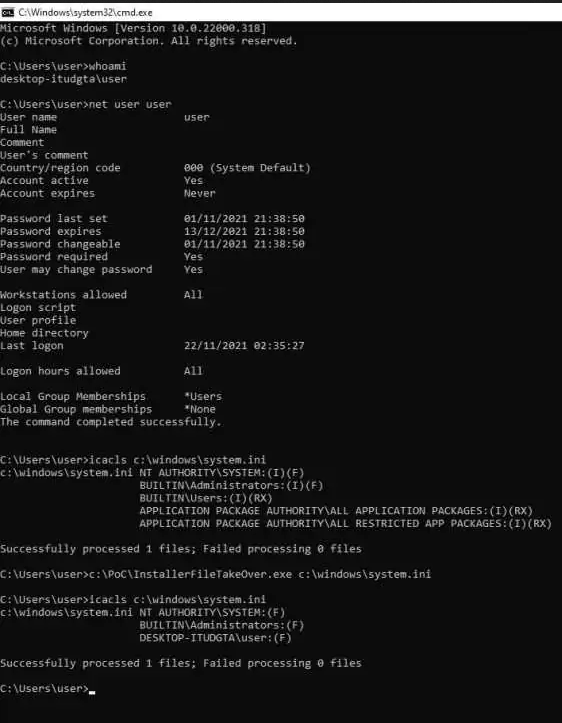
While this technique may not work on every installation, because windows installations such as server 2016 and 2019 may not have the elevation service. I deliberately left the code which take over file open, so any file specified in the first argument will be taken over with the condition that SYSTEM account must have access to it and the file mustn’t be in use. So you can elevate your privileges yourself.
Why Wasnt the Vulerability Reported Before Publishing?
Bleeping computer asked Naceri why he did not report the vulnerability to Microsoft before publication. Naceri responded that it is a reaction to Microsoft cutting bug bounties for reported vulnerabilities.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.





