With data breaches continuing to occur at an alarming rate, protecting sensitive data is critical for all businesses. As organizations store more data than ever before (on-premises and in the cloud), adequate database security becomes increasingly important. For many organizations, this security may not go further than access control.
Those who want stronger protection for sensitive data turn to an extra layer of protection against internal and external threats: database encryption.
What is database encryption?
Database encryption is the process of using an algorithm to turn data in a database into “ciphertext” (unreadable text). You must decrypt the text using an algorithmically generated encryption key.
Encrypting data renders information unreadable when accessed without proper authorization. The only people that can decrypt it are you or anyone else authorized who has the decryption keys.
Types of Data Encryption
Data encryption is typically of two types:
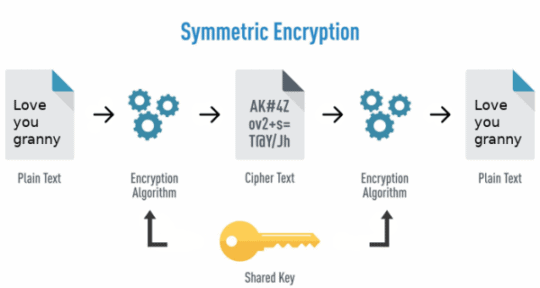
- Symmetric encryption: Uses a single symmetric key to both encrypt and decrypt data. The key is shared with all authorized users to allow data access.
- Asymmetric encryption: Uses two separate keys to encrypt and decrypt data. One key is made public (shared with everyone), and the other is kept private (known only to the key’s generator). The public key is used to encrypt data, and the private key is used to decrypt it.
Database encryption methods
When it comes to applying encryption to databases, you can consider different encryption methods based on the encryption targets:
- File-Level encryption
- Cell-Level encryption
- Column-Level encryption
- Row-Level encryption
- Table space-level encryption
In File-level encryption, individual database files are encrypted as a whole to restrict unauthorized access. However, partial encryption of the database can be performed with more specific targets as follows:
Cell-level encryption: Individual cells are encrypted separately, with their own unique keys
Column-level encryption: Individual columns of data are encrypted separately, with each column having the same key for accessing, reading, and writing data within the column
Row-level encryption: Individual rows of data are encrypted separately, with their own unique keys for their cells
Table space-level encryption: Individual tablespaces are encrypted as a whole. Each tablespace has a unique key for all of its contents.
Can Encrypted Data be Hacked?
Yeap! There are multiple ways attackers can compromise data encryption systems:
- Malware on endpoint devices – many endpoint devices have encryption mechanisms such as full disk encryption. Attackers can compromise an endpoint device using malware, and leverage keys on the device to decrypt the data.
- Brute force attacks – attackers commonly try to break encryption by randomly trying different keys. The chances of success are directly related to the size of the key. This is why most encryption standards specify the use of 256-bit encryption keys. However, some encryption systems use weak ciphers which are vulnerable to brute-force attacks.
- Cryptanalysis – this is a technique in which attackers find a weakness in the cipher itself and use it to gain access to data.
- Side-channel attacks – this involves looking for errors or weaknesses in system design, which allow users to decrypt data or prevent it from being encrypted, without breaking the cipher itself.
- Social engineering attacks – possibly the easiest way to hack encrypted data is to use phishing or other social engineering methods to trick a privileged user into providing the key.
- Insider threats – a severe threat to encrypted data is the possibility that a privileged individual will turn against the organization and abuse their privileges to steal data. Insider threats also include negligent users who fail to follow security policies.
This doesn’t mean that you should not encrypt your data-at-rest.
This means that database encryption should be one of your many layers of defense against attackers. You have to make it more difficult for the attacker and less worth his time, to try and bust through many layers to get to encrypted data, which he must dedicate more time to access.
Why is database encryption important?
Security Against Unauthorized Access
There are many security controls to apply in order to protect your information in a defense-in-depth approach. But at the end of the day, having your valuable data encrypted, will be what prevents an unauthorized person from reading them.
Proper encryption on the public cloud is equally important as data can be exposed to a much broader range of threats, such as accidental exposure to the Internet, access by some cloud tenants, and malicious insiders at the cloud provider.
Consumer Trust from a Privacy Safeguard
Database encryption is beneficial to consumers and not only the organization that implements it. Users trust your organization more when they know that their information cannot be read even when the organization suffers a data breach.
Database encryption opens an opportunity for companies to bolster consumer trust by explicitly stating how they encrypt customer data. Although end-users need to take responsibility as well, enterprises can solidify their reputations by emphasizing a commitment to incorporating the latest encryption technologies into their operations.
Encryption Helps you be Compliant with Regulatory Requirements
For regulations, such as the GDPR, there are no explicit requirements for encrypting data, however, “security measures and safeguards” must be put in place to protect the privacy of the data subjects – assuming they are EU citizens.
HIPAA (Health Insurance Portability and Accountability Act of 1996), require that confidential data be encrypted.
If your company deals with security regulations such as PCI DSS, encryption is one of the most critical requirements. All cardholder data must be encrypted using a robust algorithm such as AES-256, and RSA 2048.
Conclusion
Encryption of data-at-rest has become increasingly important and with the help of regulations such as GDPR, HIPAA, and PCI, it tends to be the “norm” for many organizations. Cloud providers and companies developing database management software are making the encryption of databases ever so easy to implement and operate for database administrators and security teams.
Build a solid encryption strategy for both data-in-transit and for data-at-rest because encryption is more than a few clicks of a button. You need to think about encryption key management, and performance among others, and these would become clear when you have a written policy and procedure for the encryption of your sensitive data.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.
