Digital transformation and the optimization of business processes drive organizations to increase and evolve the connectivity of IT and OT environments.
For those unfamiliar with the term “OT”: Operational Technology is hardware and software which are used to monitor and/or control industrial equipment. It is typically used in factories, power and water plants, damns, transportation, vessels etc.
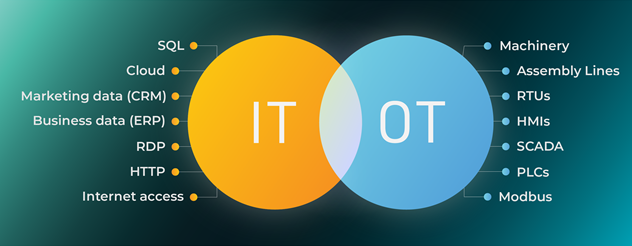
Examples of operational technology are SCADA systems (Supervisory Control and Data Acquisition), DCS (Distributed Control System) and Programmable Logic Controllers (PLCs). RTUs (Remote Terminal Units), Human-Machine Interfaces (HMI), embedded systems and computing technologies, machinery, physical equipment in plants and Variable Frequency Drives (VFDs) also are operational technologies, as are most connected assets in industrial markets.
PLM Systems, MES applications, Safety Automation Systems, Building Management Systems etc. are often categorized as operational technology too. Operational technology field devices include valves, transmitters, switches and actuators.
Greater Connectivity, Greater Exposure to Threats
This inter-connectivity creates huge benefits but also great risks. Not just to systems and information, but to human lives.
IT based technologies such as big data and machine learning in OT, enable innovations towards the management of physical devices in industrial processes and their optimization through remote diagnostics and maintenance.
Securing such devices to protect them from being weaponized and cause harm of human life, is of great importance.
Killware is not Fiction
Malware deployed with the sole purpose to cause physical harm (Killware), even death is not an idea which came out of a SciFi movie or book. Recent events indicate that more and more hackers are out there just to cause harm. Financial damage can be mitigated or undone one way or the other, but killing a human being cannot.
Recent Attacks

At the Oldsmar water treatment plant in Florida, a malicious actor attempted to change chemical mixtures to unsafe levels as part of the water treatment process. While the mass water poisoning issue was corrected before harm could be done, the incident was a wakeup call for water districts everywhere. The attack was not for financial gain but to do harm. [USA Today]
Researchers discovered credentials for the Oldsmar water treatment facility in the massive compilation of data from breaches posted just days before the attack.
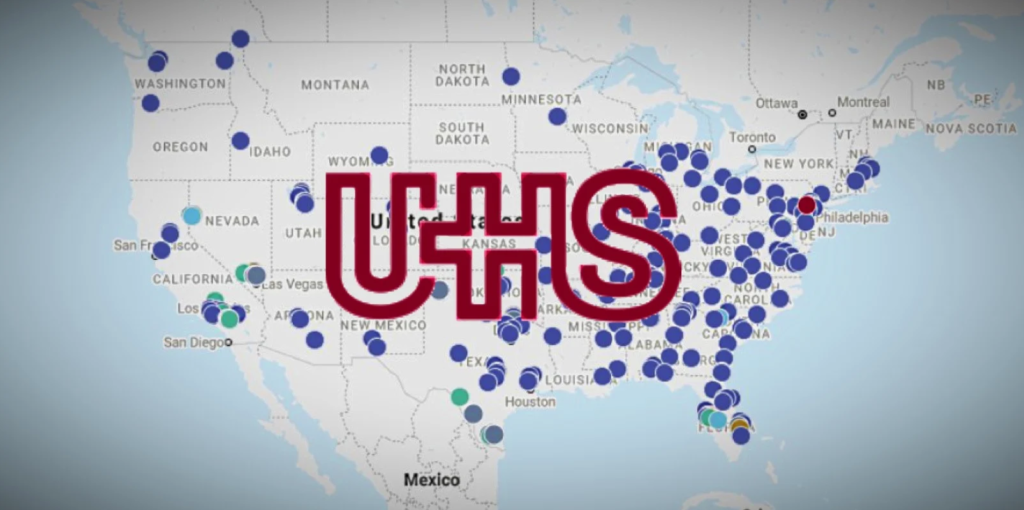
A rash of ransomware attacks on hospitals, such as the nationwide cyber attack on Universal Health Systems, one of the largest healthcare providers with 400 acute care hospitals, behavioral health facilities and ambulatory centers, had to divert patients to neighboring hospitals and cancel or defer critical surgeries, tests and other medical procedures. [USA Today]
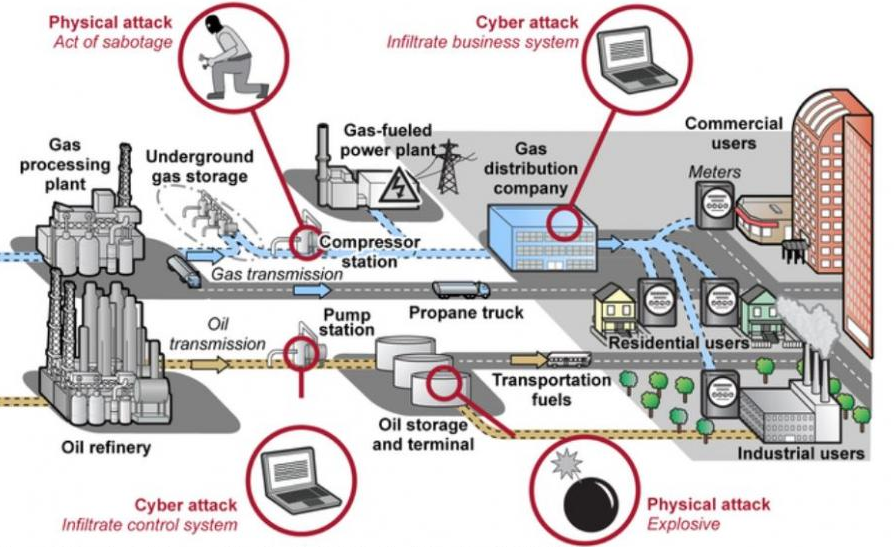
The largest cyberattack on a U.S. oil infrastructure, Colonial Pipeline, impacted computerized equipment managing the pipeline. The company supplies 45% of fuel supplies on the East Coast, transporting 2.5 million barrels each day. The ransomware attack resulted in gas shortages and price surges throughout several states. [Barnes Windley]
In all three examples above the objective of the attacker was to cause harm to humans using killware in the Operational Technology environment. Many similar attacks have been identified since the year 2000, even though they were not called killware back then.
Gartner research suggests that by 2025, cyber attackers will have weaponized operational technology (OT) environments to successfully harm or kill humans.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






