In the treacherous world of cybercrime, a formidable adversary has emerged – Greatness, the insidious Phishing-as-a-Service (PhaaS) platform. Since its inception in mid-2022, this malicious entity has cast a dark shadow over Microsoft 365 users, making phishing attacks alarmingly accessible to even novice cybercriminals. Brace yourself for a chilling account of this powerful threat that preys on unsuspecting victims.
The Emergence of Greatness: Empowering Cybercriminals with Phishing-as-a-Service
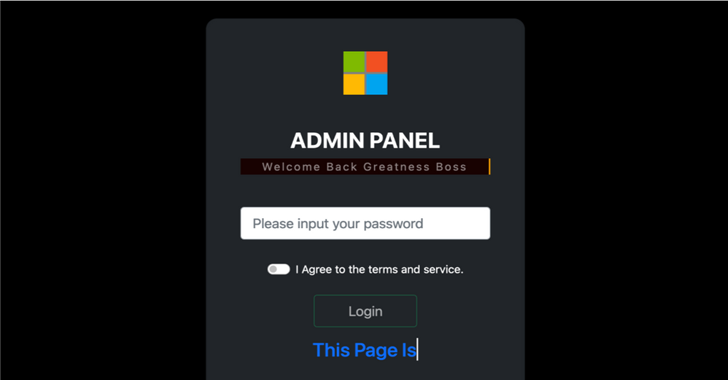
Beware the rise of Greatness, a diabolical Phishing-as-a-Service platform that has unleashed chaos within the realm of Microsoft 365. Unveiled by Cisco Talos researcher Tiago Pereira, this malevolent creation equips its affiliates with a potent arsenal, enabling the creation of deceptively genuine decoy and login pages. With its ability to extract crucial elements from authentic Microsoft 365 login pages, Greatness raises the bar for sophistication and believability.
Deceptive Tactics: The Art of Convincing Decoy Pages
Greatness weaves a web of deceit, constructing meticulously crafted decoy pages that entrap its victims. These malicious replicas, tailored to resemble legitimate Microsoft 365 login pages, lull users into a false sense of security. The ingenious design includes pre-filled email addresses, appropriate company logos, and background images, expertly mimicking the target organization’s authentic login portal. The unwary are unwittingly lured into divulging their confidential information.
Targets and Surge in Activity: Breaching the Defenses of Manufacturing, Healthcare, and Technology Sectors
No industry is safe from the clutches of Greatness. Its malefic grip has tightened around the manufacturing, healthcare, and technology sectors, spreading its venom across the United States, the United Kingdom, Australia, South Africa, and Canada. A worrisome surge in activity during December 2022 and March 2023 serves as a stark reminder of the platform’s insidious reach and growing influence.
Breaking Two-Factor Authentication: Phishing Kits as a Gateway
Phishing kits like Greatness have ushered in an era of unparalleled convenience for threat actors, irrespective of their experience level. These all-in-one tools provide a cost-effective and scalable solution for designing convincing login pages associated with various online services, effectively bypassing the safeguards of two-factor authentication (2FA). The battle for secure access takes a sinister turn as Greatness undermines the trust placed in these protective measures.
The Sinister Attack Chain: Unveiling the Phishing Process
The nefarious campaigns orchestrated by Greatness commence with malicious emails containing HTML attachments. Innocently opening these attachments triggers the execution of obfuscated JavaScript code, redirecting users to landing pages where their email addresses are already populated. Prompted to enter their passwords and MFA codes, victims unknowingly surrender their credentials and time-based one-time passwords (TOTPs) to the clutches of the cybercriminals.
A Deceptive Arsenal: The Power of AiTM Phishing Kit
Greatness boasts the fearsome AiTM phishing kit, a malevolent masterpiece designed to maximize deception. Equipped with an administration panel, this kit empowers affiliates to configure Telegram bots, monitor stolen information, and even construct malicious attachments or links. Its versatility and potency make it a formidable weapon in the hands of cybercriminals.
Evading Detection: The Role of API Key and ‘Man-in-the-Middle’ Attack
Greatness employs sophisticated techniques to elude detection. Each affiliate must possess a valid API key, ensuring that only authorized individuals can access the phishing page. This key also acts as a shield, preventing unwanted IP addresses from infiltrating the operation. Through a devious ‘man-in-the-middle’ attack, the phishing kit and the API collaborate, extracting information from victims and seamlessly submitting it to the genuine Microsoft 365 login page. Usernames, passwords, and even authenticated session cookies become the spoils of this calculated betrayal.
Microsoft’s Defense: Enhancing Two-Factor Authentication Measures
In response to the mounting threat, Microsoft has taken a decisive stance to fortify its defenses. By enforcing number matching in Microsoft Authenticator push notifications, starting May 8, 2023, the company aims to bolster the security of two-factor authentication (2FA) and counter prompt bombing attacks. A critical step forward in safeguarding users’ accounts and preserving their trust.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.
