The rise of cloud environment usage especially Microsoft Azure, has also brought new challenges for CISOs and security professionals. Following best practices will help organizations ensure that their cloud environment is operating a safe and optimal efficiency levels.
Table of Contents
Excessive Access Rights
A common misconfiguration regarding user access control is providing excessive user rights, more than the ones needed to perform their duties. Role Based Access Control facilitates Fine-Grained Access Control to resources hosted on Azure.
Roles can be assigned to different security scopes, such as subscriptions, resource groups, or individual resources (VM, Storage, VNETs). These roles are assigned to Azure AD users, groups, or applications.
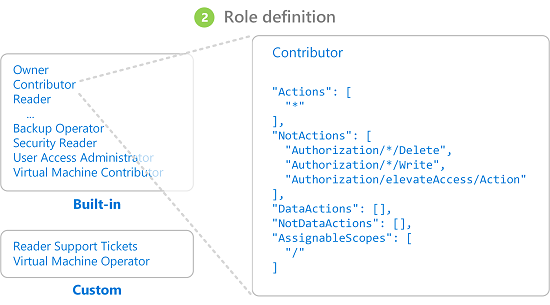
You can also create custom roles with specific permissions and assign roles. Three basic roles exist by default in Azure: owner, contributor, and reader. The owner and contributor roles have full access to all resources in the assigned scope and can provide access to other users. Readers can only view resources.
Make sure that the principle of least privilege is followed when assigning permissions to users. Failing to do so leads to users having excessive access permissions.
Lack of MFA
Azure MFA (Multi-Factor Authentication) should be enabled for users and especially Azure Administrators. It provides an extra layer of security where Administrators are asked for additional authentication via methods like SMS and the Authenticator App.
The recommended way to enable and use Azure AD Multi-Factor Authentication is with Conditional Access policies. Conditional Access lets you create and define policies that react to sign-in events and that request additional actions before a user is granted access to an application or service.
Guest Access Remains Enabled
Azure AD includes the ability to support B2B collaboration, allowing you to invite people from outside your organization to be guest users in your cloud account. Until you have a business reason to do so, you should avoid this option.
As guest accounts are not typically part of your employee on-boarding/off-boarding process they can potentially lay around unnoticed indefinitely leading to potential vulnerability. Worse yet, if you do allow guest access, make sure you turn off their ability to invite other users to your cloud resources. This helps to maintain the “Need-to-Know” and inadvertent access to your data.
No Encryption of Data at Rest and In-Transit
The security of stored data should be enhanced using storage-side encryption and Azure Disk Encryption. Azure Storage Service Encryption can be used to encrypt all data using a Microsoft platform-managed key before saving it to Azure Storage.
All newly created storage accounts will have encryption enabled by default when you enable Azure Storage Encryption. Keep in mind that keys used for encryption are managed by Azure.
Disk encryption for OS and data disks of VMs hosted in Azure is also recommended. It leverages the Azure Key Vault service which stores the keys used for encryption in an HSM module. When you enable disk encryption, its status can be monitored using tools like Azure Security Center or Azure Advisor.
Failure to Monitor Activity Logs
Azure Activity Log provides insight into what’s happening in your Azure subscription in terms of resource access and management. This service tracks all create, update, delete, and action activities performed on resources in the ARM model.
Network Security Groups Overly Permissive Rules
Network Security Groups (NSGs) provide the same functionality as a basic network firewall, with rules to filter the incoming and outgoing traffic from virtual networks and VMs. NSGs contain basic quintuple rules that can be configured to permit or deny traffic to or from a subnet, port or an IP in an Azure network.
You can assign NSGs at two levels: in the NIC card of VM and in subnets in VNet. Organizations often configure NSGs with broader permissions, which can invite unwanted access into their Azure environment.
Exposing Resources to the Public
Azure Blob Storage allows you to grant anonymous read-only access to data in your storage account. It is highly recommended to not provide anonymous access to blob containers until and unless it is strongly desired. You should use a shared access signature token for providing controlled and timed access to blob containers instead.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.
