Table of Contents
Introduction
The importance of penetration testing in cybersecurity
Penetration testing plays a crucial role in cybersecurity for several reasons:
- Identifying Vulnerabilities: A pentest helps security professionals identify vulnerabilities in their systems before malicious actors can exploit them. By discovering these weaknesses, organizations can prioritize their security efforts and remediate high-risk vulnerabilities first.
- Compliance and Regulation: Many industries and governments have established cybersecurity standards and regulations that require organizations to perform regular penetration tests. These tests ensure that companies are adhering to best practices and maintaining a secure environment for their customers and partners.
- Enhancing Security Posture: Pentesting helps organizations better understand their security posture by providing insights into potential attack vectors, misconfigurations, and security gaps. These insights can inform the development of effective security strategies and policies that reduce the likelihood of successful cyberattacks.
- Strengthening Incident Response: A well-executed penetration test can simulate real-world attacks, helping organizations test and improve their incident response processes. By understanding how an attack unfolds, security teams can refine their response plans and enhance their ability to detect, contain, and mitigate breaches.
- Building Customer Trust: Demonstrating a commitment to cybersecurity through regular penetration tests can help organizations build trust with their customers, partners, and stakeholders. By proactively addressing security concerns, businesses can reassure their clients that their sensitive data is well-protected.
A brief overview of pentest frameworks and their role in assessing vulnerabilities
Pentest frameworks serve as a foundation for conducting systematic and efficient penetration tests. These tools streamline the testing process by offering a comprehensive suite of pre-built testing modules, techniques, and automation capabilities designed to uncover security vulnerabilities in a wide range of systems, networks, and applications.
By providing a structured approach to penetration testing, pentest frameworks allow security professionals to focus on analyzing and remediating identified weaknesses rather than getting bogged down in the manual and time-consuming aspects of the testing process. As a result, pentest frameworks play a pivotal role in enabling organizations to assess their security posture, prioritize vulnerabilities, and take proactive measures to safeguard their digital assets against potential cyber threats.
The Early Days of Pentest Frameworks
Pre-framework Era: Manual Penetration Testing
Before the dawn of pentest frameworks, security professionals largely relied on manual penetration testing to assess their systems’ vulnerabilities. In this era, testers had to individually identify and exploit weaknesses using a variety of ad-hoc tools, scripts, and techniques.
This highly manual and time-consuming process often led to inconsistent results, as the quality and effectiveness of the testing heavily depended on the skill level and expertise of the individual tester. Additionally, manual testing was prone to human error, and critical vulnerabilities could be overlooked due to the sheer complexity of modern systems and networks.
The need for a more standardized, repeatable, and efficient approach to penetration testing became apparent, paving the way for the development of the first pentest frameworks that would revolutionize the cybersecurity landscape.
In summary, the challenges security professionals faced when conducting manual penetration testing are:
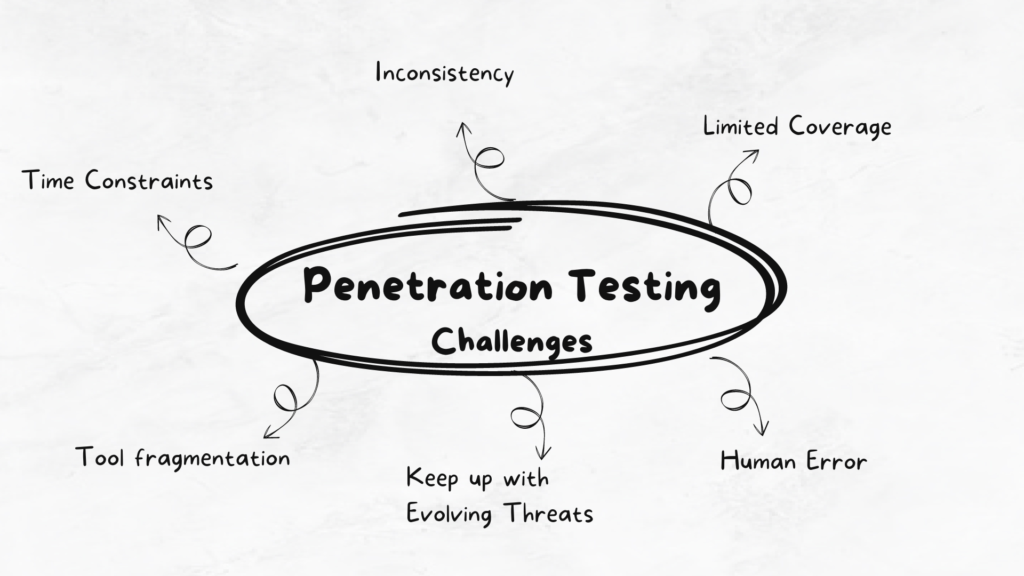
- Time Constraints: The manual nature of penetration testing often meant that security professionals had to invest a significant amount of time in identifying, exploiting, and documenting vulnerabilities. As a result, the testing process could be slow and labor-intensive, which in turn limited the frequency and scope of tests.
- Inconsistency: With no standardized approach to penetration testing, results could vary greatly depending on the tester’s skill level and expertise. This lack of consistency made it difficult for organizations to measure the effectiveness of their security efforts or compare results across multiple tests.
- Limited Coverage: Due to time constraints and the complexity of modern systems, manual penetration testing could only cover a limited portion of an organization’s infrastructure, leaving potential vulnerabilities undiscovered.
- Human Error: Relying on human intuition and expertise increased the likelihood of errors and oversights during the testing process. Critical vulnerabilities could be missed or incorrectly assessed, leading to a false sense of security.
- Tool Fragmentation: Security professionals had to work with a disparate collection of tools and scripts, which often lacked interoperability and required significant manual effort to integrate effectively.
- Difficulty in Keeping Up with Evolving Threats: The rapidly changing landscape of cybersecurity threats and attack techniques made it challenging for security professionals to stay up-to-date and adapt their manual testing methods accordingly.
These challenges underscored the need for a more efficient, standardized, and comprehensive approach to penetration testing, ultimately leading to the development of pentest frameworks that would revolutionize the way security professionals assessed vulnerabilities in their systems.
The need for a standardized approach to vulnerability assessment
As the challenges of manual penetration testing became increasingly apparent, the cybersecurity industry recognized the need for a more systematic, efficient, and consistent approach. This led to the development of the first pentest frameworks, which aimed to address the limitations and issues associated with manual testing.
- Pioneering Pentest Frameworks: In the early stages, pentest frameworks such as Metasploit, Nessus, and Core Impact emerged as some of the first comprehensive solutions. These tools provided security professionals with a structured platform for conducting penetration tests and assessing vulnerabilities in a more organized manner.
- Centralization and Standardization: The first pentest frameworks brought together a wide range of pre-built testing modules, scripts, and tools under a single, unified platform. This consolidation not only simplified the testing process but also helped establish standardized methodologies and best practices, resulting in more consistent and reliable test results.
- Automation and Efficiency: By automating various aspects of the testing process, such as vulnerability scanning, exploit development, and payload execution, the early pentest frameworks greatly reduced the time and effort required to conduct comprehensive penetration tests. This enabled security professionals to focus on higher-level analysis and remediation, ultimately improving the overall effectiveness of their cybersecurity efforts.
- Community-Driven Development: Many of the initial pentest frameworks were open-source projects, which allowed security professionals to collaborate, share their expertise, and contribute new modules, tools, and techniques. This community-driven approach fostered rapid innovation and helped the frameworks evolve to address the ever-changing landscape of cybersecurity threats.
The emergence of the first pentest frameworks marked a significant milestone in the field of cybersecurity. By providing a more structured, efficient, and standardized approach to penetration testing, these early tools revolutionized the way security professionals assessed vulnerabilities and played a crucial role in shaping the future of cybersecurity.
The Emergence of the First Pentest Frameworks
Notable early frameworks
Some of the most notable early frameworks include:
- Metasploit: Launched in 2003 by HD Moore, Metasploit quickly became one of the most widely used pentest frameworks in the cybersecurity community. It offered a comprehensive collection of pre-built modules for vulnerability scanning, exploit development, and payload execution. As an open-source project, Metasploit encouraged community contributions and evolved rapidly to keep pace with the changing threat landscape.
- Nessus: Developed by Renaud Deraison in 1998, Nessus is a well-known vulnerability scanner that played a crucial role in the early days of pentest frameworks. It provided security professionals with an efficient means of identifying and assessing vulnerabilities across a wide range of systems and networks. Over time, Nessus has evolved into a comprehensive vulnerability management platform, offering features such as patch management, compliance checking, and configuration auditing.
- Core Impact: Introduced in the early 2000s by Core Security Technologies, Core Impact was one of the first commercial penetration testing frameworks. It offered a robust suite of modules and capabilities, including automated vulnerability scanning, exploit development, and post-exploitation actions. While it came with a high price tag, Core Impact quickly gained a reputation for its powerful features and ease of use, attracting many large enterprises and government organizations as customers.
- Nmap: Created by Gordon Lyon (Fyodor) in 1997, Nmap (Network Mapper) is a popular open-source network scanning tool that has become an essential component of many pentest frameworks. While not a complete framework in itself, Nmap’s powerful capabilities for network discovery, port scanning, and service enumeration have made it a vital tool for security professionals in the early stages of penetration testing.
- OpenVAS: Originating as a fork of the Nessus project in 2005, OpenVAS (Open Vulnerability Assessment System) emerged as a powerful open-source vulnerability scanning and management platform. By offering a comprehensive suite of tools and capabilities, OpenVAS quickly became a popular choice for organizations seeking a cost-effective and flexible solution for vulnerability assessment.
These early pentest frameworks laid the foundation for the future development of more advanced and comprehensive cybersecurity testing platforms. By offering a more structured, efficient, and standardized approach to penetration testing, these pioneering tools have played a pivotal role in shaping the field of cybersecurity and setting the stage for the next generation of pentest frameworks.
How these early tools transformed the cybersecurity landscape
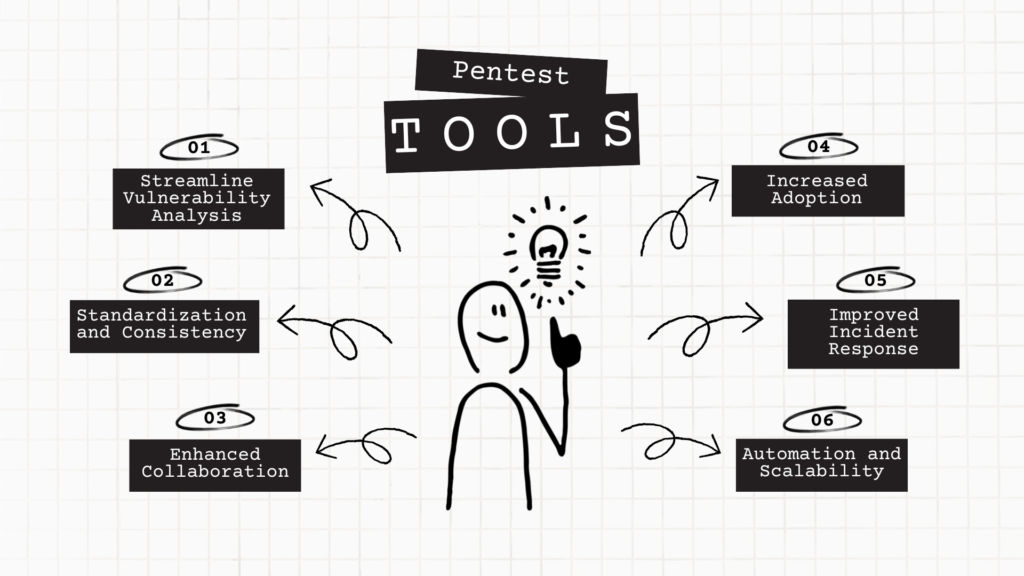
These early pentest frameworks and tools transformed the cybersecurity landscape in several significant ways:
- Streamlined Vulnerability Assessment: By centralizing various testing tools, modules, and techniques under a single platform, these early frameworks simplified the process of vulnerability assessment. Security professionals could now identify, exploit, and document vulnerabilities more efficiently, leading to faster remediation and better-secured systems.
- Standardization and Consistency: The advent of pentest frameworks helped establish standardized methodologies and best practices for penetration testing. This increased consistency across the industry, enabling organizations to more accurately measure the effectiveness of their security efforts and compare results across multiple tests.
- Enhanced Collaboration: Many of the early pentest frameworks, such as Metasploit, were open-source projects that encouraged community contributions. This fostered a collaborative environment where security professionals could share their expertise, develop new modules, and learn from one another, resulting in rapid innovation and adaptation to the ever-evolving threat landscape.
- Increased Adoption of Penetration Testing: As pentest frameworks made the testing process more accessible and efficient, more organizations began to recognize the value of regular penetration testing in assessing and strengthening their security posture. This increased adoption helped elevate the overall level of cybersecurity awareness and maturity across the industry.
- Improved Incident Response and Security Strategies: The insights gained from penetration tests conducted using these early frameworks helped organizations refine their incident response plans and develop more effective security strategies. By better understanding the potential attack vectors and vulnerabilities within their systems, organizations could proactively address security risks and reduce the likelihood of successful cyberattacks.
- Focus on Automation and Scalability: Early pentest frameworks highlighted the benefits of automating various aspects of the testing process, such as vulnerability scanning and exploit execution. This emphasis on automation paved the way for the development of more advanced frameworks that could scale to meet the needs of increasingly complex and interconnected systems and networks.
Advancements in Pentest Framework Capabilities
Enhanced Automation and Efficiency
The role of scripting languages in improving pentest frameworks

Scripting languages have played a significant role in the evolution and improvement of pentest frameworks, providing numerous benefits and enhancements in the penetration testing process. Some of the key contributions of scripting languages to pentest frameworks include:
- Automation: Scripting languages enable the automation of various aspects of the penetration testing process, from automating repetitive tasks to executing complex multi-step attacks. This automation not only increases the efficiency of the testing process but also helps to minimize human error and ensure a more consistent and thorough assessment of vulnerabilities.
- Extensibility and Customization: One of the key strengths of scripting languages is their flexibility, which allows security professionals to easily create custom scripts, modules, and plugins tailored to their specific testing requirements. This extensibility enables pentest frameworks to adapt to new threats, technologies, and environments, ensuring that they remain relevant and effective in the rapidly evolving cybersecurity landscape.
- Ease of Use: Scripting languages are generally more accessible and easier to learn than low-level programming languages, making it easier for security professionals to create custom tools and modules. This lowers the barrier to entry for newcomers to the field of cybersecurity and encourages a wider range of professionals to contribute to the development and improvement of pentest frameworks.
- Cross-Platform Compatibility: Many scripting languages are platform-agnostic, meaning they can run on various operating systems and environments with little to no modification. This cross-platform compatibility allows pentest frameworks to support a wide range of target systems, enhancing their versatility and applicability in diverse cybersecurity contexts.
- Rapid Development and Iteration: Scripting languages facilitate rapid development and testing of new tools, techniques, and exploits. This agility enables security professionals to quickly respond to emerging threats and vulnerabilities, ensuring that their pentest frameworks remain up-to-date and effective against the latest attack vectors.
- Integration and Interoperability: Scripting languages can act as a bridge between different tools and systems, enabling seamless integration and interoperability within pentest frameworks. This allows security professionals to combine the strengths of various tools, creating a more comprehensive and efficient testing environment.
Benefits of automation in vulnerability assessment
Automation has become an essential component of modern vulnerability assessment, offering numerous benefits that enhance the efficiency, accuracy, and effectiveness of the process. Some of the key benefits of automation in vulnerability assessment include:
- Time Savings: Automated vulnerability assessment tools can quickly scan large networks, systems, and applications, significantly reducing the time it takes to identify vulnerabilities compared to manual methods. This allows organizations to assess their security posture more frequently and react more swiftly to potential threats.
- Consistency and Reliability: Automated tools follow a standardized process for identifying and assessing vulnerabilities, ensuring consistent results across multiple assessments. This eliminates the potential for human error and bias, leading to more accurate and reliable vulnerability assessments.
- Scalability: Automation allows vulnerability assessments to be easily scaled up to cover large and complex networks and systems. As organizations grow and their IT environments become more complex, automated tools can be easily adapted to accommodate these changes without a significant increase in time or resources.
- Comprehensive Coverage: Automated vulnerability assessment tools can thoroughly scan and analyze every aspect of a system or network, providing a more comprehensive assessment than manual methods. This ensures that all potential vulnerabilities are identified and addressed, reducing the risk of a successful cyberattack.
- Continuous Monitoring: Automation enables continuous monitoring and real-time vulnerability detection, allowing organizations to identify and remediate vulnerabilities as soon as they arise. This proactive approach to vulnerability management helps to minimize the window of opportunity for attackers to exploit vulnerabilities.
- Prioritization of Vulnerabilities: Automated vulnerability assessment tools can help organizations prioritize vulnerabilities based on their severity, exploitability, and potential impact. This enables organizations to focus their remediation efforts on the most critical vulnerabilities, ensuring that resources are allocated effectively to minimize risk.
- Improved Reporting and Documentation: Automation can generate detailed reports and documentation about identified vulnerabilities, including information about their potential impact and recommended remediation steps. This helps organizations maintain a clear record of their security posture and track their progress in addressing vulnerabilities over time.
- Cost Savings: By streamlining the vulnerability assessment process and reducing the need for manual intervention, automation can lead to significant cost savings for organizations. This allows them to allocate resources more effectively and invest in other aspects of their cybersecurity strategy.
Integration of Advanced Vulnerability Scanning Techniques

The incorporation of fuzzing, static and dynamic analysis
To achieve a comprehensive understanding of an organization’s security posture, modern vulnerability assessment tools incorporate a variety of advanced scanning techniques, including fuzzing, static analysis, and dynamic analysis. Each of these methods offers unique benefits and insights, ensuring a more thorough and effective assessment of vulnerabilities.
- Fuzzing: Fuzz testing, or fuzzing, is a technique used to identify vulnerabilities and potential exploits in software applications by inputting malformed or unexpected data. Fuzzing can uncover memory leaks, buffer overflows, and other security flaws that could be exploited by malicious actors. By incorporating fuzzing into vulnerability assessment tools, organizations can proactively identify and address potential weak points in their software applications before they can be exploited.
- Static Analysis: Static analysis involves examining source code, binaries, or other software artifacts without actually executing the program. This technique helps identify potential security issues, such as insecure coding practices, logic errors, or misconfigurations, that could lead to vulnerabilities. By incorporating static analysis into vulnerability assessment processes, organizations can detect and remediate issues early in the software development lifecycle, reducing the risk of vulnerabilities being introduced into production systems.
- Dynamic Analysis: Dynamic analysis, also known as runtime analysis, involves analyzing software applications while they are executing in a controlled environment. This technique can identify vulnerabilities that may not be apparent during static analysis, such as issues related to input validation, access control, or data leakage. Dynamic analysis provides a more accurate and realistic assessment of how an application behaves under real-world conditions, enabling organizations to better understand and address potential security risks.
Advancements in web application security testing
Modular and customizable pentest frameworks
The rise of modular and customizable pentest frameworks has played a crucial role in the evolution of the cybersecurity landscape. As organizations face an increasingly diverse range of threats and operate in more complex IT environments, the need for pentest frameworks that can adapt to these unique requirements has become paramount. Modular and customizable pentest frameworks offer several key benefits that address these challenges:

- Adaptability: Modular frameworks are designed to accommodate a wide variety of testing scenarios and environments. By allowing security professionals to pick and choose the specific components, tools, and modules relevant to their testing objectives, these frameworks can be tailored to meet the unique needs of each organization, ensuring that vulnerability assessments remain relevant and effective.
- Scalability: As organizations grow and their IT environments become more complex, modular and customizable pentest frameworks can be easily expanded to accommodate new technologies, systems, and networks. This scalability ensures that the framework remains effective in the face of changing infrastructure and security requirements.
- Community–Driven Development: Customizable frameworks often leverage open-source technologies and community-driven development, which fosters collaboration and innovation within the cybersecurity community. This approach enables security professionals to share their expertise, develop new tools and techniques, and contribute to the ongoing improvement of the framework, ensuring that it remains current and responsive to emerging threats.
- Seamless Integration: Modular and customizable frameworks facilitate the integration of a wide range of third-party tools, technologies, and data sources. This allows organizations to leverage the strengths of multiple solutions and create a more comprehensive and efficient testing environment.
- Cost–Effectiveness: By allowing organizations to select and implement only the modules and components that are relevant to their specific needs, modular and customizable frameworks can help reduce costs and ensure that resources are allocated effectively.
Open-source contributions and the growth of the security community

The customization and extensibility of modern pentest frameworks and vulnerability assessment tools have played a vital role in their evolution and effectiveness. One particularly influential aspect of this customization and extensibility is the role of open-source contributions in fostering the growth of the security community.
Open source contributions have helped the community in many ways including:
- Collaborative Development: Open-source projects, such as Metasploit and OWASP ZAP, have created opportunities for security professionals and developers to collaborate on creating, improving, and expanding the capabilities of these tools. This collaborative development environment accelerates innovation and adaptation to the ever-evolving threat landscape, ensuring that pentest frameworks and vulnerability assessment tools remain up-to-date and effective.
- Shared Expertise: The open-source nature of many pentest frameworks encourages the sharing of knowledge and expertise among security professionals. This fosters a culture of continuous learning and improvement, where individuals can learn from the experience and insights of others, contributing to the overall growth and maturation of the security community.
- Custom Modules and Plugins: Open-source projects allow security professionals to create and share custom modules, plugins, and extensions for pentest frameworks and vulnerability assessment tools. These customizations enable the tools to be tailored to specific testing requirements or environments, increasing their versatility and effectiveness in addressing unique security challenges.
- Lower Barrier to Entry: Open-source tools and resources lower the barrier to entry for individuals looking to enter the field of cybersecurity. By offering free access to powerful tools and a wealth of shared knowledge, open-source projects empower aspiring security professionals to learn, experiment and contribute to the growth of the security community.
- Wider Adoption: The availability of open-source pentest frameworks and vulnerability assessment tools has led to their widespread adoption across the cybersecurity industry. This has not only contributed to the growth of the security community but also helped to raise awareness and promote best practices in vulnerability management.
Modern Pentest Frameworks and their Impact
Comprehensive Security Testing Platforms
In recent years, the cybersecurity landscape has seen the emergence of comprehensive security testing platforms that go beyond traditional pentest frameworks. These platforms offer a holistic approach to security assessment, integrating various tools and techniques for a complete evaluation of an organization’s security posture. They often incorporate vulnerability scanning, penetration testing, compliance monitoring, and other security-related functionalities into a unified platform.
Here, we will discuss some key features and examples of comprehensive security testing platforms:
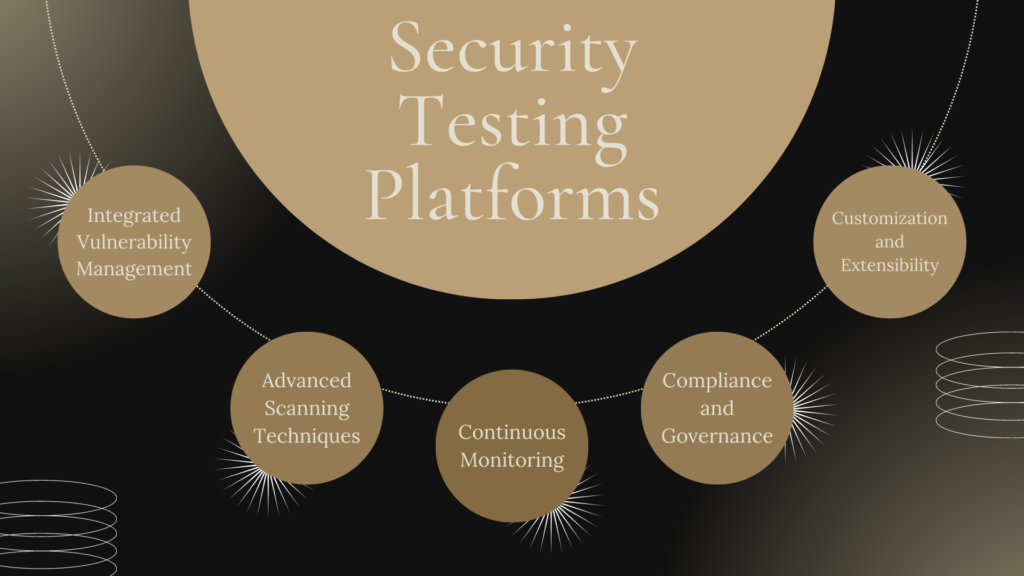
- Integrated Vulnerability Management: Comprehensive security testing platforms typically include integrated vulnerability management solutions that automate the process of discovering, prioritizing, and tracking vulnerabilities across an organization’s systems and networks. This allows organizations to maintain a clear understanding of their security risks and allocate resources effectively to remediate vulnerabilities.
- Advanced Scanning Techniques: These platforms often incorporate advanced scanning techniques, such as static and dynamic analysis, fuzz testing, and behavioral analysis, to provide a more in-depth and accurate assessment of potential vulnerabilities. By leveraging a combination of these techniques, comprehensive security testing platforms can identify a wider range of security flaws, ensuring a more thorough evaluation of an organization’s security posture.
- Continuous Monitoring: Comprehensive security testing platforms emphasize the importance of continuous monitoring and real-time vulnerability detection. By providing ongoing visibility into an organization’s security environment, these platforms enable organizations to proactively address security risks and minimize the potential for successful cyberattacks.
- Compliance and Governance: Many comprehensive security testing platforms offer built-in compliance and governance features, allowing organizations to monitor and enforce adherence to industry-specific regulations and security best practices. This helps organizations maintain compliance with relevant standards and minimize the risk of penalties and reputational damage.
- Customization and Extensibility: Similar to all-in-one pentest frameworks, comprehensive security testing platforms often support customization and extensibility through custom scripts, modules, and plugins. This allows organizations to tailor the platform to their unique security requirements and adapt to new threats and technologies as they emerge.
The Shift Towards Cloud-Based Pentest Frameworks
The rapid growth and adoption of cloud computing in recent years have led to a significant shift towards cloud-based pentest frameworks. This transition has been driven by the numerous benefits and advantages that cloud-based solutions offer over traditional on-premises frameworks. Here, we will explore some key factors contributing to this shift and the advantages of using cloud-based pentest frameworks:
- Scalability: Cloud-based pentest frameworks offer unparalleled scalability, allowing organizations to easily adjust the resources and capabilities of their testing environment based on their requirements. This ensures that security professionals can efficiently assess large and complex networks, applications, and infrastructure without being constrained by the limitations of on-premises hardware.
- Flexibility: Cloud-based frameworks provide the flexibility to access and deploy testing tools from anywhere, at any time. This enables security professionals to perform security assessments and respond to incidents more quickly and effectively, regardless of their physical location.
- Cost Savings: By leveraging cloud infrastructure, organizations can reduce the costs associated with maintaining and managing on-premises hardware and software. Cloud-based pentest frameworks typically offer a pay-as-you-go pricing model, which allows organizations to only pay for the resources they consume during testing, leading to significant cost savings.
- Ease of Deployment and Maintenance: Cloud-based pentest frameworks often come with pre-configured environments and tools, simplifying the deployment process and reducing the time needed to set up a testing environment. Additionally, maintenance and updates are typically managed by the cloud service provider, ensuring that the latest tools and techniques are always available without the need for manual updates or installations.
- Integration with Other Cloud Services: Cloud-based pentest frameworks can easily integrate with other cloud services and tools, such as continuous integration and delivery pipelines, security information and event management (SIEM) solutions, and threat intelligence platforms. This seamless integration enables organizations to create a more cohesive and efficient security testing environment.
- Data Security and Privacy: Leading cloud service providers adhere to strict security standards and best practices, ensuring that data and information stored in the cloud are protected from unauthorized access and potential breaches. By using cloud-based pentest frameworks, organizations can take advantage of these robust security measures while performing their security assessments.
Examples of Comprehensive Security Testing Platforms:
- Tenable.io: Tenable.io is a cloud-based vulnerability management platform that offers a wide range of security assessment features, including vulnerability scanning, compliance monitoring, and web application security testing.
- Rapid7 InsightVM: InsightVM is a vulnerability management and risk assessment platform that integrates with the popular Metasploit Framework. It provides a comprehensive view of an organization’s security posture, with features such as real-time vulnerability detection, risk scoring, and remediation prioritization.
- Qualys Cloud Platform: The Qualys Cloud Platform is a comprehensive security and compliance solution that offers vulnerability management, web application scanning, and policy compliance monitoring. It also includes features for assessing container security and cloud infrastructure.
Future Trends and Challenges
As the cybersecurity landscape continues to evolve, machine learning (ML) and artificial intelligence (AI) are poised to play an increasingly significant role in the development and enhancement of pentest frameworks. The integration of these advanced technologies has the potential to revolutionize vulnerability assessment and penetration testing processes, offering new opportunities and challenges for security professionals. In this section, we will explore the impact of machine learning and artificial intelligence on pentest frameworks and discuss the future trends and challenges associated with their integration.

- Enhanced Vulnerability Detection: ML and AI algorithms can be used to analyze vast amounts of data and identify patterns that indicate potential vulnerabilities, security flaws, or suspicious activities. By incorporating these algorithms into pentest frameworks, organizations can improve the accuracy and efficiency of vulnerability detection, uncovering security risks that might otherwise go undetected by traditional methods.
- Adaptive Testing: ML and AI can enable pentest frameworks to adapt and respond to the unique characteristics of each target system, network, or application. This adaptive testing approach can help security professionals tailor their testing strategies and techniques based on the specific security posture and risk profile of the target environment, resulting in more effective and targeted assessments.
- Automated Exploit Generation: AI-driven techniques, such as genetic algorithms and reinforcement learning, can be used to automatically generate and test potential exploits based on the identified vulnerabilities. This can help organizations quickly develop and deploy patches or mitigations, reducing the window of opportunity for attackers to exploit vulnerabilities.
- Advanced Threat Modeling: Machine learning and artificial intelligence can facilitate advanced threat modeling by simulating complex attack scenarios and analyzing the potential impact of various threats on an organization’s security posture. This can help security professionals better understand the risks associated with different vulnerabilities and prioritize their remediation efforts accordingly.
Challenges

Complexity and Resource Requirements: The integration of ML and AI into pentest frameworks introduces new levels of complexity and requires significant computational resources to process and analyze data. Organizations must invest in the necessary infrastructure and expertise to support these advanced technologies effectively.
Trustworthiness and Explainability: As ML and AI algorithms become more sophisticated and autonomous, concerns about their trustworthiness and explainability may arise. Security professionals must ensure that AI-driven tools and techniques are transparent and well-understood, enabling them to make informed decisions about their deployment and use.
Ethical Considerations: The integration of ML and AI into pentest frameworks raises ethical questions about the potential misuse of these technologies by malicious actors. Organizations must consider the ethical implications of using AI-driven tools and techniques and implement appropriate safeguards to prevent their abuse.
Machine learning and artificial intelligence have the potential to transform pentest frameworks and reshape the future of vulnerability assessment and penetration testing. By embracing these advanced technologies, organizations can enhance their ability to detect and address vulnerabilities more effectively and efficiently.
However, the integration of ML and AI also presents new challenges, requiring organizations to carefully consider the implications of their use and ensure that they are deployed responsibly and ethically.
Conclusion
In summary, the continuous evolution of pentest frameworks has had a profound impact on the cybersecurity industry, driving innovation and improving the effectiveness of vulnerability assessment and penetration testing processes. The emergence of these frameworks has transformed the way security professionals identify, analyze, and address security risks, enabling organizations to better protect their networks, systems, and applications from cyber threats.
As we look to the future, the integration of advanced technologies, such as machine learning and artificial intelligence, promises to further revolutionize pentest frameworks and redefine the landscape of cybersecurity. By staying abreast of these developments and embracing the potential of these cutting-edge tools and techniques, organizations can ensure a robust and resilient defense against the ever-evolving landscape of cyber threats and maintain a secure environment in an increasingly interconnected world.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.






