Tenable, the Exposure Management company, recently unveiled a comprehensive study that unveils the obstacles faced by cybersecurity and IT leaders as they strive to safeguard their organizations’ growing attack surfaces.
This report, titled “Old Habits Die Hard: How People, Process, and Technology Challenges Are Impacting Cybersecurity Teams,” offers valuable insights.
Released during Cybersecurity Awareness Month, it brings to light a concerning statistic: over the past two years, the typical organization’s cybersecurity program was only able to proactively defend against 57% of the cyberattacks it encountered. This leaves a substantial 43% of attacks that successfully breach their defenses, necessitating post-attack remediation efforts.
This study, conducted in 2023 by Forrester Consulting on behalf of Tenable, draws from a survey of 825 global cybersecurity and IT leaders. It sheds light on the people, processes, and technology challenges obstructing modern cybersecurity and IT teams from implementing effective risk reduction measures.
The Predominance of Reactive Measures
A significant finding from the study is that nearly 58% of respondents primarily focus on responding to successful attacks rather than working to prevent them proactively.
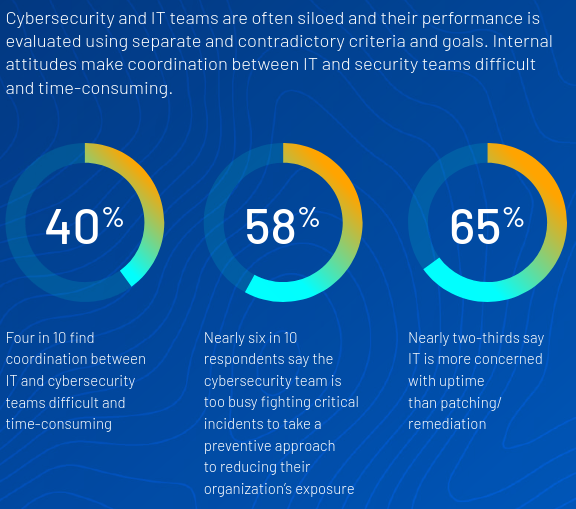
This reactive approach is primarily attributed to the difficulties organizations face in reducing potential risks before attacks occur. Cybersecurity professionals often find it challenging to gain a comprehensive view of their attack surface, including identifying unknown assets, cloud resources, code vulnerabilities, and user entitlement systems. The increasing complexity of infrastructure, with its reliance on multiple cloud systems, numerous identity and privilege management tools, and a variety of web-facing assets, introduces numerous opportunities for misconfigurations and overlooked assets.
Notably, respondents express heightened concerns regarding the risks associated with cloud infrastructure. A significant 53% of them view cloud infrastructure as the most substantial source of exposure risk within their organizations. Public cloud usage (30%), multi-cloud and/or hybrid cloud (23%), private cloud infrastructure (12%), and cloud container management tools (9%) rank in descending order as the sources of perceived risks.
Key Findings from the Study
Several additional findings emerge from this comprehensive study:
- While 75% of respondents consider user identity and access privileges when prioritizing vulnerabilities for remediation, 50% admit that their organizations lack an effective method for integrating this data into their preventive cybersecurity and exposure management practices.
- Data hygiene issues hinder 57% of respondents from extracting quality data from user privilege and access management systems, as well as from vulnerability management systems.
- On average, organizations spend 15 hours each month preparing reports for business leaders on the state of their security infrastructure.
- Concerning meetings about business-critical systems, 53% of organizations hold these meetings monthly, while 18% do so only once a year, and 2% never convene such meetings.
Tools and Technologies Used As Part of the Cybersecurity Strategy
According to the study, the most used tools used by organizations as part of their cybersecurity strategy are:
- Password encryption: 82%
- Identity and user privilege management: 77%
- Antivirus/Anti-Malware: 73%
- Firewalls: 68%
- Cloud Security: 64%
A Timely Call to Action
This data is of utmost significance for publicly traded companies, particularly given the recent introduction of SEC rules on cybersecurity risk management, strategy, governance, and incident disclosure.
These rules, effective from December of this year, mandate the disclosure of material cybersecurity incidents by public companies. They also require these organizations to outline their processes for assessing, identifying, and managing material risks stemming from cybersecurity threats. Additionally, the rules highlight the oversight processes of boards of directors and executive management concerning cybersecurity risk management. For companies lacking these best practices and processes, preventive security measures will become a requirement for continued operations.
Robert Huber, Chief Security Officer and Head of Research at Tenable, aptly states, “Preventive security is no longer an optional approach to risk management, but a prerequisite.” With the expanding attack surface and exposure points brought about by trends like cloud migration and AI, it’s clear that the current firefighting approach is a recipe for failure.
Many organizations acknowledge the importance of proactively understanding and mitigating risks, but they often face challenges beyond their control. The hope is that this research will foster collaborative discussions among stakeholders to simplify practices, prioritize risk remediation, and navigate the complex landscape of modern cybersecurity successfully.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.
