Introduction
Rorschach is a newly discovered ransomware strain that has caught the attention of the cybersecurity industry. It was discovered by the Cybersecurity and Infrastructure Security Agency (CISA) in the United States while responding to a ransomware case.
The ransomware stood out due to two rare facts, the threat actor did not use an alias, and it has no affiliation to any known ransomware groups.
This article aims to provide a detailed analysis of Rorschach’s unique features.
Execution Flow
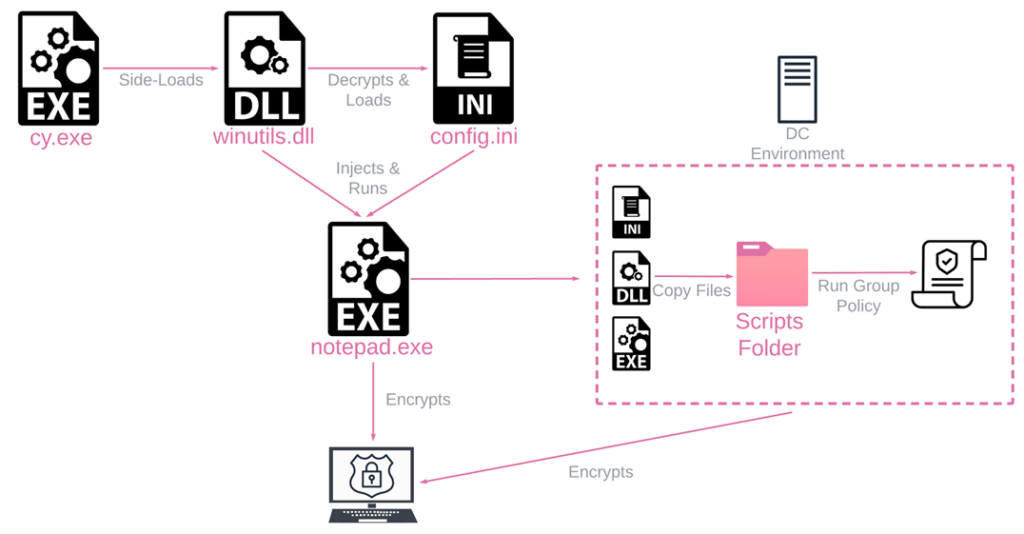
Rorschach’s execution flow comprises three files:
- cy.exe,
- winutils.dll,
- and config.ini
When cy.exe is executed, the loader/injector winutils.dll is loaded into memory and runs in the context of cy.exe.
Subsequently, the main Rorschach payload config.ini is loaded into memory, decrypted, and injected into notepad.exe, where the ransomware logic begins.
Security Solution Evasion
Rorschach uses uncommon methods to evade security solutions. It runs processes in SUSPEND mode, providing falsified arguments to harden analysis and remediation efforts. The ransomware uses this technique to run operations like:
- stopping services,
- deleting shadow volumes and backups,
- clearing event logs,
- and disabling the Windows firewall
Self-Propagation
Rorschach can spread automatically when executed on a Domain Controller (DC) by creating a Group Policy that copies itself into the %Public% folder of all workstations in the domain.
It also creates a Group Policy to kill a predefined list of processes by invoking taskkill.exe and registers a scheduled task that runs Rorschach’s main executable with the relevant arguments.
Ransomware Analysis
The Rorschach binary is carefully protected and requires a lot of work to access. The initial loader/injector winutils.dll is protected with UPX-style packing, which requires manual unpacking. After unpacking, the sample loads and decrypts config.ini, which contains the ransomware logic.
Rorschach uses the “syscall” instruction to make direct system calls, which is uncommon in ransomware. It also contains built-in options hidden and obfuscated from reverse-engineering.
Encryption Process
Rorschach employs a hybrid-cryptography scheme that blends the curve25519 and eSTREAM cipher hc-128 algorithms for encryption purposes.
This process only encrypts a specific portion of the original file content, and the WinAPI CryptGenRandom generates cryptographically random bytes used as a per-victim private key. The shared secret is calculated through curve25519, using both the generated private key and a hardcoded public key.
The ransomware logic implements thread scheduling via I/O completion ports and compiler optimization for speed. Rorschach is one of the fastest ransomware strains, encrypting 220,000 files in 4 minutes, 30 seconds.
Technical Similarity to Other Ransomware
Rorschach appears to have borrowed some routines from Babuk and LockBit ransomware strains. The hybrid-cryptography scheme of Rorschach bears a resemblance to Babuk’s, and the code used to stop services through the service control manager appears to have been directly copied from Babuk’s source code.
Rorschach’s list of languages used to halt the malware is the same list used in LockBit v2.0, and it also took some inspiration from LockBit in the I/O Completion Ports method of thread scheduling.
Ransom Notes
The Rorschach variant analyzed leaves a ransom note structured like Yanlowang’s ransomware group. However, a similar attack reported earlier this year by AhnLab triggered an almost identical execution flow but left a ransom note similar to those issued by DarkSide.
Conclusion
In conclusion, the Rorschach ransomware is a newly discovered strain that exhibits unique and sophisticated features. Unlike other ransomware cases, the threat actor did not hide behind any alias and appears to have no affiliation to any of the known ransomware groups. It has been observed to use signed components of commercial security products to evade detection and run processes in a way that is difficult to analyze and remediate. It also has the ability to propagate itself within a Windows Domain Controller, making it a significant threat to large organizations.
The ransomware’s encryption process is highly effective and fast, using a hybrid-cryptography scheme that combines curve25519 and eSTREAM cipher hc-128 algorithms. The code is also protected and obfuscated in an unusual way for ransomware, making it difficult to analyze and compare to other strains. Nonetheless, Rorschach appears to have taken inspiration from some of the most infamous ransomware families, incorporating various time-honored methods with some novel ideas of its own.
Overall, the discovery of Rorschach ransomware highlights the need for continued vigilance and improved cybersecurity measures to protect against evolving threats. Organizations should ensure they have robust security solutions in place, including regular backups, to minimize the impact of a potential attack.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.
