The North Korea-linked Lazarus APT group has been observed employing a novel weapon in their arsenal – the KandyKorn macOS malware. This insidious tool has been used in a series of targeted attacks against blockchain engineers, revealing a growing concern for the security of cryptocurrency professionals. Elastic Security Labs has been diligently tracking these developments, shedding light on the sinister activities of this threat actor.
KandyKorn Malware: A Closer Look
The KandyKorn malware, described as an advanced implant, boasts a wide range of capabilities designed to monitor, interact with, and, perhaps most significantly, evade detection.
It deploys reflective loading, a form of direct-memory execution that can effectively bypass detection mechanisms. Elastic Security Labs, which undertook the analysis of this threat, has highlighted the potency of this malicious software.
The Attack Strategy: Impersonation and Deception
To infiltrate their targets, the threat actors within the Lazarus group took on the guise of blockchain community members in a public Discord channel frequented by individuals in this field.
Their goal was simple but effective: lure victims into downloading and extracting a ZIP archive labeled “Cross-Platform Bridges.zip.”
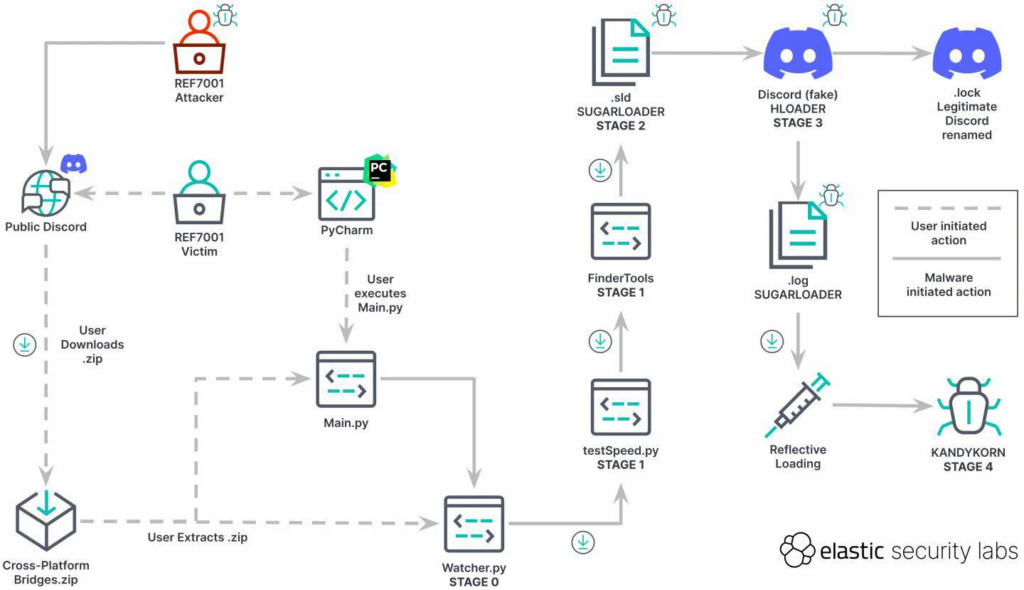
Inside this seemingly innocuous archive lurked malicious Python code, concealed behind the mask of an arbitrage bot. Arbitrage bots are legitimate tools used to capitalize on cryptocurrency rate discrepancies between platforms.
The Malicious Chain of Events
The attack unfolded in stages, with the ultimate aim of infecting the target system with the KandyKorn macOS malware. The sequence of malicious code employed in the operation consisted of the following stages:
- Stage 0 (Initial Compromise) – Watcher.py
- Stage 1 (Dropper) – testSpeed.py and FinderTools
- Stage 2 (Payload) – .sld and .log – SUGARLOADER
- Stage 3 (Loader)- Discord (fake) – HLOADER
- Stage 4 (Payload) – KANDYKORN
Upon extracting the archive, victims discovered a Main.py script alongside a folder named “order_book_recorder,” containing 13 Python scripts. The SUGARLOADER was responsible for connecting to the command and control (C2) server, downloading the KandyKorn malware, and executing it directly in memory.
A Trail of Digital Bread Crumbs: Attribution and Capabilities
Elastic researchers, in their pursuit of unraveling this campaign, managed to trace it back to April 2023, primarily through the identification of the RC4 key used to encrypt the SUGARLOADER and KandyKorn C2 communication.
This malware exhibits a multitude of capabilities, including information harvesting, directory listing, process execution, file downloads and uploads, archiving directories, process termination, terminal command execution, shell spawning, configuration retrieval from the server, sleeping, and clean exit.
A Sinister Motive: Cryptocurrency as the Target
The North Korea-linked threat actors maintain a relentless focus on targeting organizations within the cryptocurrency industry. Their objective is twofold: to evade international sanctions and secure funding for their military operations.
This pattern is well-documented and remains consistent, with the Lazarus Group at the forefront of such campaigns. In their intrusion, they targeted blockchain engineers participating in a public chat server, crafting lures that speak directly to their skills and interests, all while hinting at the promise of financial gain. The level of interactivity required from the victims was designed to mirror what would be expected in a legitimate context.
Ongoing Threat: A Warning from Elastic Security
Elastic Security, in its continuous monitoring of the situation, sounds a note of caution. The campaign remains active, and the threat actors are undoubtedly refining their tactics, techniques, and procedures. This serves as a stark reminder of the ever-present danger faced by cryptocurrency professionals and the need for robust cybersecurity measures.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.
