The Collaboration between Microsoft’s DCU, Fortra, and Health-ISAC
A recent joint operation between Microsoft’s Digital Crimes Unit (DCU), Fortra, and the Health-ISAC has resulted in a major legal crackdown against servers hosting illicit versions of Cobalt Strike.
Cobalt Strike is a tool that is widely used by threat actors for hacking purposes, making it a significant target for such operations.
Fortra, a company dedicated to protecting the legitimate use of its security tools, has taken this vital action to safeguard such use. Microsoft has also been actively involved in ensuring that its services and products are used lawfully.
Disruption Plan
To effectively disrupt the usage of pirated legacy copies of Cobalt Strike, a court order has been issued by the U.S. District Court for the Eastern District of New York on March 31, 2023. The plan involves enlisting the assistance of relevant CERTs and ISPs to make all malicious infrastructure non-functional.
This move will substantially restrict the ability of criminals to monetize and employ illegal versions of the tool for cyber attacks, forcing them to seek new alternatives.
Ransomware Gangs and Hackers Exploiting Cobalt Strike
Cobalt Strike was originally introduced as a legitimate commercial penetration testing tool by Fortra in 2012.
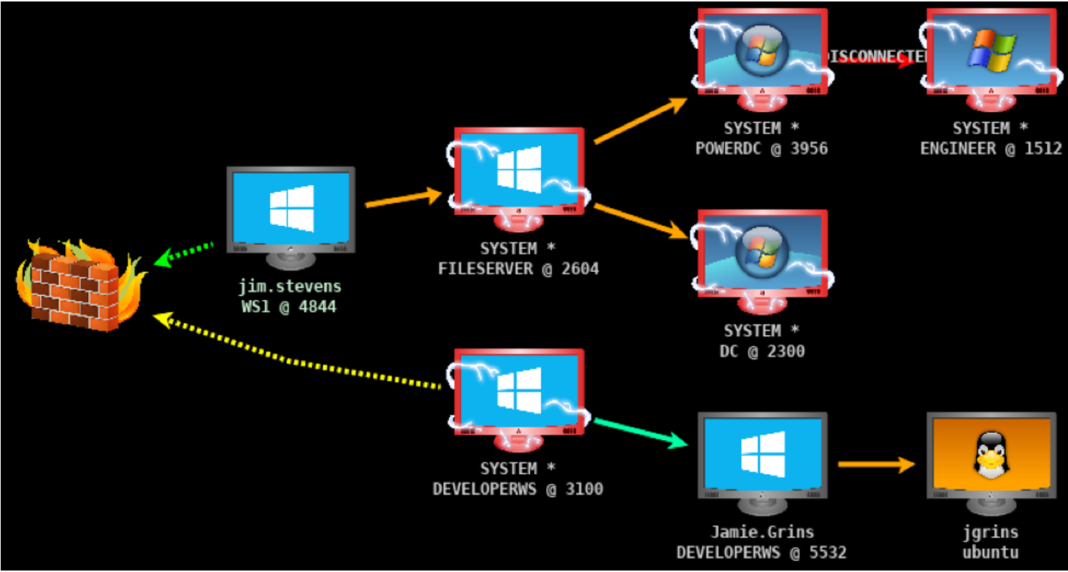
Despite strict licensing policies, the tool’s cracked copies have been acquired and distributed by threat actors worldwide. These actors use the tool in their post-exploitation operations, enabling them with persistent remote access to compromised devices to harvest sensitive data or drop additional malicious payloads.
Global Malicious Infrastructure for Cobalt Strike
Countries such as China, the United States, and Russia have been identified by Microsoft as hosting malicious infrastructure for Cobalt Strike. The identities of those responsible for these criminal activities remain unknown.
Hackers and threat actors affiliated with state-supported organizations and hacker groups have been observed using cracked versions of Cobalt Strike for cyber attacks at the behest of foreign governments, such as Russia, China, Vietnam, and Iran.
Collaboration with Other Security Bodies
Microsoft, Fortra, and Health-ISAC are actively working to improve the security of their ecosystem and have affirmed that they will collaborate with other security bodies such as the FBI Cyber Division, National Cyber Investigative Joint Task Force (NCIJTF), and Europol’s European Cybercrime Centre (EC3).
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.