a new and cunning malvertising campaign has surfaced, employing Google Ads to ensnare users searching for popular software. Malwarebytes, the cybersecurity stalwart that uncovered this activity, describes it as “unique in its way to fingerprint users and distribute time-sensitive payloads.”
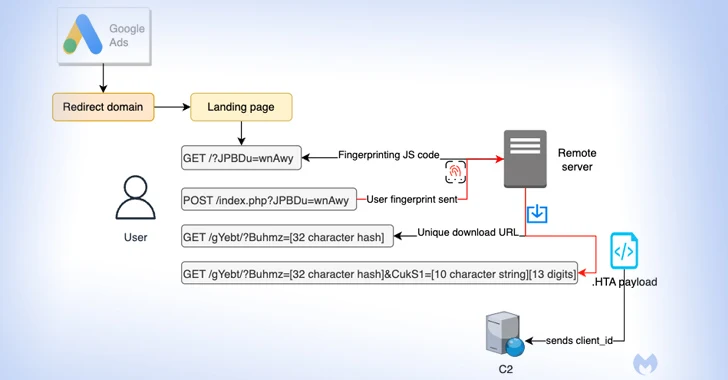
The attack targets unsuspecting users seeking software like Notepad++ and PDF converters by presenting fake advertisements in Google search results. Clicking on these ads triggers a series of maneuvers designed to filter out bots and unwanted IP addresses, ultimately leading to a deceptive website.
If the user piques the interest of the threat actor, they are redirected to a replica site promoting the software, all while surreptitiously fingerprinting the user’s system to identify if the request originates from a virtual machine.
The Art of Deception
Those who fail the system check, are redirected to the legitimate Notepad++ website, whereas a potential target receives a unique ID for tracking purposes and to ensure each download is both unique and time-sensitive. This method grants malicious actors a reliable malware delivery chain, allowing them to focus on refining their decoy pages and crafting custom malware payloads.
A Sinister Synergy
Interestingly, this revelation coincides with a similar campaign targeting users searching for the KeePass password manager. Malicious ads in this campaign direct victims to a domain utilizing Punycode, a special encoding technique that converts Unicode characters to ASCII. This intricate process ensures that only genuine victims reach the final destination by filtering out sandboxes and bots.
The Unveiling of the Malware
Users who land on the deceptive site are lured into downloading a malicious installer, setting in motion the execution of FakeBat, also known as EugenLoader. This loader is specifically engineered to download further malicious code, thereby compromising the user’s system.
Conclusion
The combination of Punycode and rogue Google Ads is a testament to the increasing sophistication of malvertising via search engines. By using Punycode to create domain names similar to legitimate sites, malicious actors execute a homograph attack, successfully enticing unsuspecting users into installing malware.