Oracle and KPMG published the “Cloud Threat and Security Report 2020” which identifies the key risks and challenges that organizations are facing as they implement and maintain cloud solutions. Securing an organization’s data and maintaining compliance require a security-first approach to culture and infrastructure, with a clear understanding of the shared responsibilities required for cloud security.
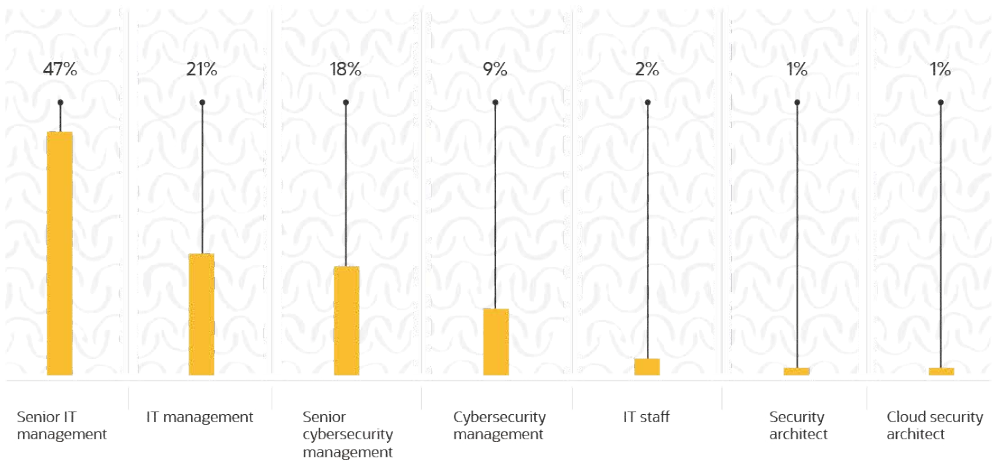
RESPONDERS ROLES IN THE ORGANIZATION
PUBLIC CLOUDS ARE VIEWED MORE SECURE THAN ON-PREMISE ENVIRONMENTS
Even in the face of well publicized public cloud data loss incidents, many consider public clouds as more secure and resilient environments. In fact 40% of the responders shared a sentiment that they view public clouds as much more secure than what they can deliver with theri on-prmises environemnt.
BUSINESS CRITICAL APPLICATIONS MOVING TO PUBLIC CLOUDS
Cloud Migration Outpaces Security Readiness
92% of admitted that their organization has a gap between current and planned cloud usage and the maturity of their cloud security program.
ORGANIZATIONS ARE NOT FOLLOWING THE RULE OF LEAST PRIVILEGE
The fundamental concept of restricting access rights for users and accounts to the minimum needed to conduct a task and do one’s job is paramount in today’s hybrid, multi-cloud reality.
Over-privileged accounts (37%). Not all accounts need root or admin privileges. The more accounts that have escalated rights, the greater the risk for business and the greater the reward for attackers.
Exposed web servers and other types of server workloads (35%). Server workloads that are externally facing are subject to port scanning if they are not routed through a bastion host or if their security groups are not properly configured to prevent unauthorized protocols and traffic over open ports. A bastion host is a minimally configured, hardened, single purpose proxy that provides access to an internal network from the internet.
Object store-resident data not appropriately secured via access control lists (ACLs) (34%). Confusion related to the ACLs that control who can access what types of data stored in object stores has led to unauthorized access and data loss.
The lack of multi-factor authentication (MFA) (33%). Cloud consoles are the point of control for cloud accounts, and, as such, access should be protected with an additional authentication challenge. We will revisit this important topic.
Disabled logging for capturing an audit trail of cloud activity (31%). The dynamic and temporal nature of IaaS platforms requires retaining an audit trail of activity for regulatory compliance and investigative purposes.
UNPROTECTED CLOUD SECRETS INCREASING BUSINESS VULNERABILITY
The placement of cloud secrets, sometimes in clear text, in unprotected locations is another byproduct of competing objectives. Dev teams are simply moving fast and not thinking about where they are placing secrets.
Best practices to secure cloud secrets include, again, the implementation of least privilege policies and storing secrets in a secure store such as a hardware storage module (HSM) or key vault.
LOCATIONS OF UNPROTECTED SECRETS
WHAT WAS DEPLOYED AFTER CLOUD MISCONFIGURATION WAS DETECTED
TURNING DevOps TO DevSecOps
Just as DevOps required a cultural shift that led to a different mindset, culture will be the starting point for integrating security into DevOps processes.
DevOps is being broadly adopted across the board, with only 6% saying their company has no plans to employ DevOps. With nearly one-third of respondents already employing DevOps, almost another quarter planning to do so in the next 12-24 months, and another one-third interested in doing so, it is evident that DevOps is quickly becoming mainstream as the standard approach for how software is built and applications are deployed.
To what extent does your organization plan to incorporate security processes and controls via its DevOps processes (i.e., DevSecOps)?
PRIMARY REASONS THE ORGANIZATION PLANS OR ALREADY EMPLOYS DEVSECOPS
Collaboration: 40% shared that DevSecOps fosters a high level of collaboration between their development, infrastructure management, application owners, and cybersecurity stakeholders, a pillar of DevOps culture.
Efficiency: 40% noted that DevSecOps allows them to gain greater operational
efficiency vis-à-vis automation, always a welcome benefit given resource-challenged cybersecurity teams.
DevSecOps also serves compliance considerations, with over one-third (36%) sharing that DevSecOps allows them to assure that their business meets and maintains compliance with applicable industry regulations.
PHISHING TARGETS AND TECHNIQUES ARE EXPANDING
Criminals are now stealing privileged credentials via targeted phishing to gain access to an organization’s critical cloud services as well as the data associated
with those services. A key takeaway of this year’s cloud threat report is privileged cloud credentials are the new keys to the kingdom. Unfortunately, an astounding
59% of research respondents shared that members of their organization with privileged cloud accounts have had those credentials compromised by a
spear phishing attack.
Have any members of your organization with privileged cloud accounts been compromised by a spear-phishing attack designed to steal their cloud credentials?
CYBERSECURITY ATTACKS WITHIN THE LAST 24 MONTHS
AI/ML Are Viewed as Applicable for a Range of Cybersecurity Use Cases
For which of the following cybersecurity use cases will your organization employ artificial intelligence within the next 24 months?
LESSONS LEARNED AND RECOMMENDATIONS
The alarming cloud security readiness gap exposed in this report reveals that today’s line-of-business-driven consumption of cloud services threatens to leave security considerations even further behind. The incessant cycle of phishing, malware, increasing cyber fraud, and a range of misconfigured cloud
services further stretch already challenged cybersecurity programs.
Be a catalyst to bring about cultural change within your organization so that the use of cloud services and applications is not at odds with cybersecurity objectives.
Become an expert on the cloud security shared responsibility model to eliminate any ambiguity on how you and your cloud services providers divide securing your company’s portfolio of cloud services.
Leverage DevSecOps automation as a means to implement repeatable cloud configuration management best practices to secure the entire lifecycle of cloud applications.
Get savvy on cyber business fraud to better secure what will be an expanded use of SaaS applications in all areas of your business.
