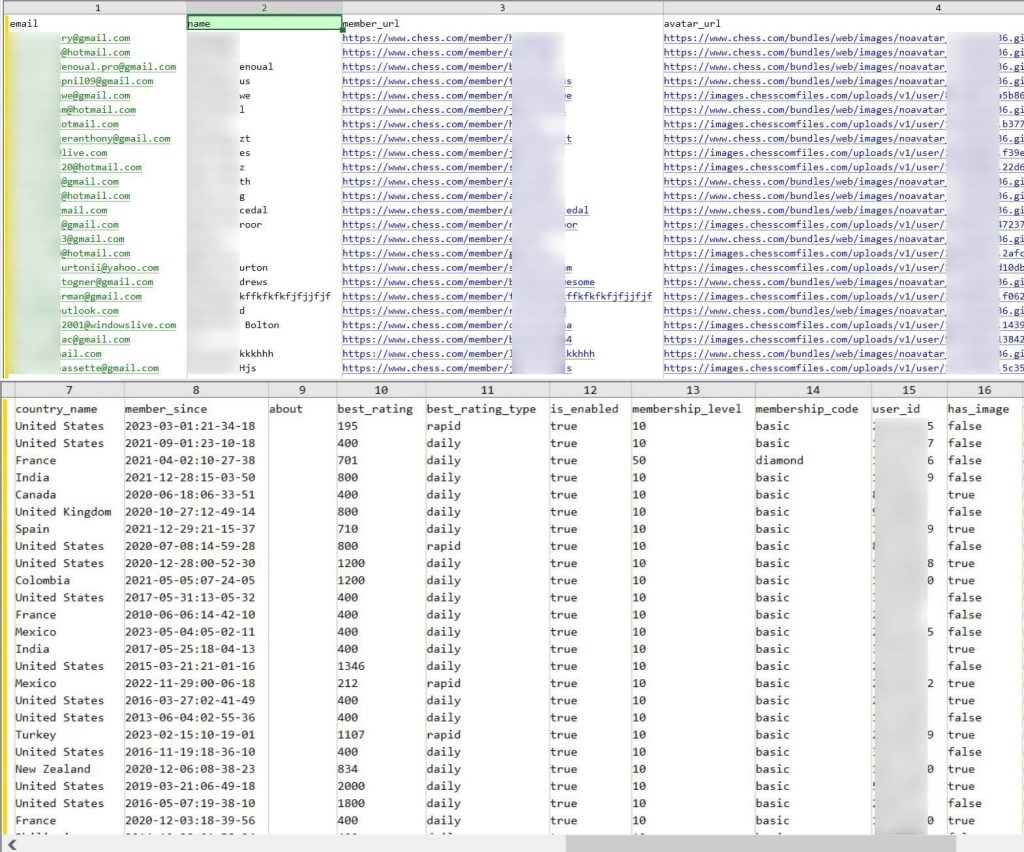
A threat actor known as ‘DrOne’ has claimed responsibility for leaking a scraped database from Chess.com, a popular online platform for chess enthusiasts, exposing the personal data of over 800,000 registered users.
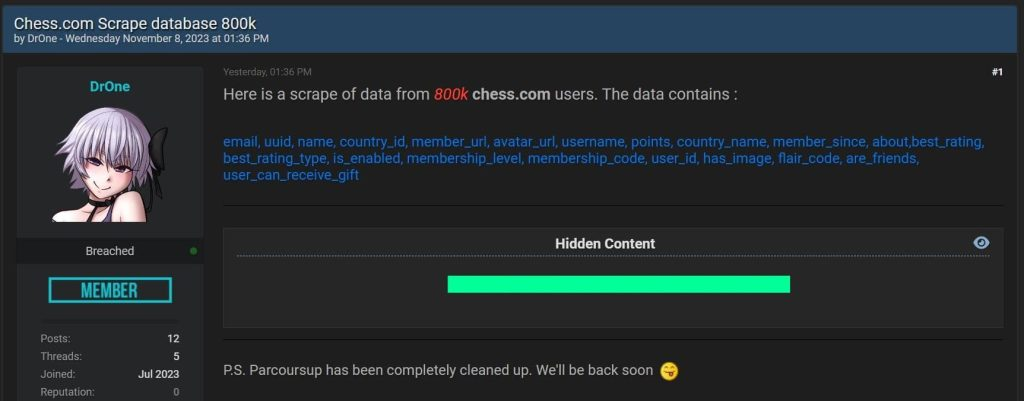
The leaked records, disclosed on Breach Forums, include full names, usernames, profile links, email addresses, originating countries, avatar URLs, Universally Unique Identifier (UUID), User IDs, and date of registration.
While the leaked data does not include passwords, it serves as valuable information for cybercriminals, enabling potential identity theft, phishing scams, social engineering attacks, or cross-referencing with previously leaked login credentials. The leak raises concerns about the security of Chess.com, especially as this is not the platform’s first encounter with cybersecurity issues.
In February 2021, ethical hacker Sam Curry discovered and reported a critical vulnerability in Chess.com that could potentially grant unauthorized access to any account on the platform, including administrator accounts. This recent breach emphasizes the need for affected users to change their passwords not only on Chess.com but also on other accounts where the same password is used.
Given the potential for phishing tactics exploiting the breach, users are urged to exercise caution and avoid clicking on suspicious links. Verifying URLs before clicking and staying vigilant against phishing attempts are crucial measures to enhance cybersecurity in the aftermath of this data leak.
Dimitris is an Information Technology and Cybersecurity professional with more than 20 years of experience in designing, building and maintaining efficient and secure IT infrastructures.
Among others, he is a certified: CISSP, CISA, CISM, ITIL, COBIT and PRINCE2, but his wide set of knowledge and technical management capabilities go beyond these certifications. He likes acquiring new skills on penetration testing, cloud technologies, virtualization, network security, IoT and many more.